Are Virtual Data Rooms (VDRs) Secure?
Secure Virtual Data Room Solutions – are they just Snake Oil?
Secure virtual data room (VDR) systems don’t stop users from sharing documents. Here, we explore the reality of safe data rooms and explain why they are useless for secure document sharing.
- What is a virtual data room or deal room?
- Secure VDR & Virtual Deal Room security
- Is it safe to store sensitive documents in the cloud?
- Popular virtual data rooms (VDRs) and their flaws
- Locklizard as a secure data room alternative
 What is a virtual data room or deal room?
What is a virtual data room or deal room?

A deal room or online data room is a cloud-based solution (browser-based application) that enables users to share and collaborate on information online. They are also called secure cloud collaboration systems. They are marketed at businesses looking to share confidential information, intellectual property, and other sensitive corporate data, and for the sharing of M&A documents during the due diligence process (but also for capital raising, initial public offerings, and other financially sensitive data).
They are sold on their ease of use and ability to create a secure online space — an easy-to-use online secure file-sharing solution that provides data storage with collaboration tools.
Virtual dealrooms have rapidly been adopted by small companies to large corporations but are particularly popular with financial institutions (investment banking, private equity firms, etc.) who had previously used traditional or physical data rooms. They are also popular with legal firms and life science companies for sharing sensitive information and project management.
 Secure VDR & Virtual Deal Room Security
Secure VDR & Virtual Deal Room Security
Some people think that secure data rooms and cloud collaboration systems are a safe way to securely share confidential files and documents. This isn’t surprising – the first thing they tell you when you visit their sites is just how secure they are. Here, we explain why that is not true and why their security features are often just smoke and mirrors.
 Is a secure data room or cloud collaboration system really secure?
Is a secure data room or cloud collaboration system really secure?

Like any marketing term, whether a virtual deal room (VDR) or cloud collaboration system is secure depends on how you define ‘secure’ and whether the parts the VDR provider deems secure match those expectations. There is only one question you need to ask a secure data room provider, though – “Does your system stop users from sharing documents?”
The truthful answer to that question will always be no.
- Authorized users can share their login credentials or links with other non-authorized users and, therefore your documents.
- They can share ‘protected’ documents with unlimited users via online meetings (Microsoft Teams, Google Meet, Zoom, etc.) or via remote desktop access.
- They can also easily bypass security permissions or restrictions to create documents that can be viewed and shared offline. This is because JavaScript can be edited in the browser.
 Secure virtual data rooms: why security is inadequate
Secure virtual data rooms: why security is inadequate

‘Secure’ data rooms make a big thing about how secure their data (server) systems are with terms such as ‘most secure virtual data room’, ‘secure electronic data room’, ‘most secure data room’, ‘highly secure data room’,’ secure virtual deal room or secure VDR’ and ‘safe data room’. They sometimes even target their marketing at processes that their security is unsuitable for, calling themselves an ‘investor data room’, ‘M&A virtual data room’, ‘M&A dealroom’, etc. It is meaningless marketing babble designed to get them search traffic.
Does a secure virtual data room (VDR) prevent document sharing?
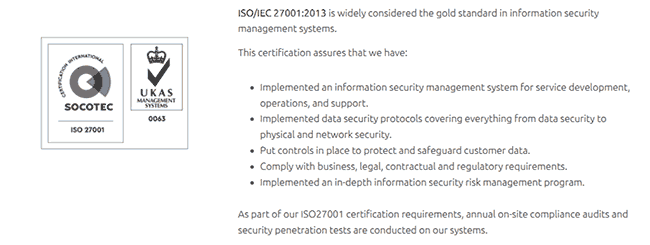
Many secure virtual data rooms or v-rooms, cloud-hosted secure data room, or secure virtual data room providers publish their security credentials and certification credentials on their websites to show you just how secure they are. Something along the lines of:
ISO/IEC 27001:2013 is widely considered the gold standard in information security management systems.
That sounds important and secure, right? Does this mean it stops authorized users from sharing your documents with non-authorized users? Does any claim provided by a safe data room state this? No.
These claims are there to make you believe their systems are fit for purpose (whatever that might be). It is the equivalent of a food manufacturer advertising their 0% fat cereal bar as healthy when it is 80% sugar.
In other words, secure VDRs are not as secure as they might first seem.
Data encryption in data rooms

Secure data room systems claim they are secure because they store your data encrypted at rest on a secure backbone (e.g. AWS-hosted server) that is itself certified. That’s just as well, since if your documents are being decrypted on the server before being delivered to the browser, that could mean thousands of temporary files containing your document content just sitting there in the clear. You would, therefore, hope that the server hosting these could not be readily hacked, as a minimum.
So, encryption of data at rest in a secure data room is important to stop hackers from gaining access to your documents. As the server has regular updates, good protections against malware, etc. But this is just one component of data room security.
 Is it safe to store sensitive documents in the cloud?
Is it safe to store sensitive documents in the cloud?

If you have confidential or sensitive business documents, you might want to question why you would want to upload them to a provider’s dataroom server as unprotected files. Even if they are encrypted, what happens to your original unprotected documents – are they definitely deleted? Are any temporary files left over? How can you verify this?
A more sensible approach would be to not let them leave your computer or domain to begin with – protect documents locally and distribute protected documents as you see fit. This is not what secure data room systems allow you to do.
 Can a secure VDR that relies on a login & password ever be secure?
Can a secure VDR that relies on a login & password ever be secure?

Let’s face it: any system that relies on a manually-entered username and password to stop unauthorized access is not very secure. The objective of using a secure data room is for secure document sharing (i.e., ensuring only specific users can open your documents). Yet, users can share their login credentials with others and, therefore, your documents.
Most secure data room systems don’t even limit how many people can log in with the same credentials simultaneously. User ‘Jo Bloggs’ could be logged in from thirty locations at once, and you would never know. This is especially true if every Jo Bloggs is using the same VPN or proxy IP address.
 Can Two Factor Authentication (2FA) provide foolproof security?
Can Two Factor Authentication (2FA) provide foolproof security?

Some secure virtual data room solutions claim their system stops sharing by using 2FA as an additional security measure. While it is true this might help to prevent users from being hacked, it doesn’t stop authorized users from sharing their credentials. Users can still forward 2FA information to others. Some systems, for example, require users to enter their email address when clicking on a link to a document – they then click on a link sent to that address to gain access. However, they can still give that second link to other users by forwarding the email. The same is true of a PIN or any other form of secondary validation.
A more sensible and secure approach to the login process is locking documents to devices so authorized users cannot share them with others. Unfortunately, this is not achievable in a browser environment, where no software is installed on the client.
 Can document tracking provide accountability?
Can document tracking provide accountability?

Data rooms enable you to track what documents a user has opened and see if it is always from the same IP address. Indeed, the effectiveness of virtual data room software often hinges on its ability to perform such monitoring of user activity.
However, if you have many users using the system, there are large volumes of data to sift through. You are also assuming that only the authorized user has opened those documents. Anybody with those login credentials could have been viewing the files from the beginning. You therefore have no idea who you are actually tracking.
Then there is the IP information and what that relates to. Here, we need to have a quick lesson in browser proxies and VPNs. Most anti-virus software has a proxy installed as standard, enabling users to browse the web securely – just choose your location, and the system will automatically assign a different IP address for you each time. With VPN systems, you can choose a dedicated IP address (or static IP), and multiple users can use the same VPN.
On a different note, many users regularly change IP addresses or share the same IP address with others simultaneously. Switching from Wi-Fi to mobile data changes a user’s IP address, and most home internet connections change IP addresses daily. Clearly, IP tracking cannot be relied upon.
 Are browsers effective in ensuring data security?
Are browsers effective in ensuring data security?

Virtual deal rooms or data rooms and cloud collaboration systems operate in the browser, introducing more problems. Browser environments are notoriously slow (bad luck if you have large or complex documents) and highly insecure.
Browsers were not built with security in mind. Users can easily manipulate code in the browser using third-party plugins, JavaScript, and direct debugging (developer mode). The DRM controls data room providers claim to enforce (usually with JavaScript) could be bypassed without you knowing. For an example of how insecure JavaScript-based browser controls are, see how easy it is to bypass Google Docs security.
In addition, there’s a limit to what you can control – stopping screen grabbing and printing to PDF is not possible.
High Quality Screenshots
Many computer users have screen-capturing applications installed on their devices. These could be dedicated programs like Snag-it or ScreenRec, or even just the built-in Windows Snipping Tool. These free tools are effective in capturing high-quality screenshots of document content. Browser plugins are available (e.g. Fireshot) that automate screen capture of each page, saving it to a single PDF file and AI tools can automate PDF watermark removal. Secure data room systems cannot prevent screen recording software from capturing screenshots since they have limited control over the browser.
Sharing of Documents via Online Meetings
If your goal is to prevent sharing, then stopping users sharing protected documents via online meetings (Microsoft Teams, Google Meet, Zoom, etc.) is an important factor to consider. Cloud collaboration systems that use a browser for document viewing cannot prevent this – it is simple therefore for users to share protected documents with an unlimited number of users. This is also true of the use of remote desktop apps.
Printing to PDF
It is possible that you will need to allow printing for certain documents so that users can have a physical copy. However, if you allow printing from a secure data room system, there is a risk that users may just print to a file driver (such as PDF) instead of a physical printer. This means that any protection on the document will be automatically removed, and the users will have an unprotected PDF document that they can use or share with others as they wish.
 Enabling offline use of documents can compromise data room security
Enabling offline use of documents can compromise data room security

It’s important to acknowledge that not every user has constant internet access. It is reasonable for users to expect to view documents offline when traveling, during outages, etc.
While dataroom solutions prevent download of PDF files to prevent sharing, most secure data room systems let choose whether to allow this. However, the downloaded PDF files are either not protected (e.g. Digify, DocSend, etc.), or are password-protected PDF files – see removing PDF password protection. This raises the question: why use a secure data room solution if you want to allow document downloads when users can download unprotected PDF files that they can share at will.
 Do digital watermarks on documents provide additional security?
Do digital watermarks on documents provide additional security?

Most secure data room systems let you add watermarks to your documents. If, however, you allow users to download PDF files, those watermarks can be easily removed using a PDF Editor such as Adobe Acrobat. This is because they are added as a layer to the PDF file, and that layer can be removed in one go.
With some providers, you may not even need to enable downloads for users to remove or modify watermarks. Some watermarks are applied via JavaScript, which can be manipulated in the browser. Other data room providers allow users to retrieve the unprotected PDF document via their browser’s developer mode even if downloads are disabled. We cover this in more detail in our blog on how to remove watermarks from Google Docs.
Users can also use automated screen capture plugins to capture an entire document to PDF and then use an AI watermark removal app.
Ultimately, digital watermarks for downloaded documents don’t provide additional security, since you can no longer identify the user who shared your documents. With some providers, users may be able to modify or remove the watermark even if you disable downloads.
 Secure Data Rooms usability issues
Secure Data Rooms usability issues

So far, we have just mentioned data room security issues, but some of these systems are so poorly designed that they’re also a struggle to use at scale. For example, if you want to have a PDF file that expires at different times for different users, you must upload the file multiple times (one for each user) or create multiple links to the same file. This quickly becomes unmanageable in a medium to large company. It’s much simpler to use an existing document management system and just have secure PDF files made available in it.
 Popular virtual data rooms (VDRs) and their flaws
Popular virtual data rooms (VDRs) and their flaws

Many customers fall into the trap of thinking that only niche, low-quality virtual data room providers exhibit these security issues. In our testing, though, even the best virtual data room companies are not secure despite positive reviews. Here are four examples of secure dataroom providers and why you might want to consider more secure alternatives for external document sharing.
SecureDocs virtual data room
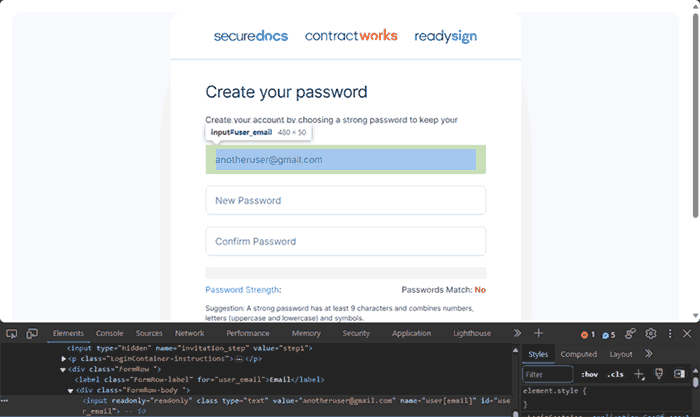
SecureDocs makes a lot of noise about its AWS hosting and data encryption and not much about its other security. This is probably for the best because it has severe flaws in other areas:
- Uses a username and password system like every other data room (and then considers 6 lowercase letters and four numbers a ‘strong password”).
- Does not force 2FA and accepts SMS as a method, which is insecure.
- Allows a user to log in from multiple locations at once (and therefore share an account with as many people as they like).
- No attempt to stop screenshots.
- Displays the document as images, which can be found in the browser’s developer mode and downloaded/shared. These have predictable file names, so downloading every single page is a simple matter.
- Their “personally identifiable” watermarks are easy to modify. Users you invite to the data room can change their name in their account settings. Though they are only supposed to use the email address you provide on signup, they can change this by editing the field in their browser’s developer mode. Combining both of these flaws, they can display whatever watermark they like.
- The exploit above could also be used to create an account under an unauthorized user’s email address.
This is what we found with just a few minutes of digging. SecureDocs virtual data room clearly isn’t going to stop sensitive and confidential documents from being shared.
Cirtrix fileshare (ShareFile)
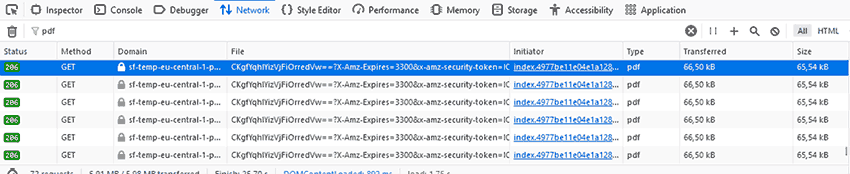
ShareFile (formely Citrix fileshare) tells users that they can confidently share and collaborate without having to sacrifice security. We would re-think that marketing copy given the following issues:
- Users can open the “Network” tab in their Firefox developer mode and find the full, unprotected PDF, which they can download, print, save, etc. They can also upload it to a free PDF password remover so that they can edit it and remove any watermarks.
- Displays files as images, which can be downloaded with a simple “right-click > Open image in new tab”.
- Uses usernames and passwords, which can be shared, does not force 2FA.
- Doesn’t try to prevent screenshots.
- There is no way to enable printing without also allowing editing and downloading.
- Tracking is basic (it only tells you if somebody accesses the link) and at what time.
In other words, ShareFile is an apt name. Anybody who uses this service can expect their sensitive files to be shared widely and freely.
DocSend virtual data room
DocSend’s security isn’t quite as bad as Citrix, but it is incredibly slow to display documents and still exhibits all the other flaws you’d expect from a data room:
- Links to documents or data rooms (spaces) can be shared with other users.
- Email verification links can be shared with others.
- Verification cookies can be edited and used on other devices.
- Multiple users can log in at the same time using the same login credentials.
- If printing is allowed, then users can print to unprotected PDF files.
- Users can take high-quality screenshots of document content using screen grabber tools.
- Downloaded files have NO protection applied to them. If downloads are disabled, tools like Deck2PDF will let users download them anyway.
- Watermarks in downloaded files can be easily removed with PDF editing software.
- Tracking data is for an email address. Since email addresses can be shared with other users, you have no idea who you are actually tracking (users can use a VPN to share the same IP).
- The browser environment provides weak security since it can be easily compromised (i.e. security removed) by plugins, JavaScript, or debugging editors. In fact Docsend to PDF and Deck2PDF provide an online free service which converts DocSend documents to PDF format.
Digify secure data room
Digify exhibits similar flaws to all the others:
- Data room login credentials can be shared with other users.
- Email verification links can be shared with others.
- Multiple users can log in at the same time using the same login credentials.
- If printing is allowed, then users can print to unprotected PDF files.
- Users can take high-quality screenshots of document content using screen grabber tools.
- Downloaded files have NO protection applied to them.
- Watermarks in downloaded files can be easily removed with PDF editing software.
- Tracking data is for an email address. Since email addresses can be shared with other users you have no idea who you are actually tracking (users can use a VPN to share the same IP).
- The browser environment provides weak security – it can be compromised (i.e. security removed) by plugins, JavaScript, or debugging editors.
- Document tracking cannot be turned off – this could be a privacy concern for some users.
You might want to think again if you’re handling sensitive documents with Digify, FileCloud, or any other data room provider for that matter. The moral of the story is not to be fooled by the security credentials and claims branded by secure data rooms – they are mere marketing hype.
 Locklizard as a secure data room alternative
Locklizard as a secure data room alternative

Locklizard provides secure document sharing that actually works. It ensures your documents cannot be shared with others regardless of their location.
Our document security software locks PDF documents to authorized devices so they cannot be shared and enforces the same DRM controls for both online and offline documents.
Our secure PDF Viewers can be installed on Windows, Mac, iOS and Android. They stop screen grabbing and sharing of documents via online meetings, and prevent printing to PDF while preventing watermarks from being removed by PDF editing software.
With Locklizard, there are no login credentials to enter. Keys are transparently managed and securely transmitted. Once received, they are stored encrypted without user intervention so that there is nothing to share.
Compared to secure data room systems, Locklizard provides an extensive range of PDF expiry controls, enabling you to protect a document just once yet limit individual access (different dates) for each user. You protect PDF files on your local computer (no cloud servers involved) and can add protected PDF files to your existing systems like any other file.
We don’t tie you into monthly pricing which can soon add up, offering annual and perpetual licenses. You can choose to host with us or on-premise in your own environment.
Locklizard’s PDF DRM security products enable you to share documents securely regardless of their location, enforcing access and use controls. Stop sharing, piracy, and theft of content by taking a free trial.
 FAQs
FAQs

Is an M&A virtual data room or dealroom more secure than other types of data room?
M&A virtual data rooms, investor data rooms and secure dealrooms, are no more suitable than any other cloud based collaboration solution for hosting sensitive documents. They all allow documents to be shared with others relatively easily. Usually, they are exactly the same as other data rooms but with an M&A marketing spin.
Do secure data room plugins offer better security?
No, secure data room plugins for Google Docs, OneDrive, etc. usually make security worse. They require you to put your trust in third-party plugin providers and navigate the complexities of compatibility while offering no better protection than a regular data room or Google Doc.
Can Locklizard be used with a data room?
You can upload Locklizard’s .pdc files to most data rooms, but there is little reason to. You would not be able to view your Locklizard PDFs in the data room’s browser app and it would not improve security. If you need web access (users to view documents online in their browser), we recommend you instead use the Locklizard web viewer. This is not as secure as the desktop app but provides cloud storage and improved security over many data room providers.
Can you use SharePoint as a data room?
Yes, kind of, though the policy management will be a lot more complex and risk-fraught than your average dataroom, and you won’t get much better security. As outlined in How to make SharePoint secure, Microsoft’s default security must be complemented by a DRM solution for it to be secure.
Is there any desktop-based virtual data room software?
Not as such. Virtual data rooms are defined by their ability to host your files in the cloud and access documents via web clients or browsers. Though a few data room-like solutions such as FileCloud have desktop viewer applications, they’re usually an electron wrapper of the website or have poorly thought-out security.
Are secure virtual data rooms (VDRs) suitable for due diligence/investment banking/healthcare/education?
It depends on the type of data you are processing and the risks you are willing to take. It is quite clear that VDRs will not prevent users from intentionally leaking documents and require additional measures to prevent unintentional leakage via phishing etc.
Can virtual data room reviews be trusted?
Most virtual data room reviews provide positive feedback on how easy the systems are to use for low-volume use. What they tend not to mention are the slow document loading speeds, lack of security (since unless you are looking to bypass this you might think they are secure), how they tend to scale badly – it quickly becomes unwieldy to manage a large number of users and documents, and how monthly costs quickly escalate as your user and document base grows.
Are document collaboration systems more secure than VDRs?
No, they all have the same security issues since they work in the browser. See How secure is Google Docs as an example.

 What is a virtual data room or deal room?
What is a virtual data room or deal room? Secure VDR & Virtual Deal Room Security
Secure VDR & Virtual Deal Room Security Is a secure data room or cloud collaboration system really secure?
Is a secure data room or cloud collaboration system really secure? Secure virtual data rooms: why security is inadequate
Secure virtual data rooms: why security is inadequate Is it safe to store sensitive documents in the cloud?
Is it safe to store sensitive documents in the cloud? Can a secure VDR that relies on a login & password ever be secure?
Can a secure VDR that relies on a login & password ever be secure? Can Two Factor Authentication (2FA) provide foolproof security?
Can Two Factor Authentication (2FA) provide foolproof security? Can document tracking provide accountability?
Can document tracking provide accountability? Are browsers effective in ensuring data security?
Are browsers effective in ensuring data security? Enabling offline use of documents can compromise data room security
Enabling offline use of documents can compromise data room security Do digital watermarks on documents provide additional security?
Do digital watermarks on documents provide additional security? Secure Data Rooms usability issues
Secure Data Rooms usability issues Popular virtual data rooms (VDRs) and their flaws
Popular virtual data rooms (VDRs) and their flaws Locklizard as a secure data room alternative
Locklizard as a secure data room alternative FAQs
FAQs