What is DRM? How protection works & DRM protected content
 What is DRM or Digital Rights Management?
What is DRM or Digital Rights Management?
DRM protection meaning or definition
DRM is an acronym for Digital Rights Management, a term used to describe the technology that controls or restricts how content can be accessed and used.

Digital Rights Management solutions use multiple security technologies to prevent unauthorized access and restrict use. These include:
- Encryption to prevent unauthorized access
- DRM restrictions to prevent unauthorized use – copying, printing, editing, etc.
- A licensing system to manage access and permissions
- Control over Operating System functionality or the environment (i.e. a browser)
- Additional security functionality to help prevent illegal use – e.g. watermarks
 DRM software and solutions
DRM software and solutions

DRM solutions are software applications or apps that protect and control access to and use of valuable digital content, such as music, video, games, documents, reports and ebooks. Many document DRM solutions are implemented as online systems or cloud-based solutions where users login to a portal to view DRM protected content. Examples of this are secure data rooms and Google Docs. However, their security is woefully lacking with protection that is simple to bypass despite their certifications and claims. For an example of this, see Google Docs security.
Where cloud-based document DRM solutions allow users to download DRM protected content, that content is usually saved as unprotected or password protected PDF files that provide little or no security. Alternatively, companies use JavaScript or PDF DRM plugins to enforce protection, opening up users computers to malicious attacks or compromise.
A secure document DRM system will not rely on the browser, JavaScript or plugins to enforce security because they have many weaknesses. Instead, it will use a third-party viewer app to enforce encryption, licensing controls and DRM restrictions, and lock use to authorized devices and locations to prevent copying and sharing.
 What is DRM protected?
What is DRM protected?
DRM protected refers to any file that has DRM restrictions or controls applied to it to prevent copying, editing, and unauthorized distribution of digital content.
DRM protected files are also encrypted to prevent unauthorized access, and a license key is used to authorize access and permissions.

To access DRM protected or restricted content you need a valid license key, the appropriate decyrption key, and software or hardware that can decrypt and apply the DRM controls.
 What are Digital Rights Management restrictions?
What are Digital Rights Management restrictions?
Digital Rights Management restrictions enable publishers or creators to control what authorized users can do with protected content.

Such restrictions or permissions include:
- Preventing editing and modification
- Prevent saving to unprotected formats
- Preventing forwarding and sharing
- Preventing printing (or limiting the number of prints available)
- Preventing screenshots or screen grabbing
- Document expiry
- Revoking access
- Locking documents to devices, IP addresses, and country locations
- Watermarking documents with unique user information to establish an identity
In addition, Digital Rights Management systems let content creators track and log use so they can view analytics data on when digital content was used (i.e. when documents were viewed and printed), by whom, and when.
 How does DRM work?
How does DRM work?
DRM works by using multiple security technologies & applications to control access to and use of content. These include an app to protect content, a license server to manage rights, and an app to view DRM protected content.
 DRM protection, protected content, license & software applications
DRM protection, protected content, license & software applications
Protection of Digital Content

To apply Digital Rights Management controls to content (to create DRM protected content), content owners use a protection application. This encrypts the content so it can only be viewed by someone with the correct decryption key (see document encryption), and lets you choose which DRM controls to apply (i.e. preventing printing or making the content expire after a period of time). The protection app could be software installed on a device, or an online service solution where content is uploaded to a cloud server before being protected.
DRM License Server & Key Management

A DRM license or DRM key ties a user to a specific account on a DRM license server (also known as a DRM server, rights manager or rights manager server) and provides control over the content they can access. Users have to enter a license key or click on a link to activate their license which is then locked to the device.
The DRM license server is used:
- for authentication purposes – authenticating users and devices
- to email users their license keys and/or access information
- to authorize the number of devices allowed
- to record IP and device information so content can be locked to devices and locations
- to control ongoing access and permissions
- to transparently relay decryption keys to the Viewer application which enforces the DRM restrictions. With an installed viewer, these keys are locked to authorized devices so that they cannot be shared with other users. Decryption keys must not be exposed to users (i.e. passwords) and must be locked to devices so they will not work on other devices, otherwise they could be given to other users along with the protected content.
Viewing DRM Protected Content

The Viewer application checks that it has the necessary decryption key to decrypt the content, and if it does, it loads the content with the appropriate DRM controls applied. If the Viewer application does not have the correct decryption key(s) it will check with the DRM server to see if the user is allowed access to the protected content. Additional checks are made to the DRM license server as and when required, such as checking for new access rights.
DRM protected content can be viewed in a number of ways:
- DRM Plugin Software. Users can view protected digital content in a native application by installing a plugin (common for browser applications and music/movies). Plug-ins however, have an inherent security weakness in that other plugins can be used to bypass restrictions, and updates to the native application can render them useless – see PDF DRM Plugin.
- Installed Software App. Standalone Viewer, Reader, or Player applications are the most reliable and secure since you have control over the Operating System environment. However, users must download an application to process the protected content.
- Browser Viewer. Enforcing digital rights management in a browser (cloud-based DRM) is becoming increasingly common. But web-based readers have their drawbacks, such as slowness and multiple security weaknesses. Since no software is installed on the client computer, some facilities that take control over the Operating System are not available, so users can screenshot digital content using screen grabber apps and print to unprotected formats (PDF, XPS, etc.) if printing is allowed. Browser-based viewers are also easy to manipulate with script injections and plugins, which can bypass security controls. Document loading times, searching and scrolling all take longer over the web. A classic example of a cloud based DRM system using a Web Viewer is a secure data room – see why dataroom security is NOT adequate for secure document sharing.
 Online DRM or Always on DRM vs Offline DRM
Online DRM or Always on DRM vs Offline DRM
Permission to access DRM protected content and its continued use can be revoked, and rights or restrictions changed on-the-fly. When this is enforced depends on when the DRM device connects to the license server.

Always on DRM or online DRM
Always on DRM, or online DRM, requires a permanent internet connection so that license and access controls can be constantly checked against the license server. Content cannot be used if an internet connection is unavailable or if the rights management server is down.
Always on DRM is popular for music, gaming, and video services where content is streamed online.
Offline DRM
Offline DRM allows content to be used without enforcing an internet connection. In this case, a check is made against the license server when the content is first accessed to download the decryption key and controls, and after that connection, content can be used offline.
Offline DRM is popular for e-books, training courses, etc. where users have purchased a perpetual license to use content and require use in situations where an internet connection may not be readily available (i.e. the beach, a plane, etc.).
Online vs offline DRM
Choosing whether to enforce online DRM is a business decision where the user requirement must be taken into account together with the media you distribute and the controls you wish to have available. For instance, you cannot revoke an offline document once it is distributed.
Locklizard provide both online and offline DRM software solutions. Content owners can specify how long a user can remain offline without requiring to connect to the license server or to connect once only. Locklizard also provide a fully offline DRM solution where content is protected to USB sticks and no server connection is ever required to view protected documents. Our offline DRM provides the same security as online solutions so there is no reason to force users to be online unless you want instant revocation.
 What is DRM Software?
What is DRM Software?
DRM software is software that is used to restrict how content can be used in order to prevent digital piracy. This may be a DRM plugin to an application, a standalone app that may or may not work with hardware, or software such as JavaScript that is used to restrict use within a browser (cloud-based DRM system). Plug-ins and JavaScript are not a particularly secure way to enforce DRM restrictions since there are multiple ways users can bypass their protection or security controls and they can put users systems at risk from malicious code execution.
DRM software prevents unauthorized users from gaining access to content by implementing security controls. It ensures that only authorized individuals can access and view protected DRM content, controls what they can do with it, and how long they can access or view it. This helps protect valuable digital content from being copied, shared, or accessed by unauthorized users.

Even hardware devices use software DRM, which is updated with firmware updates (software code). The use of integrated hardware however enables more control over the operating environment and helps prevent users from bypassing or removing DRM protection.
 DRM Support of Software & Hardware platforms
DRM Support of Software & Hardware platforms
DRM support of both software applications and hardware platforms is becoming more popular due to the increased demand of streaming services, working from home, and paper-free workflows. Microsoft (Xbox), Apple (FairPlay DRM) and Amazon (Amazon DRM for Kindle) are just a few of the major businesses that use both DRM software and hardware to protect their intellectual property and revenue streams, and many hardware devices now read DRM files.
For documents published in PDF format, thousands of publishers use PDF Digital Rights Management software to protect their training courses, reports, confidential documents, and ebooks from unauthorized access and misuse.
Digital Rights Management has come a long way since Sony first protected DVDs with region controls in hardware, and software DRM can now replace much hardware functionality.
 DRM software and single sign-on access integration
DRM software and single sign-on access integration
Because online DRM systems require users to login, most browser-based DRM solutions integrate with single sign-on access, allowing users to access DRM protected content using their existing credentials without the need for additional login information. This also helps to improve security since login credentials can otherwise be easily shared.
For DRM software that uses third-party apps, SSO is not required since there is no additional login beyond the initial authentication to the device. Online DRM systems therefore require additional work to make authentication more secure and seamless to users.
 DRM APIs
DRM APIs
Most DRM solutions provide APIs so companies can integrate document protection with various systems, including websites, content management systems (CMS), e-commerce systems, learning management systems (LMS), and customer relationship management systems (CRM).
APIs automate commands, such as the adding of users, assigning of access rights, etc. so that these tasks do not have to be done manually.
 Advantages / Disadvantages of DRM software implementations
Advantages / Disadvantages of DRM software implementations
Here we cover the different types of DRM software implementations and which DRM software is best for protecting documents and ebooks.
 Cloud-based DRM software
Cloud-based DRM software

Software that is hosted and runs in the cloud. For example, online portals and document collaboration systems, secure data rooms, etc.
Advantages:
- Simple to use.
- Users don’t have to install any software on a device.
- Can be used with any Operating System.
Disadvantages:
- Poor security – users can share login credentials so does not prevent sharing, does not prevent screenshot utilities, downloadable files are either not protected or poorly protected, DRM restrictions can be removed using plugins or scripts (for example Docsend to PDF), files are uploaded unprotected to a web server or unprotected on the web server to convert to image files so could easily be compromised.
- Slow – files are displayed as images in the browser which can result in slow loads times, especially for large documents.
- Users have to be online to view files unless download is made available which weakens security.
 DRM plugins
DRM plugins

Software that is installed as a plugin to a host application (e.g. Adobe Acrobat) to add specific functionality.
Advantages:
- Works with a native application that users may already be familiar with.
Disadvantages:
- Poor security – DRM restrictions can be removed using plugins or fail to function correctly after the host application is updated, poorly designed plugins may put users systems at risk.
- Troublesome – plugins often conflict and can stop working after host updates.
- Users have to install software.
 JavaScript
JavaScript
JavaScript is used by cloud-based document DRM systems to block certain functionality (e.g. printing, copying, etc.) and some DRM companies also use it to control access to downloadable files.
Advantages:
- None from a user’s perspective.
Disadvantages:
- Poor security – can be modified or removed using third party scripts and plugins.
- Dangerous – can put user’s systems at risk from malicious code execution as this is typically done using JavaScript.
 DRM installed app or Viewer software
DRM installed app or Viewer software

This is an app that is installed on a device. The best DRM software apps have been built from the ground up with security in mind rather than adding DRM restrictions to an existing app (i.e. Kindle DRM) as an afterthought.
Advantages:
- Strong security – can lock use to devices so documents cannot be shared unless the physical device is shared, prevents screenshot utilities, tracking is more accurate since you are tracking a device rather than login credentials which can be shared, no useless passwords or JavaScript.
- Transparent authentication and key management – users don’t have to login to yet another system.
- Offline files have the same security as online ones.
Disadvantages:
- Users have to install software.
 Which is the best DRM software for security?
Which is the best DRM software for security?

The best DRM software from a security perspective is an installed app. This is because:
- Files are never exposed unprotected in the cloud.
- DRM protected content can be locked to devices to prevent sharing.
- Unlike plugins and browser apps, installed apps have full control over the Operating System and can therefore prevent screenshots, printing to file drivers (i.e. unprotected PDF files) and lock content to physical devices.
 Why is Digital Rights Management used?
Why is Digital Rights Management used?
Digital Rights Management is used to prevent unauthorized users accessing content and to control what authorized users can do with it. It ensures the owner, author or publisher of a work can prevent piracy or illegal sharing, enforce their copyright, and exert controls that limit what a recipient is entitled to do with it.
 DRM in the Publishing Industry
DRM in the Publishing Industry
Traditionally, in the print publishing industry, the author (or publisher) of a book asserts their right to be able to control what the purchaser can (or cannot) do after they purchase the work. This typically takes the form of a copyright claim on the first page.

However, there has been a major power shift in publishing due to digital transformation. Previously, copying and re-printing a physical book was non-trivial – if you wanted to steal someone else’s work you needed to find someone willing to publish the copy, and the publisher knew they would be sued without mercy. There were some really obvious physical controls in the physical print industry that could not be overcome on a mass scale.
But the digital age has changed all that. Suddenly, computers can make copies at near-zero cost, and do so without detection. The rules of the ancient world no longer apply. The use of websites to facilitate the sharing of pirated films, music, and PDF documents demonstrates that works that do not have digital rights management applied can be copied an unlimited number of times. Files can be shared and transmitted without any control at all. Even print documents are threatened, with users able to scan a document, turn it into a PDF, and distribute it digitally.
Content is the lifeline of the media and publishing industry. Protecting this content is pivotal in safeguarding their revenue streams. DRM software enables media and publishing companies to control access to and use of their content by implementing different content and user controls for different user groups. This flexibility allows them to charge varying fees, such as lower fees for view-only access on a single device and higher premium fees for accessing content on multiple devices. Publishing companies can ensure that ebooks and other materials can be locked to authorized devices, and cannot be illegally shared or distributed, copied, edited, printed or used beyond a certain time-frame. Implementing DRM solutions empowers media and publishing firms to combat piracy, prevent unauthorized access, and monetize their revenue-generating content more effectively.
So, digital rights management is a critical feature if you are making confidential information available to others – whether it is a price list, a contract specification, an analyst’s report, a newsletter, or a book. Without DRM, you have no way of preventing people who have access to your intellectual property from doing whatever they like with it. DRM software lets authors and publishers exert more appropriate digital rights over content than they were able to in the physical print era. This is why most publishers across various industries will use DRM to protect their intellectual property.
 DRM for Standards organizations
DRM for Standards organizations

Standards organizations can safeguard their revenue-generating content by utilizing DRM (Digital Rights Management) software. This enables them to protect their valuable documents by encrypting them and making them exclusive to authorized users who have paid for access.
One of the key features of DRM software is its ability to control content distribution. By implementing digital rights restrictions (that prevent sharing, printing, and copying of materials), associations can ensure that only paying members or subscribers can access and view the content. DRM prevents unauthorized distribution and protects an organization’s revenue streams.
Another important aspect of DRM software is the ability to automatically revoke access once a membership or subscription ends. This ensures that individuals who are no longer current members or subscribers cannot continue to access the content, further safeguarding the organization’s revenue.
Furthermore, DRM solutions provide standards organizations with the flexibility to introduce multi-tiered subscription plans to maximize revenue. For example, they can offer different levels of access based on the subscription package. This could include lower-cost options with limited access, such as view-only access with no printing capabilities, and premium options that provide more extensive access privileges, including the ability to access content on multiple devices and unlimited printing. By offering these premium options, organizations can upsell their existing members or subscribers and generate additional revenue.
In summary, DRM software is a crucial tool for standards organizations to protect their revenue-generating content. It ensures that only authorized users have access to the materials, offers control over content distribution, enables access revocation, and allows for the introduction of multi-tiered subscription plans to optimize revenue.
 DRM for financial services institutions
DRM for financial services institutions

Financial services institutions, including asset management companies, hedge funds, insurance companies, private equity firms, and other investment management organizations, have a crucial responsibility to safeguard the interests of their clients, shareholders, and themselves. The ever-increasing number of data breaches highlights the relentless pursuit of unauthorized users to gain access to sensitive information. Therefore, it is imperative for these institutions to adopt a robust DRM (Digital Rights Management) solution to protect their clients’ information effectively.
To truly protect clients’ information, traditional online solutions like secure data rooms, which primarily secure the access portals or platforms, fall short. These solutions do not offer adequate protection as simple workarounds leave files vulnerable to unauthorized use or dissemination. In contrast, an effective DRM solution that is not browser-based, ensures comprehensive protection for individual files or documents, regardless of their storage location or method.
By implementing a strong DRM solution, financial services institutions can mitigate the risks of reputational damage and financial losses resulting from unauthorized access or sharing of content. Such a solution provides encryption and access control measures that prevent unauthorized users from accessing or using the files, even if they manage to acquire them. By employing sophisticated encryption, permissions (restricting printing, copying, or modifying) and tranparent licensing technologies, DRM software installed on a device ensures that downloaded files remain protected and inaccessible to unauthorized individuals.
Moreover, a good DRM solution enables institutions to track and monitor file usage, ensure compliance with regulatory requirements, and safeguard against internal breaches to further enhance data security.
By protecting clients’ information using an effective DRM solution, financial services institutions not only fulfil their fiduciary duty but also inspire trust among clients and shareholders. Implementing the best DRM solution available minimizes the likelihood of content leakage or sharing with unauthorized parties. Thus, financial institutions can be confident that their clients’ information remains confidential, safeguarding their reputation and bottom line.
In summary, by investing in a comprehensive DRM solution, financial services institutions can ensure the protection of individual files, regardless of where they are stored or saved, and mitigate the risks associated with data breaches. This approach demonstrates a commitment to both their clients’ interests and regulatory compliance, strengthening the institution’s reputation and profitability.
 Market research and data intelligence companies
Market research and data intelligence companies

Market research and data intelligence companies can effectively safeguard their valuable intellectual property by implementing a comprehensive Digital Rights Management (DRM) solution. Since digital information is easily shared and leaked, it is crucial to take proactive measures to protect the countless hours put into performing market research across various industry sectors such as commodities, oil and gas, medical, pharmaceutical, and technology.
By integrating DRM software, these companies can ensure that their reports, price sheets, forecasts, and other research materials are safeguarded from unauthorized distribution and access. DRM technology provides a range of measures and controls to prevent unauthorized sharing, copying, editing, printing and accessing of valuable content without proper authorization or subscription.
One of the primary ways DRM protects market research intellectual property is through encryption. By encrypting research files, it becomes significantly more challenging for unauthorized parties to access or use the content without the appropriate permissions or credentials. Encryption helps in maintaining the confidentiality and integrity of the research data, ensuring that it remains usable only by those who have the necessary rights.
Furthermore, DRM solutions provide robust access controls and user authentication mechanisms with locking of content to devices and locations. This allows market research companies to limit access to their valuable content only to authorized individuals or subscribers. By implementing device authentication, DRM software ensures that only those who have paid for the content or subscribed to the service can access and benefit from the research materials.
Another critical feature of DRM software is the ability to track and monitor the use of protected content. With usage tracking, market research companies can gain insights into how their content is being utilized. It is therefore especially important that the DRM system can lock use to devices so you can ensure that you are tracking a specific user rather than anyone with access who has access to the login credentials for an online system.
Implementing DRM software also enables market research companies to integrate dynamic digital watermarking. Dynamic watermarking adds a unique identifier to each piece of content, making it easier to trace the source of any leaks or unauthorized distribution. This serves as a deterrent and allows for swift identification and legal action against any party found to have violated the intellectual property rights.
In conclusion, market research and data intelligence companies can safeguard their valuable intellectual property by implementing a comprehensive DRM solution. By utilizing encryption, access controls, device authentication, usage tracking, and dynamic watermarking, these companies can effectively protect their research materials from unauthorized distribution and ensure that their countless hours of hard work do not go to waste. Implementing DRM is a critical step in safeguarding valuable research information, enforcing payment for content, and maintaining a competitive edge.
 Associations & Professional Training Organizations
Associations & Professional Training Organizations

Associations and professional training organizations often need to securely send documents and share training materials securely with their members and trainees, ensuring that only paid members are entitled to view materials.
DRM also provides associations and professional training organizations with additional benefits over content use, such as automatic expiry of old content, document tracking to see who has viewed and printed materials (assuming printing rights have been granted), and instant revocation of users and content. Tracking, expiry and revocation can be all be enforced for documents downloaded to a device.
By utilizing DRM software, these organizations can easily protect their valuable teaching materials from unauthorized sharing and distribution, and integrate them with their existing association management systems or learning management systems.
 What other businesses use Digital Rights Management?
What other businesses use Digital Rights Management?

Above are just a few examples of industries that can greatly benefit from DRM software. However, the versatility and adaptability of DRM solutions make it applicable to many other sectors that deal with valuable digital assets and content security.
- DRM protection is used by a number of industries to control the use of paid digital content.
It is popular in the digital music (Spotify, Apple, etc.), movie streaming (Netflix, Amazon, etc.), DVD (blu-ray), gaming (Steam, Xbox, Sony, etc.), and ebook industries (Kitaboo, Amazon, etc.) to control digital content distribution, prevent unauthorized use, and protect revenue streams.
Whilst many end-users paying a few dollars for a song, movie, or ebook, are against the use of DRM, it is more readily acceptable in the business world, protecting high-value reports and content available to members only. This is because if someone has paid $1000 for a report, they would not necessarily be happy if other users were to receive the same document for free.
- DRM is used by companies internally to protect confidential information or sensitive information, share documents securely with third parties, and track document use to identify leaks.
DRM within an organization is also known as Enterprise Rights Management or Information Rights Management. Some online systems where document controls and access can be altered in real-time are sometimes referred to as Active Rights Management systems, but essentially they are all the same thing.
If you want to lock a Google Doc to stop sharing, protect a Word document from editing and copying, prevent ebook piracy, make a PDF non editable or add a watermark to a PDF that cannot be removed, then only DRM software can achieve this.
 What are the benefits of Digital Rights Management?
What are the benefits of Digital Rights Management?
Publishers can employ these restrictions and controls to not just protect their revenue and prevent illegal activity, but enable new forms of content distribution.

Some of the benefits of digital rights management for documents include:
Subscription licensing
The ability to ‘rent’ or ‘loan’, or provide subscription content to users at a lower price than a lifetime purchase. Publishers can expire a user’s access after a certain date or when a subscription is not paid without them being able to easily bypass it. This system provides users with more affordable pricing and publishers with a new, steady revenue stream.
Revenue protection
Increased revenue through anti-piracy and sharing mechanisms. Drastically reducing publishing costs without seriously losing revenue and gain access to significantly larger potential global markets than before.
Copyright enforcement
Clearly state and enforce your copyright through a combination of irremovable dynamic watermarks and copy protection measures.
Data Leakage prevention
Prevent documents from being leaked before publication by restricting them to specific start dates, specific devices, IP addresses, and locations.
Distribution control
Stop ebooks from being accessed in specific countries (such as those with differing distribution rights) or prevent employees or third parties accessing content outside of authorized locations.
Compliance
Stay compliant by proving proof of the use of documents, and enforce document retention policies.
Tracking use
Analyze customer use to see what content they have viewed and/or printed.
All of these benefits make an effective DRM solution or software well worth the investment for most publishers and companies.
 | How to DRM protect PDF files |
How to protect a document or e-book with Locklizard DRM protection
Safeguard DRM software enables you to securely protect PDF documents on your computer, and you can distribute DRM protected content just like any other file.
- Right-click on a PDF in Windows File Explorer and select “Make secure PDF”.
%22%20transform%3D%22translate(1.2%201.2)%20scale(2.41016)%22%20fill%3D%22%23fff%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-.5809%2027.73216%20-106.81608%20-2.23748%20197.3%200)%22%2F%3E%3Cellipse%20rx%3D%2246%22%20ry%3D%2230%22%2F%3E%3Cellipse%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(84.31433%2010.80091%20-3.55798%2027.77434%20176%200)%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
- Protect the document from unauthorized use by ticking the relevant controls. We recommend that you add a watermark to identify users. Safeguard creates permanent dynamic watermarks that cannot be removed using PDF editing software.
%22%20transform%3D%22translate(1.3%201.3)%20scale(2.57031)%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20fill%3D%22%234b8fc5%22%20cx%3D%2284%22%20cy%3D%227%22%20rx%3D%22194%22%20ry%3D%2215%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-132.31977%2038.04086%20-24.81465%20-86.31426%20103.4%20134.4)%22%2F%3E%3Cellipse%20fill%3D%22%23d4d1cf%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22rotate(82.1%20-70.5%20201.8)%20scale(28.42074%20194)%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
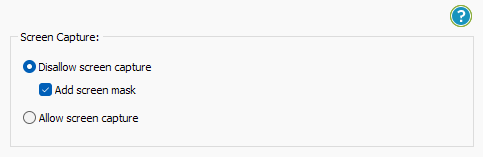
- Locklizard will automatically prevent users from copying text and images, but you may want to take additional steps to protect from screen capture. Without screen capture protection, a user can screengrab your document and import it into an optical character recognition tool to make the text editable. To prevent this, open the “Environment Controls” tab and tick “Disallow screen capture” and optionally “Add screen mask” which covers the viewer window with an image if focus is moved away from it.
%22%20transform%3D%22translate(1%201)%20scale(1.88672)%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20fill%3D%22%23cacaca%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22rotate(76.5%20-20%2045)%20scale(59.50181%2038.8711)%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20cx%3D%22161%22%20cy%3D%2259%22%20rx%3D%2295%22%20ry%3D%2295%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20cx%3D%22157%22%20cy%3D%2246%22%20rx%3D%2290%22%20ry%3D%2290%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
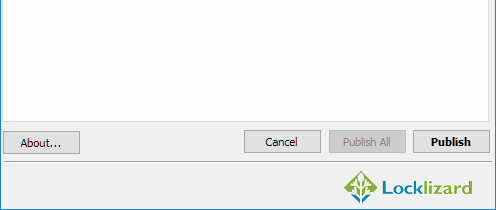
- Press the “Publish” button at the bottom of the window.
%27%20fill-opacity%3D%27.5%27%3E%3Cellipse%20fill%3D%22%23d1d1d1%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22rotate(168.9%20164.5%20104.6)%20scale(494.0625%2062.51262)%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(393.1765%20-23.13948%204.63058%2078.68087%20199.7%2040)%22%2F%3E%3Cellipse%20fill%3D%22%23d5d5d5%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-82.79938%20-45.81606%2023.04825%20-41.6531%2025.1%20159.3)%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
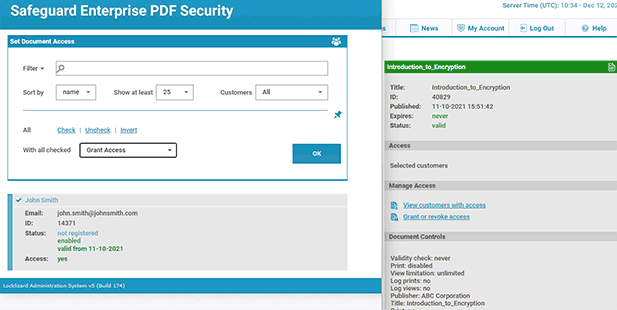
Your protected file will output to its source folder in the .pdc format and you can safely share it knowing that nobody can access it without a valid license. - Add a user account and send them their license via the Safeguard admin portal.
%22%20transform%3D%22translate(1.2%201.2)%20scale(2.41016)%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20fill%3D%22%2357cae7%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(90.48772%20.46606%20-.09282%2018.0206%2065.8%207.7)%22%2F%3E%3Cellipse%20fill%3D%22%23eae2e1%22%20cx%3D%22125%22%20cy%3D%2281%22%20rx%3D%22255%22%20ry%3D%2253%22%2F%3E%3Cellipse%20fill%3D%22%239df1bc%22%20cx%3D%2252%22%20cy%3D%2221%22%20rx%3D%2292%22%20ry%3D%226%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
You’ll need to send your recipients the DRM protected file (or a link to it), alongside a download link for the secure reader application and a valid license. The simplest way of doing this is by ticking “Email license” when you add a new user. See how to add a new user and grant them document access.
Once a user has installed the Viewer and activated their license they will be able to open any DRM protected files you have authorized them to view.
Safeguard DRM Restrictions
- Stop printing, allow printing or limit the number of prints.
- Add expiry – make the PDF expire on a specific date, after a number of views, after a number of prints, or after a number of days from opening.
- Stop printscreen and screen grabbing apps – even from remote connections.
- Log document views and prints to see how your documents are being used.
- Add dynamic watermarks to viewed and or printed pages. Dynamic variables replace actual user and system data when the document is viewed/printed so you only have to protect the document once for all users.
Safeguard’s default DRM protection
- Stops users from editing, copying, and pasting content
- Locks files to devices so they cannot be shared with others
- There are no passwords for users to enter, manage, or remove
- Revoke PDFs & users at any time regardless of where they reside
- Optionally lock user access to specific locations

 DRM Encryption: Are DRM technologies here to stay?
DRM Encryption: Are DRM technologies here to stay?
DRM technologies are here to stay for the foreseeable future – increasingly file and document sharing systems are implementing DRM to provide greater control over digital content use.
Digital Rights Management is the next logical step after encryption for enabling publishers to retain control over their intellectual property and protect their revenue streams no matter where their content is published.
Encryption can only protect content at rest or in transit – once a user opens the file, they have full control over its use. DRM systems use encryption to control document access along with DRM controls to enforce or restrict digital content use.
 Is blockchain DRM the future?
Is blockchain DRM the future?
Using a blockchain for DRM can useful for the validation of user credentials, maintaining a decentralized ledger of licences linked to copyright material, and maintaining access logs. Since the entirety of the data is stored on a number of server nodes and distributed across a peer-peer network, the data cannot be tampered with and hence is immutable. It also prevents the loss of data in case a centralized server goes down, but this may be a moot point with backups, load balancing and other failsafe technologies already in common use.
The problem with blockchain is the speed – both lookups and the writing of data across multiple systems, and the sheer cost of transactions both environmentally and monetarily. However some DRM service providers are likely to be attracted by its novelty. So if businesses are wiling to spend the money and don’t mind the environmental costs, then blockchain DRM might have a future.
Further reading on Digital Rights Management DRM
To learn more about digital rights management (DRM), take a look at the following white papers.
 FAQs
FAQs

How do you define DRM, its meaning, or what does DRM stand for?
DRM stands for Digital Rights Management, a set of permissions, rules, or constraints to limit how content can be accessed and used.
What is DRM content?
DRM content is digital content (i.e. an ebook, PDF document, etc.) that has had Digital Rights Management controls imposed on it to prevent it from being used in an unauthorized manner as determined by the owner, author or publisher of a work. This may be controls to prevent it from being edited, copied, shared, screen grabbed and printed.
Should my ebook/document have Digital Rights Management?
It depends entirely on what you are trying to achieve. Using DRM technology is typically a good idea if you are planning to make a profit, keep certain information out of the public eye, or ensure that your work is not attributed to somebody else. If Digital Rights Management is implemented correctly then it is the only effective security for stopping unauthorized sharing of ebooks. This is because it can be used to restrict how digital content is used (stop copy/paste, disable printing, stop editing, control expiry, etc.). Not all ebook DRM however is equal. Some formats provide limited restrictions and have been comprehensively cracked – so choose your ebook format and protection solution carefully.
Is DRM suitable to keep documents confidential?
PDF DRM software like Locklizard is designed to stop unauthorized sharing, editing, and printing, and this makes it very suitable for keeping confidential documents private.
DRM software or services that rely on passwords (typically online services such as secure data rooms) or watermarks (social DRM), however, offer far less protection – so choose your solution wisely.
Why are many people against DRM?
There is a small but passionate community of people who are anti DRM and say it only hurts paying customers. This is typically because Digital Rights Management places restrictions on legitimate users (such as how many devices a digital book can be used or, whether it can be printed, etc.) in order to prevent illegitimate ones.
However, there is sadly no way to identify whether a user will infringe on a publisher’s copyright in advance. As publishers must continue to make a profit (or users will lose access to the content they love entirely), DRM is the only real option to protect intellectual property from sharing and piracy. To prevent friction, publishers should be proportionate with their Digital Rights Management controls and ensure digital books and other content can be viewed on a wide range of Operating Systems.
Is DRM legal?
Of course. Everybody has a right to protect their creative works and enforce their copyright. However, you must ensure that your DRM is compliant with privacy laws – ie. GDPR and tracking.
What are the laws that govern DRM encryption and digital rights management?
There are laws that govern both the use of encryption and DRM and the protection of copyrighted works. Using cryptography inside a country is usually lawful but there may be requirements that prevent export of cryptographic hardware and software to specific countries (the Wassenaar agreement). There is general agreement that if they are for public sale and the cryptographic mechanisms cannot be altered by the recipients they avoid regulation so that is OK. Where Digital Rights Management is concerned, the US produced the Digital Millennium Copyright Act (DMCA) which criminalizes the production and dissemination of technology, devices or services intended to circumvent measures that control access to copyrighted works.
Do I need DRM or is the DMCA or copyright law enought to protect my intellectual property?
The Digital Millennium Copyright Act (DMCA) and copyright law provide some protection against illegal use of your digital media. However you must be willing to put aside time and expense (lawyers) to enforce this. By using Digital Rights Management the copyright holder or the creator of digital content can prevent copyright infringement (unauthorized sharing and use, illegal distribution & online piracy) to begin with.
What is a DRM service?
A DRM service usually consists of software to protect content (video, games, ebooks, documents, etc.), a licensing server to administer users and content, and software to view content. Protected files are encrypted to prevent unauthorized access and a DRM license determines what authorized users can do with it. A DRM service is usually hosted in the cloud but some Digital Rights Management companies provide own server solutions. Examples include Azure Information Protection, Adobe Experience Manager Document Security, or Locklizard DRM for documents, Adobe DRM and Amazon DRM for e-books, Spotify and Apple itunes for audio files, and Widevine DRM for video streaming. All of these DRM service providers use multiple security technologies that provide content creators with copy protection for their digital assets.
How does DRM differ from Enterprise Rights Management?
Essentially the terms have the same meaning. Digital Rights Management has historically applied to the protection of DVD video, music and gaming, whereas Enterprise Rights Management is a term more frequently used for the protection of business documents.
What is DRM encryption?
Encryption is used in Digital Rights Management software to:
- protect content at rest and prevent unauthorized access
- protect keystores that store decryption keys for files that can be used offline
- securely send data between the client and the server
How does DRM differ from encryption?
Encryption is used to scramble data so that it cannot be used without the correct decryption key. It protects data in transit and at rest. Once the data is decrypted however a user has full rights over its use, including the distribution of unprotected files.
Digital Rights Management is a set of restrictions that control how decrypted data can be used. So users cannot share, copy, edit, print, etc. content. It ensures that only protected files can be distributed.
What is a DRM policy?
A policy is a set of restrictions that can be applied to a file. By using policies you do not have to manually choose the restrictions each time when protecting content.
Does DRM prevent piracy?
It all depends on the implementation. Digital Rights Management enforced in the browser or using a plugin for example is not as effective since it is easier to bypass. DRM systems that use passwords also provide poor security since passwords are easy to share and/or remove. Many e-book solutions have also been poorly implemented, enabling security to be removed using cracking or conversion tools. Properly implemented, DRM can help prevent piracy by stopping illegal sharing and copying of content.
Is a free DRM tool effective?
No. There are many software tools or online services that claim to add free DRM protection to documents. In reality they add poor security such as password protection, JavaScript, and other easily bypassable controls. Usually you have to upload documents to a server where you have no control over unprotected copies.
Is a social DRM or watermarks effective?
Social DRM or social watermarking, sounds like a great way to discourage pirating by identifying users. In reality both visible and invisible watermarks can be easily removed. This is because there is no DRM software to control use of the operating environment.
Is FileCloud DRM effective?
No. FileCloud DRM documents are encrypted with a key and can only be viewed in its secure viewer application. However, keys are managed by the end user, which means they can easily share them with unauthorized parties. Additionally, FileCloud does not stop screenshots in virtual machines or support watermarks to dissuade screen pictures via mobile phone.
Is DRM the same as copyright?
No, DRM enforces copyright by preventing unauthorized access and use of content.









 Free Trial & Demo
Free Trial & Demo What is DRM or Digital Rights Management?
What is DRM or Digital Rights Management? DRM software and solutions
DRM software and solutions What is DRM protected?
What is DRM protected? What are Digital Rights Management restrictions?
What are Digital Rights Management restrictions? How does DRM work?
How does DRM work? DRM protection, protected content, license & software applications
DRM protection, protected content, license & software applications
 Online DRM or Always on DRM vs Offline DRM
Online DRM or Always on DRM vs Offline DRM What is DRM Software?
What is DRM Software? DRM Support of Software & Hardware platforms
DRM Support of Software & Hardware platforms DRM software and single sign-on access integration
DRM software and single sign-on access integration DRM APIs
DRM APIs Advantages / Disadvantages of DRM software implementations
Advantages / Disadvantages of DRM software implementations JavaScript
JavaScript DRM installed app or Viewer software
DRM installed app or Viewer software Which is the best DRM software for security?
Which is the best DRM software for security? Why is Digital Rights Management used?
Why is Digital Rights Management used? DRM in the Publishing Industry
DRM in the Publishing Industry DRM for Standards organizations
DRM for Standards organizations DRM for financial services institutions
DRM for financial services institutions Market research and data intelligence companies
Market research and data intelligence companies Associations & Professional Training Organizations
Associations & Professional Training Organizations What other businesses use Digital Rights Management?
What other businesses use Digital Rights Management? What are the benefits of Digital Rights Management?
What are the benefits of Digital Rights Management?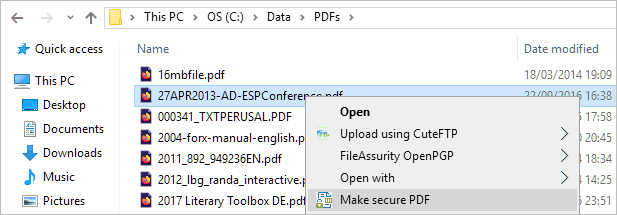
 DRM Encryption: Are DRM technologies here to stay?
DRM Encryption: Are DRM technologies here to stay? Is blockchain DRM the future?
Is blockchain DRM the future? FAQs
FAQs Download DRM Copy Protection Software
Download DRM Copy Protection Software















