Secure Cloud Document Storage and Encryption

How effective is secure cloud document storage for encrypted file sharing?
This blog examines what makes a cloud storage provider secure, whether the reality matches the marketing hype, and what additional steps you can take to achieve secure encrypted file sharing and prevent leaks.
Storing documents & files securely in the cloud

With a general shift towards flexible working over the past decade, cloud storage has become high in demand and even essential for some organizations. Providers have looked to capitalize on this, offering secure cloud storage that aims to meet the regulatory requirements of the modern enterprise. These companies clearly have a stronger focus on security in their marketing material, but how effective are they in the real world for protecting sensitive documents?
This article will cover:
- What is secure cloud storage?
- Is cloud storage safe and secure?
- Are cloud watermarks an effective deterrent?
- Which cloud storage is most secure?
- Achieving secure encrypted file sharing
- The best cloud storage and security
 What is secure cloud storage?
What is secure cloud storage?

Secure cloud storage is, at its core, very similar to any “regular” cloud storage. You upload your files to somebody else’s server and share links via email with others who want to access them. Some providers also allow you to collaborate on documents in real-time with others. There’s no set standard or definition that differentiates “secure” cloud providers from regular ones. There are, however, several features that companies using such a label tend to share.
 End-to-end encryption
End-to-end encryption

Most secure cloud service providers use TLS and end-to-end encryption to protect files when they are in transit and at rest. Data is encrypted on the sender’s device and is only ever decrypted on the recipient’s device – never in the cloud. So files are encrypted while they’re being uploaded and while they are stored, but cloud providers such as Google and Dropbox, always have the ability to decrypt your files.
Some secure cloud storage providers take this further by enabling users to use their own encryption keys (which consists of a public key and private key pair) which they store locally on their device. Files are encrypted using the public key and can only be decrypted with the private key (secret key). This is referred to as “zero-knowledge storage”. This is better for privacy and security than the type of encryption regular cloud providers tend to use, with the core idea being that the cloud provider is unable to access your sensitive files (since the cloud storage provider does not have the keys to decrypt your data) and nor are hackers that compromize the server where your files are stored.
 Access controls
Access controls

The cloud provider gives their customers more options for controlling access to files, folders, and accounts. Features such as multi-factor authentication (MFA) might require users to provide multiple forms of verification before they gain access. Systems such as Role-based access control (RBAC) and Identity and Access Management (IAM) enable more streamlined control over which users can access which files.
 Logging and monitoring
Logging and monitoring

Admins usually get more specific insights into how files are being used, such as who has accessed a file, when, and where from. Most providers will alert them of unauthorized access and if a file is accessed from an unusual location, and some even allow admins to configure policies to determine when they should be notified (i.e. whenever a user shares a file with somebody outside of the organization). However, if a file can be downloaded or printed to file, then untracked copies can be distributed unknowingly.
 Document controls
Document controls

Document controls aren’t unique to “secure” cloud providers, but there’s usually more emphasis on them and often additional features. Other than standard printing, editing, and download prevention, you’re more likely to see options such as expiry, password protection, dynamic watermarks, and open limits.
 Compliance and certifications
Compliance and certifications
Organizations, particularly those that process customer information, have strict regulations they must comply with. Almost all secure cloud providers are compliant with some standards, the most common ones being GDPR, ISO/IEC 27001, HIPAA, and SOC 2. This is hopefully backed by third-party audits.
Certifications however are more of a marketing tool. They do not guarantee that a system is secure or provides adequate data protection, just that it abides by certain cybersecurity policies and procedures. Many companies that have these certifications have had a data breach regardless.
 Is Cloud storage safe and secure?
Is Cloud storage safe and secure?

The features of secure cloud providers certainly improve security in some ways, but they’re not secure in every aspect.
If properly implemented, secure cloud providers can prevent:
- The interception of files by attackers while they are in transit to the providers servers or being downloaded.
- Documents from being extracted and used should their server be comprised.
- Their servers from being compromised in the first place.
 Cloud storage security issues
Cloud storage security issues
Cloud storage is generally better than standard messaging or cloud platforms at protecting your documents in transit and at rest. But they’re still poor at preventing leaks and misuse, especially since login details can be shared.
They cannot:
- Stop users from making unauthorized copies of files.
- Prevent sharing with unauthorized users (leaks).
- Prevent unauthorized editing or printing.
- Provide accurate monitoring.
- Enable dynamic, irremovable watermarks.
Let’s take a look at why this is in detail.
 Why can’t secure cloud providers stop user leaks?
Why can’t secure cloud providers stop user leaks?

To prevent the copying and sharing of cloud documents, you need to stop downloading in any form. This sounds simple on the surface, but means preventing:
- Printing and scanning.
- Printing to file drivers (print to PDF) if printing is allowed.
- Screenshots.
- Copy and paste.
- Downloads.
All of this must be achieved with a very limited toolset, as to prevent malware, a browser must prevent websites from directly controlling a user’s system functions. As a result, developers typically use HTML and CSS to hide certain buttons and features within their web applications. JavaScript, meanwhile, is utilized to interact with and restrict certain browser features.
The problem with using JavaScript controls is that they are primarily executed in the user’s browser rather than at the server level. As such, they can be disabled or bypassed using the browser’s developer mode or specifically designed browser plugins. You can see our how secure are Google Docs or Flipbook or PDF guides for examples of this. HTML and CSS can also be edited in the browser, so users can enable buttons and features that they should not be able to access.
 Are cloud watermarks an effective deterrent?
Are cloud watermarks an effective deterrent?

Some providers implement dynamic watermarks try to make up for their inadequate document controls. The idea is that a dynamic watermark that states the user’s name will deter them from sharing the document.
Alas, while the thought process here is correct, the implementation undermines it. A watermark is only a useful deterrent if it fulfils the following criteria:
- It cannot be removed or modified.
- It clearly states the user’s name and can do so accurately.
- It can be applied automatically to prevent issues at scale.
As we discussed before, cloud providers such as secure data rooms, are unable to prevent users from making local copies of their PDF files, and consequently, they cannot stop them from editing them and removing the watermark.
 Which cloud storage is most secure?
Which cloud storage is most secure?

Just about every provider on the market will say they have the “most secure cloud storage”, “the most secure file sharing solution”, “the best data security for sensitive information” or similar marketing nonsense. The majority have broadly similar data security features to their competitors and the same inherent flaws.
The right choice for your organization typically depends on what you value most:
- If you value company size and reputation: Microsoft OneDrive, Google Drive, and Apple iCloud will probably make the most sense.
- If you think open source is the key to good security: Proton Drive is the obvious pick, as its source code is available on GitHub and has been independently audited.
- If you just want AES-256 bit encryption: Google Cloud, OneDrive, Proton, iCloud (opt-in), Box, and more all support it.
- If integration with your existing security tools/processes is key: Box or Dropbox are most likely to suit your needs.
Other important factors to consider and ease of use, the user experience, support of mobile devices, advanced features, known vulnerabilities, and protection of confidential and sensitive data.
Ultimately, though, as we have demonstrated, no cloud provider is truly secure. Regardless of their feature set, the level of security they provide, or market cap, they do not stop leaks and misuse.
 Achieving secure encrypted file sharing
Achieving secure encrypted file sharing
Thankfully, though secure cloud storage is more marketing than merit, it’s possible to achieve secure encrypted file sharing through other means. You do need to be careful with the type of solution you choose, however, since general file encryption software tools fail to protect files and documents in use – once documents are decrypted users have full control over them. This includes software solutions such as:
- Microsoft Word password protection
- WinZip encryption
- PGP encryption
- Windows Bitlocker encryption
- AxCrypt
- Cyrptomator
You should primarily be using these tools if you want to prevent files from being intercepted en route to their destination or when they are at rest. One example is when you’re uploading files from an insecure network or to a file host that you do not trust to protect your data adequately. If you want to protect documents during use, at rest, and in transit, you should look at a document DRM solution.
 How DRM enables secure file sharing
How DRM enables secure file sharing

Digital Rights Management (DRM) solutions such as Locklizard take a very different approach to cloud document protection and secure file sharing. Though they use AES encryption, a good document DRM solution will only decrypt files in memory, never expose decryption keys to the end user, and lock those decryption keys to an authorized device. This approach is typically combined with a focus on protecting files not only at rest and in transit but also in use. A good document DRM solution will use a desktop viewer app to exert more control over users’ systems, preventing saving, printing, copying, sharing, and screenshots, and enforcing expiration dates regardlesss of offline use.
Overall, a document DRM solution is not as convenient for secure file sharing as uploading a file to a cloud provider and praying. What they do offer, if implemented correctly, is protection for a file’s entire lifecycle and across all of its use cases.
 The best cloud storage security
The best cloud storage security

Locklizard Safeguard is a PDF DRM solution that is purpose-built to protect documents regardless of where they are stored and whether they are being shared securely within an organization or with a third party. Protecting a PDF with Locklizard before uploading it to a cloud service ensures that it cannot be accessed if servers/accounts are compromized or an authorized user shares it with an unauthorized one. Users require a valid license installed on their PC to decrypt and view files, and this license file is single-use by default. As Locklizard also stops saving, editing, and copy-pasting and can optionally prevent screenshots and printing, there is no good route for users to share document content with others.
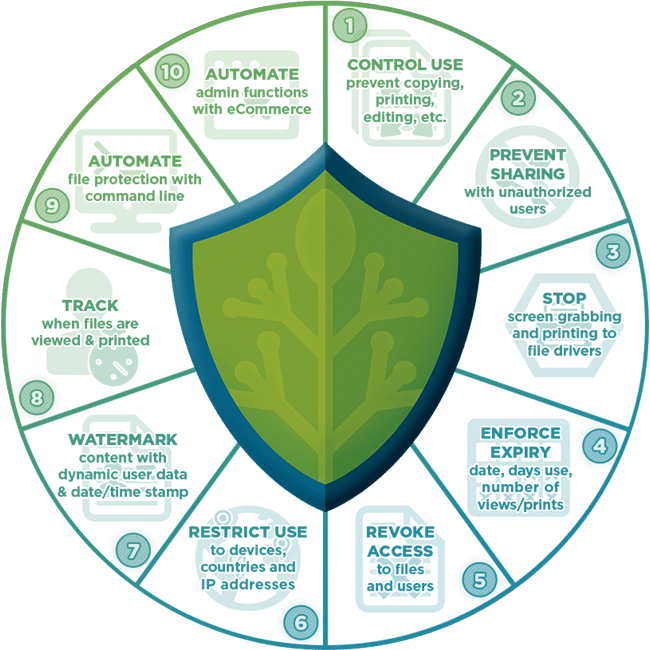
Safeguard provides additional controls to help publishers and businesses stop leaks, enforce compliance, and protect against IP theft. It allows companies to:
- Stop online and offline PDF scraping.
- Restrict access to specific users or user groups.
- Lock use to authorized devices.
- Expire PDF documents based on date, days since first open, number of opens, or number of prints (note: limited opens and prints are not available offline).
- Manually revoke access regardless of where the document is located.
- Disable printing or restrict it to black and black-and-white or greyscale copies.
- Add dynamic, irremovable watermarks that can include usernames, date/time, company, publisher, and more.
- Track who has opened a document, when, and where from.
- Limit access to approved IP addresses and locations.
You can see if Locklizard Safeguard provides the best protection of your business documents by taking a 10-day free trial of our DRM software.
 FAQs
FAQs

Is it safe to store documents in the cloud?
The short answer is that it depends. It depends on your provider, how secure their servers are, what security features they have, how their encryption is implemented. It also depends on you: how well you have secured your account, whether you have taken additional steps to secure your data, and whether your PC is compromised by malware or used in a public place. Ultimately, you have to decide what “safe” means to you. If it means stopping leaks and document misuse, then no – cloud storage is not safe. If you consider your files safe if they are protected from natural disasters, then cloud storage may work for you.
Where is the safest place to store files?
On a local PC at a physically secure location that is disconnected from the internet, preferably in an area with few natural disasters. This is not feasible or proportionate for most people, so an encrypted file on a stationary PC is more common.
What is the most privacy-conscious cloud storage?
It would be impossible to single out one provider. In general, cloud storage providers that use zero-knowledge encryption are the most privacy-conscious. Sync and pCloud are two services that have zero knowledge and are particularly privacy-minded. But in any case, you must place a high degree of trust in your provider and that they do not have any security issues, backdoors, etc.
How can I improve the security of my cloud files?
By encrypting them yourself before you upload them. This ensures you aren’t reliant on your cloud provider to properly store your encryption keys and account. If you want to share files securely with others, or are looking to sell a PDF document online securely, then preferably protect them with DRM software so you can control their use.
Is Adobe document cloud secure?
No. As we have covered how secure Adobe Document Cloud is, it has several issues, including the use of PDF password protection for downloaded files.
Does Google Drive provide encryption for shared files?
Regular and shared files are encrypted at rest and in transit on the server side. They aren’t protected if someone accesses their copies on your local PC or logs into your account.
Does Lockizard secure files other than PDF?
No. We only protect PDF files.
How does Locklizard secure file sharing work?
- The contents of your files are encrypted using the AES (Advanced Encryption Standard) algorithm and DRM controls are applied. File encryption is done on your desktop using a Writer app.
- You give users permission to view protected files via the Safeguard Admin System (web interface).
- Users are sent an email with a license file to authorize their device and a link to download a viewer app. They can install the viewer app on different devices – Windows, Mac, Android and iOS are supported.
- You distribute your protected files just like any other file – via email attachments, upload it to public or private clouds (useful for large files), use SharePoint, etc.
Can users view Locklizard protected documents in the browser?
Yes, with the Safeguard Web Viewer. Protected PDF files can be published to the web and viewed in the user’s browser for a simple secure file sharing solution.

 What is secure cloud storage?
What is secure cloud storage? End-to-end encryption
End-to-end encryption Access controls
Access controls Logging and monitoring
Logging and monitoring Document controls
Document controls Compliance and certifications
Compliance and certifications Is Cloud storage safe and secure?
Is Cloud storage safe and secure? Cloud storage security issues
Cloud storage security issues Why can’t secure cloud providers stop user leaks?
Why can’t secure cloud providers stop user leaks? Are cloud watermarks an effective deterrent?
Are cloud watermarks an effective deterrent? Which cloud storage is most secure?
Which cloud storage is most secure? Achieving secure encrypted file sharing
Achieving secure encrypted file sharing How DRM enables secure file sharing
How DRM enables secure file sharing The best cloud storage security
The best cloud storage security FAQs
FAQs
