Document Encryption & DRM Security: Securely encrypt documents
 | An overview of document encryption and why DRM is needed for document control |

 What is document encryption?
What is document encryption?
Document encryption is the process by which documents are protected with cryptographic keys (a password, public key, token, etc.) so that only individuals with the corresponding decryption keys can open them. It is used to protect documents in transit (i.e. sent via email) and at rest (i.e. stored on a disk or in the cloud) from being accessed by unauthorized users.
 Document encryption software
Document encryption software
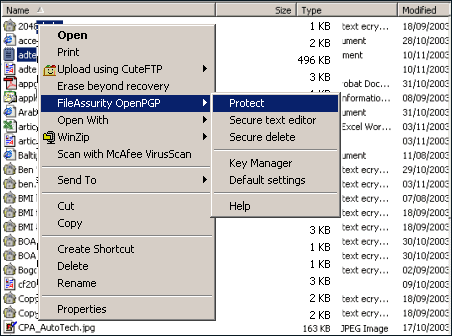
Document encryption software can either be:
- standalone file encryption applications (like PGP, which encrypts any files and not just documents)
- plugins to certain applications like Microsoft Office/Word or Adobe Acrobat which enable documents to be encrypted when they are saved to disk
- online tools that enable you to upload documents and encrypt them on a cloud server
Not all document encryption is equal. Whilst most document encryption programs provide NIST-approved AES encryption, they vary with their protection methods – some provide password protection, some use hardware tokens, and others provide public key technology (PKI). Each scheme has its own pros and cons – passwords can be given away (and are often weak and therefore easily broken), tokens have to be distributed and maintained, and public key technology has to have a management hierarchy.
For further information on Adobe Acrobat encryption, see:
 Why encrypt documents?
Why encrypt documents?

According to some politicians, if you have nothing to be worried about then you don’t need encryption! Strange. Historically, there were five groups of people who wanted encrypted documents:
- Purveyors (traders)
- Princes (the military)
- Politicians (diplomats)
- Paramours (lovers)
- Popes
Unlikely though it may seem, purveyors come out top of the list. The earliest preserved writings were sales manifests on baked clay tablets, and early cryptographic documents included a recipe for pottery glaze. So maybe trade is the most important thing of all? Consider – the famous Enigma machine was first used in commerce before being taken up by the military. So, it is important to preserve commercial activity, and there is a lot more of that than all the others. It’s just so much less exciting.
You don’t need a lot of imagination to figure out that each group must have had information they want to share, but only with carefully selected people and not always on the same basis for each recipient. And you can also figure out that they would want to be sure that the information did not get into the wrong hands, was not changed or misrepresented, and could maybe be denied if necessary. And that is just what an encrypted file provides.
Encryption is the most valuable tool supporting our most common security requirements for internet-based transactions and communication. TLS (Transport Layer Security) relies on encryption to provide secure communications such as encrypted email and secure instant messaging. SSL encryption is ubiquitous for protecting information as it races around the networks from tablet to bank to merchant, or to anywhere else for that matter. Because of that, internet trade is underpinned by something that makes it all tick.
Document encryption isn’t just useful – it’s the essential technology for securing documents in today’s society on the onternet.
But here’s the rub:
 Document encryption – the downside
Document encryption – the downside

Encryption works just fine if you can maintain an encryption key register – just like you do an email address book. That’s easy to say but evidently not so easy to do, otherwise the email suppliers would have cracked this one years ago.
There are two big problems with encryption that are difficult to solve. The first is that you need the keys of all the people you might want to send secret information to. And the second is that when they get the secret information from you, they can do just what they want with it.
Encrypted documents work splendidly when they’re in transit and at rest (stored on a device). The issue, however, is that the recipient can give the crown jewels to the enemy (either the encrypted document with the corresponding decryption key, or the decrypted document) and you can’t do anything about it. So, document encryption is the starting point, but it needs more functionality if it’s going to give you full document control.
As mentioned earlier, there can be a big management problem looking after and protecting all the cryptographic keys involved in the encryption process. The solution to this is a management system that is based upon both users and documents, and that manages all the keys secretly – actively preventing the users from getting involved in a complicated system that can all too easily go wrong.
Ultimately, although we need encryption to protect a document while it travels around the network or sits on a hard drive somewhere, we also need ways of controlling what can be done with the content once the document has been opened – and that can be achieved with Digital Rights Management (DRM).
 | Document DRM – encrypt documents & enforce document restrictions |

DRM has to be both available to the application using the document, and implemented in it by design so that weaknesses are not exposed.
Computer applications (apart from those doing encryption) were usually not designed with document security control in mind – mostly they were designed to get to market as rapidly as possible while allowing quick and easy document copying. Another consideration was speed of operation. Complex application packages are large and use a lot of processing, usually rendering images onto the screen or manipulating large data in memory or on disk (where they would make uncontrolled copies of the documents to speed up performance).
This makes things difficult for document DRM providers, as they are obliged to either find some way of bootstrapping themselves into the applications, or use Systems Development Kits (SDKs) and handle the business functionality themselves. Naturally, both methodologies have been used.
Bootstrapping yourself into someone’s application works in one of two ways. You can either reverse engineer into the application (difficult and may cause litigation in some jurisdictions) or, if the manufacturer allows it, plug-in to their functionality (usually requires a licensing deal, which can be quite complex).
Both of these approaches present problems. If you have reverse engineered into an application and the applications provider changes anything, what you are doing will probably cease working immediately. The same applies to plug-ins, where the locations will likely change, again meaning that everything stops working. This will likely leave your customers very unhappy.
There are also problems for these types of implementations if document locations within the data storage of the application change, and it can be difficult to maintain security/integrity if new unencrypted copies of the document are created by the application, even as temporary files.
A more secure approach to implementing DRM controls into applications is to develop a custom DRM application using appropriate Software Development Kits (SDK). There are many reasons why this is a more secure and reliable approach.
If you plug in to another architecture, you face the problem of trying to prevent users accessing commands. For instance, in Microsoft Word, after highlighting some text you can copy it using Alt + E + C, Ctrl + C or using the appropriate mouse clicks. You can also “Save As” a document using Alt + F + A or using the toolbar. Using an SDK instead allows the DRM provider to determine what functionality they are going to support and how it is being implemented. They can be sure that there are no unencrypted copies of files created or left on hard drives, that memory used for decryption is not transferred to a swap file, and control how text and images are rendered to the screen (some systems send text as text and others as graphics – which is more difficult to copy back to text). The DRM provider can even not implement certain functionality such as editing so that there is no way to enable it.
Another advantage of using an SDK is improved stability. Product manufacturers are continuously making changes to their products, and according to Gilb’s hypothesis (on unreliability), every time a bug is fixed the fix creates one new bug that can be found and one that likely cannot. This may not be strictly accurate, but it’s true that from a security standpoint, the more changes that are made, the more new bugs are introduced. Unless there is a security reason to make a change (say it stops working) it is more reliable for users not to have updates, or, if you must, alter the smallest system where you will do the least damage.
This may sound negative, but consider that the PGP encryption system is well known and widely implemented, and very stable and reliable. It is also very small, with limited functionality. And that is why it is so successful. Though new functionality is exciting, the more systems that interact with a tried and tested security mechanism, the more vulnerable it tends to become.
 | How to encrypt a document using Locklizard Safeguard |
Though it is more effective than standard encryption, creating a encrypted file with Locklizard is no harder. The process takes less than a minute:
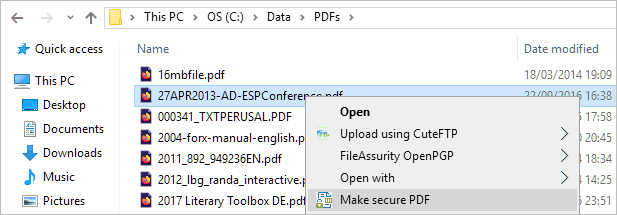
- Right-click on a PDF file on your desktop and select “Make secure PDF”.
%22%20transform%3D%22translate(1.2%201.2)%20scale(2.41016)%22%20fill%3D%22%23fff%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-.5809%2027.73216%20-106.81608%20-2.23748%20197.3%200)%22%2F%3E%3Cellipse%20rx%3D%2246%22%20ry%3D%2230%22%2F%3E%3Cellipse%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(84.31433%2010.80091%20-3.55798%2027.77434%20176%200)%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
- Protect the PDF from copying by ticking the relevant controls. We recommend that you add a watermark to discourage sharing. Safeguard creates permanent dynamic watermarks that identify users and their devices.
%27%20fill-opacity%3D%27.5%27%3E%3Cellipse%20fill%3D%22%2341a4f3%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-487.06174%201.99374%20-.1896%20-46.31965%20307.5%205.3)%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-339.63112%20147.02746%20-81.37559%20-187.97633%20311.5%20343.2)%22%2F%3E%3Cellipse%20fill%3D%22%23d2d0cf%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(48.50184%20-131.82415%2081.24637%2029.89284%2072.8%20153.5)%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
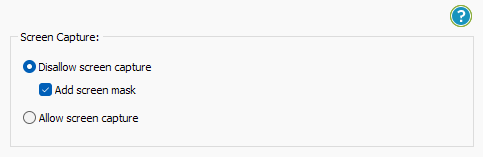
- Locklizard PDF will automatically protect a PDF reader from copying text and images, but you may want to take additional steps to protect your PDF from screen capture. Without screen capture protection, a user can screengrab your PDF and import it into an optical character recognition tool to make the text editable. To prevent this, open the “Environment Controls” tab and tick “Disallow screen capture” and optionally “Add screen mask” which covers the viewer window with an image if focus is moved away from it.
%22%20transform%3D%22translate(1%201)%20scale(1.88672)%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20fill%3D%22%23cacaca%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22rotate(76.5%20-20%2045)%20scale(59.50181%2038.8711)%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20cx%3D%22161%22%20cy%3D%2259%22%20rx%3D%2295%22%20ry%3D%2295%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20cx%3D%22157%22%20cy%3D%2246%22%20rx%3D%2290%22%20ry%3D%2290%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
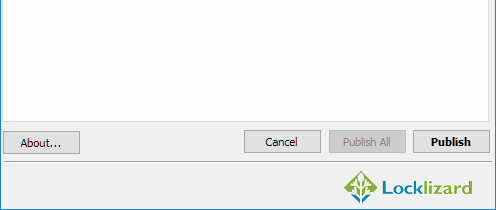
- Press the “Publish” button at the bottom of the dialog.
%27%20fill-opacity%3D%27.5%27%3E%3Cellipse%20fill%3D%22%23d1d1d1%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22rotate(168.9%20164.5%20104.6)%20scale(494.0625%2062.51262)%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(393.1765%20-23.13948%204.63058%2078.68087%20199.7%2040)%22%2F%3E%3Cellipse%20fill%3D%22%23d5d5d5%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-82.79938%20-45.81606%2023.04825%20-41.6531%2025.1%20159.3)%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
Locklizard will automatically protect a PDF from editing on publication for anybody who has access to it. This restriction cannot be bypassed, and as the user cannot make a copy of the document, they won’t be able to clone it and edit that, instead. On publication, your document will output to its source folder in the .pdc file format and you can safely share it knowing that nobody can access it without a valid license.
 | A summary of document encryption and DRM |
Document encryption (preferably using a strong and reliable method such as that used by PGP) is a critical tool for protecting document contents. But it needs to be allied to a DRM system that can enforce a limited set of controls so that document owners can specify what is allowed once the content is decrypted. When the document is decrypted, it should only ever occur in memory so users cannot grab content from temporary files on disk. Document DRM applications should also lock decryption keys to devices so they cannot be readily shared – note that this cannot be achieved if the system uses passwords that are known to the user (since these can be shared with other users).
A document DRM system must itself be compact and reliable if it is going to deliver the expected results and not be effected every time a major application manufacturer makes changes. So, document encryption is the essential building block for document security, but successfully implemented DRM technologies are required to integrate with document encryption and application functionality.
 Further reading on encryption
Further reading on encryption
To learn more about encryption, please take a look at the following white papers.
![]() Introduction to Encryption
Introduction to Encryption
![]() Encryption is not enough for DRM
Encryption is not enough for DRM
![]() Using encryption to Secure Downloads & stop copying
Using encryption to Secure Downloads & stop copying
 | Why Locklizard for Document Encryption? |

US Gov Strength PDF Security – Encrypt documents without passwords
Locklizard takes your document protection seriously – we encrypt PDF documents with US Gov strength AES encryption and use licensing controls and DRM security to control document use.
Our PDF DRM Security products enable you to share documents securely without insecure passwords or plug-ins, and enforce access, location, expiry, and usage controls. You can revoke PDFs at any time regardless of where they are.
Our DRM technology ensures your documents remain safe from copying, sharing, editing, screen grabbing and printing..
Read our customer testimonials and case studies to see why organizations use Locklizard PDF security for secure document sharing and to sell documents securely.









 Free Trial & Demo
Free Trial & Demo What is document encryption?
What is document encryption? Document encryption software
Document encryption software Why encrypt documents?
Why encrypt documents? Document encryption – the downside
Document encryption – the downside


 Further reading on encryption
Further reading on encryption FAQs
FAQs














