
Stop PDF editing, printing, copying. Stop sharing & control use.
 | Common myths about stopping copying, emailing, and downloading |
Stop copying, saving, emailing & downloading files
It is a common myth that you can stop the copying, emailing, and downloading of files. This is not possible in today’s age. What you can stop, however, is the use of content by unlicensed users.
 MYTH 1: You can stop the copying of files
MYTH 1: You can stop the copying of files

Back in the eighties, particularly with the advent of CD-ROM devices, a lot of work was done to try to implement systems that prevented the copying of films and soundtracks. The most successful approaches were probably the Digital Audio Tape (DAT) standard (it failed because the public would not buy a product that did not allow them to copy their own tapes). An attempt to modify the MP-3 standard also failed because it proved unworkable.
Despite what people say or think, unless hardware is involved, it is not practically possible to stop people from making copies of files, one way or another. You have similar problems with trying to stop people saving files once they have opened them with an application. There are just too many ways to copy files and admins would require too much control over the OS. So, if it is impractical to stop file copying (ask the film industry about this one) what can you do?
The answer is simple – you must encrypt the file and make sure that the application that can decrypt it cannot be used to make an unprotected, uncontrollable version. You can then control who can actually use the file and what they can do with it. It doesn’t stop them from making copies – but it DOES prevent copies from being useful to anybody who is not authorized. When it comes to it, the result is the same – no misuse.
 MYTH 2: You can stop downloading
MYTH 2: You can stop downloading

Stopping the downloading of files is theoretically possible. You could handcraft an application to receive information from a server a line at a time for both printing and displaying text. Not very usable, you might say, but it does minimize caching (just an up-scale version of downloading).
Of course, working that way does create serious performance problems. Searching a document for a given word suddenly becomes unbelievably slow, and everything comes to a halt if you meet a picture or want some fancy font rendering.
This is why the internet uses caching or PDF (and any other) documents use downloads and work with local copies. Anything you view in a browser is downloaded to a temporary folder on your disk and loaded into the browser from there. It’s not that stopping downloading cannot be done, it’s more that we have learned that it simply is not practical, even with today’s apparently huge bandwidths.

Most secure data room systems stop PDF documents from being downloaded by converting your PDF files to images when you upload them – so only raster images are cached locally. However, this provides a poor user experience, since images are slow to display and features such as search, bookmarks, and annotations are unlikely to be available. Images can also be run through OCR recognition tools to turn them back into text.
The answer, then, is not to stop downloading, but to prevent the downloaded file(s) from being useable. Again, this is where encryption comes in to play – preventing unauthorized access.
 MYTH 3: You can stop the emailing of content
MYTH 3: You can stop the emailing of content
Back in the early 2000s, it looked like stopping emailing of content and files might actually be possible. Some manufacturers and corporate IT departments had gotten their acts together and invented email scanning (a bit like anti-virus, but using books of rules) to figure out what should be allowed out of the corporate firewall, and what should not. It might even have worked in the corporate world, but for a couple of inventions along the way. The use of flash (USB) drives suddenly became very popular, but arguably worse, the ‘Bring Your Own Device’ (BYOD) market took off, led by the Blackberry. These devices came with their own email clients, their own network connections inside or outside the firewall, and their own ways of connecting to USB drives. The rest, as they say, is history.
When push comes to shove, the average mobile phone user can get past the most sophisticated security systems there are. Even Gmail’s confidential mode, which forgoes scanning and instead tries to stop users from copying, printing, or downloading the email, doesn’t work and doesn’t add any protection to attachments. And while you can recall emails (learn how to unsend an email in Gmail here) this feature is so limited that it’s rarely useful.
The only way to stop unauthorized access is to make sure that any file you want to protect can only be used by licensed users. They can send and copy the files/emails anyway, so the only option left is to stop the attachment from being used by an unauthorized recipient.
 | How Locklizard DRM Security stops unauthorized use and misuse of Documents |

 Stopping unauthorized access
Stopping unauthorized access
Encryption is not enough to prevent unauthorized use of documents. Once a user has the key to decrypt a document, they are in control of it. This is always the case with password-based systems since the user must know the password in order to enter it.
Locklizard Safeguard uses public key technology (no passwords) with DRM and licensing controls to provide persistent document protection and control regardless of where documents reside. See our DRM Technology.
 Stopping copying of files
Stopping copying of files
Though (as we have covered) users can always copy files, Locklizard makes the copied files useless to unauthorized recipients. This solves the problem by neatly avoiding it.
Locklizard encrypts PDF file(s) into a proprietary format – the PDC file. Unlike encrypted PDF files from other solutions, the start of the encrypted file is random rather than known plaintext. This makes it harder to attack.
The decryption key is also not in the encrypted file, so password-type attacks do not work. Key materials are transported secretly, encrypted, and locked to specific devices. The end user cannot obtain them even if they use any of the SSL-type attacks for disclosing secured content.
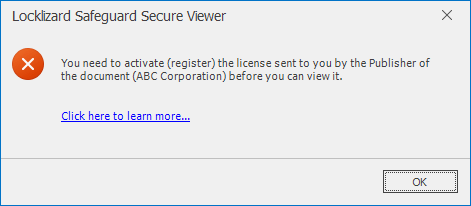
Finally, even if someone else installs a viewer to read a PDC file, they have to register valid a license with a cloud-based server, and this license cannot be reused from another user. The server can identify the devices that have registered valid licenses and will not download decryption keys unless the requesting user passes all tests.
So, although you can copy Locklizard protected files, they are only of any use to people with valid, current licenses to use the protected documents.
 How to prevent copying of file from a USB
How to prevent copying of file from a USB
You cannot effectively stop files from being copied from a USB in a modern work environment. Though theoretically, you could modify the file’s permission to disable read access, this would also stop it from being opened in the intended application, making it useless.
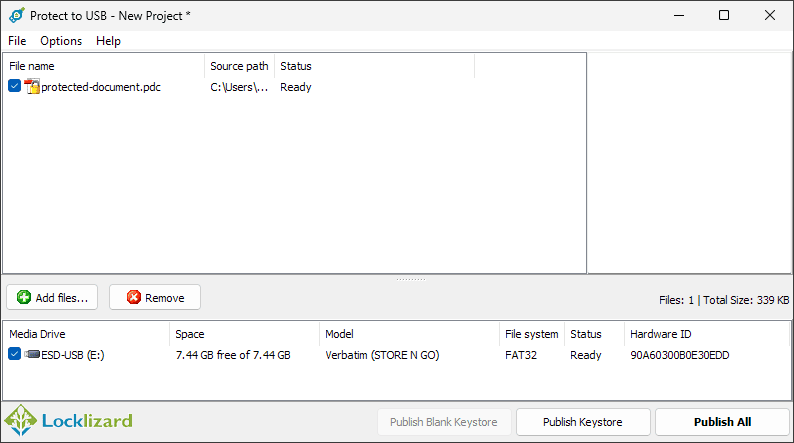
The better option again is to instead control who can open the file and how they can use it via encryption and DRM controls. This makes copying irrelevant, as unauthorized users cannot access the document anyway. Locklizard offers a fully offline USB DRM solution for exactly this purpose.
 Stopping document misuse
Stopping document misuse
Locklizard uses various techniques to prevent documents from being misused by authorized users.
- Documents are locked to devices so they cannot be shared with other users.
- Our Secure Viewer applications do not have Save or Save As functionality in the code (unlike just greying out buttons in a browser) so the user cannot obtain that functionality even if they want to.
- Content is only ever decrypted to memory – no temporary files are used – so there is no exposure of unprotected content.
- DRM controls stop PDF editing, copying and pasting content, as well as screen grabbing and printing.
- You can add dynamic watermarks to viewed and or printed pages to identify users. Dynamic variables (date/time, user name, company name, email address) are replaced with actual user and system data when the protected PDF document is displayed and/or printed.
- Documents can be set to expire so they are no longer available to use after a certain period of time, and you can revoke access instantly anytime, anywhere.
- Documents can be tracked and logged so you can see where they are being used, how often, and when.
- Documents can be locked to locations (e.g. the office) so they cannot be used outside authorized areas.
 | How to prevent PDF sharing, copying, editing & printing with Locklizard DRM security |

Using Locklizard to protect a PDF so it can be sold or shared securely is quick and simple.
Admins secure a PDF file using Safeguard Writer and then add their intended recipients as users in their admin portal. The system will automatically send the end-user an email with their license file and a link to the Safeguard Reader application. The protected PDF file can then be delivered however you like (emailed, downloaded from a web site, etc.), as only authorized users can open it.
Here’s how to prevent PDF file sharing:
- Right-click on a PDF on your desktop and select ‘Make Secure PDF’.
%22%20transform%3D%22translate(1%201)%20scale(2.11719)%22%20fill%3D%22%23fff%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20cx%3D%22224%22%20cy%3D%221%22%20rx%3D%22133%22%20ry%3D%2229%22%2F%3E%3Cellipse%20cx%3D%22244%22%20rx%3D%22138%22%20ry%3D%2230%22%2F%3E%3Cellipse%20cx%3D%2224%22%20cy%3D%223%22%20rx%3D%2229%22%20ry%3D%2216%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
Creating a protected PDF file
- Select the copy protection controls you want to apply. By default, editing, copy & paste (copying of text & images), and printing of the document are disabled.
%27%20fill-opacity%3D%27.5%27%3E%3Cellipse%20fill%3D%22%235194ca%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(508.06451%20-1.40545%20.14966%2054.10264%20291.4%205.5)%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-306.52329%20137.1145%20-92.6746%20-207.17664%20296.5%20351.9)%22%2F%3E%3Cellipse%20fill%3D%22%23d5d2cf%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22rotate(172.3%20177.7%20320.7)%20scale(483.63947%2056.22878)%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
Encrypting a PDF without passwords using Safeguard PDF DRM
- Press the Publish button to protect the PDF.
- Select the users you want to give access to your secure PDF file using the cloud-based Admin System.
%27%20fill-opacity%3D%27.5%27%3E%3Cellipse%20fill%3D%22%2355c4df%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22rotate(90.2%20107.3%20141)%20scale(43.64149%20572.09553)%22%2F%3E%3Cpath%20fill%3D%22%23fffffe%22%20fill-opacity%3D%22.5%22%20d%3D%22M-73.4%20560.4l-79.9-346%20412.5-95.2%2079.8%20346z%22%2F%3E%3Cellipse%20fill%3D%22%23d8d2d1%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-12.04925%20-60.99846%20128.61015%20-25.40483%20192%20305.4)%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
Safeguard Admin System
- Distribute your protected PDF just like any other file.
For a more detailed guide see how to add security to a PDF.
 | Why Locklizard for Document Security? |
US Gov Strength PDF Security – Secure PDF files without passwords
It is abundantly clear that PDF password protection or password security is not adequate to protect sensitive information or confidential business documents. If you password protect a PDF or other document then it is only a matter of time before it will be shared.
Locklizard however takes your document protection seriously – it is the best way to prevent PDF file sharing and stop editing, copying and printing. Our DRM PDF Security products enable you to share documents securely without insecure passwords or plug-ins and enforce access, location, expiry, and usage controls. You can also revoke PDFs at any time regardless of where they are located.
Our DRM technology ensures your secure PDF files remain safe no matter where your documents reside. See our customer testimonials or read our case studies to see why thousands of organizations use Locklizard PDF security to securely share and sell their documents.









 Free Trial & Demo
Free Trial & Demo Stopping unauthorized access
Stopping unauthorized access Stopping copying of files
Stopping copying of files How to prevent copying of file from a USB
How to prevent copying of file from a USB Stopping document misuse
Stopping document misuse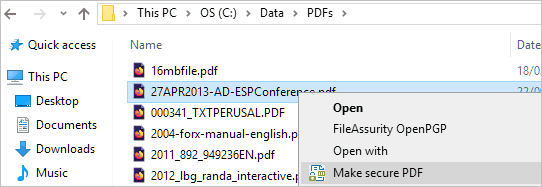


 FAQs
FAQs














