How to revoke document access

Why revoking document access is important & how to do it effectively.
In this blog, we discuss the different types of document revocation and what solutions you can use to implement them for PDF documents.
When it comes to document protection, much of the focus is on prevention – stopping documents from leaking, preventing editing, and preventing sharing. The reality, however, is that a system that does not account for failure is not an effective system. Or, as renowned security professional Bruce Schneier puts it:

While hyperbolic, the message is clear. No security system, document or otherwise, is one hundred percent effective. If you do not have the tools in place to detect and act on misuse, you are forgoing a key part of the security process.
This is one of the reasons that document revocation is so important. Even with the best document security tools in place, you can’t account for everything. Perhaps an employee inadvertently sent the wrong document to the wrong people. Perhaps you believe from tracking usage that somebody you sent a document to is misusing it. Or maybe it’s something less malicious: the information you provided initially is simply out of date.
Generally, then the need to revoke documents falls into two categories: planned and unplanned. We’ll be exploring each today, as well as the controls you need to execute them and the type of solution you should be looking for to deliver this.
 Planned disposal
Planned disposal
The most common reason for documents to be revoked is because they have outlived their usefulness. Much like food, many documents have a “sell-by date” – a time after which the information in them is considered too outdated and potentially dangerous. This is especially true with material like training courses, where documents may be constantly updated. Keeping old documents in circulation could result in new or old employees referring to practices that are no longer the best way of doing things.

Embargo and copyright expiry are other common reasons for revocation. Documents may be distributed internally or to press ahead of time, then revoked and reworked for public release. With books, meanwhile, copyright expires 70-years after the author’s death. As a result, you may want to expire paid documents and issue new, copyright-free ones at that point, or remove current restrictions after the fact.
For libraries and digital book rental services, document expiry is an essential part of business. To retain the “loan” structure and prevent illegal distribution, it’s necessary to cut off a reader’s access after a defined period or extend that access after a loan is extended. You also need controls to stop copying and DRM removal, or the user will just create a new copy of the document without the same restrictions. Optionally, you may want to expire documents after a number of opens, views or prints.
 Unplanned disposal
Unplanned disposal
While most of us would prefer all of our document revoking to fall into the former category, it’s sadly rarely the case. There are many scenarios in which it’s necessary to remove access to a document on the fly.
For publishers, for example, it may be necessary to revoke copies of an e-book with a major error and redistribute the accurate version. Membership associations and subscription services, too, may have to revoke access to a document suddenly when a member decides to cancel or when dues are not paid.

Perhaps the most crucial use for document revocation, though, is removing access when a document is misused. Whether it’s a publisher fallen prey to piracy or an enterprise whose confidential meeting minutes have leaked, having the ability to revoke access can greatly reduce harm.
To be able to do so, however, organizations must have comprehensive controls in place. The document needs to be checked over the internet to ensure that access is still allowed, either on each open or at regular intervals. It’s also necessary to have the ability to revoke access to a single or all documents on a per-user and per-publication basis.
 Choosing the right solution
Choosing the right solution
Though several types of solutions claim to protect documents, such as secure data rooms and Adobe’s PDF security, most don’t have the controls necessary to effectively enforce both types of revocation.
 Secure data rooms
Secure data rooms
Secure data rooms usually use passwords as an authentication method to access the secure server space that houses the document. This is not effective for multiple reasons. Firstly, a user can just share their login password to grant somebody else access to the document.
Secondly, data rooms are accessed via the browser, and the browser is not a secure environment. It cannot enforce certain restrictions, such as the blocking of third-party screen grabbing tools. Users can also manipulate the browser via its developer mode or plugins, extracting the document’s text in many cases. For an example of how insecure JavaScript-based browser controls are, see how easy it is to bypass Google Docs security.
Finally, they miss out on the core aspect of security mentioned earlier: the ability to revoke the document if it does leak. Once a user downloads, prints to PDF, or otherwise extracts a document, the admin loses all control over it. It can no longer be revoked or tracked.
 Adobe PDF security
Adobe PDF security
Adobe security that uses password encryption can be trivially bypassed in numerous ways. Documents can be decrypted with a password for viewing, and that password can be passed onto others. Though users can place a separate password to prevent editing, printing, copy-pasting, etc., this is enforced not by cryptography but by the viewer application itself. All somebody needs to do to bypass it is use a viewer application that does not enforce the permissions password, or upload it to an online removal tool.
Adobe Acrobat has no built-in revocation tools either, so once a document is distributed there’s no ‘undo’ button.
 Azure Information Protection
Azure Information Protection

MicroSoft Azure Information Protection or RMS provides protection of documents in the cloud. It enables admins to encrypt MS document formats, and, through policies embedded in the documents, prevent the content from being decrypted by unauthorized users. Specific document operations like printing, copying, editing, forwarding, etc. can be allowed or disallowed, tracking can be enabled, and admins can revoke protected files remotely.
However, an attack in 2016 showed that authorized users could remove the protection, thus rendering it useless. This paper details how to break Microsoft RMS – it covers all RMS implementations, including Azure rights management, AD RMS and Office 365. All a end-user needs is view access to remove the RMS protection from a protected file.
 PDF DRM solutions
PDF DRM solutions
For serious protection, the best choice is a fully-fledged PDF DRM system like Locklizard Safeguard. With Safeguard, organizations can manage everything on the fly from a web portal, revoking documents and applying print, view, and time limits, while effectively cutting out unauthorized copying. At the same time, it has less overhead and requires less groundwork than traditional certificate-based systems, making it a no-brainer for document expiry and revocation.
Here’s how it works:
- You encrypt a PDF on your local PC and add any DRM controls you want to enforce.
- Your protected PDF is saved to your disk and a document record is created on the Admin System.
- You create a user account for each user you want to view your protected confidential PDF.
- An email is automatically sent to the user with a link to the Viewer and their license file.
- Once the Viewer is installed and the license file activated (clicked-on) it is registered to that device and cannot be registered elsewhere (unless otherwise specified).
- You control from the Admin System which protected documents each user can access.
- You distribute your DRM protected PDF just like any other file (email, file sharing site, etc.).
Thus, only people who are authorized to view the document can open or print it, and nobody can edit or copy it. Depending on your DRM license controls and restrictions, you can also deny users the ability to screengrab or view outside of select countries or locations. Safeguard also allows admins to track document views/prints to identify misuse.
 How to revoke document access using Safeguard PDF DRM
How to revoke document access using Safeguard PDF DRM
Safeguard PDF security allows you to revoke document access for all users, individual users, and devices (in case a device is lost or compromised). Note: Revocation cannot occur in offline access mode. Documents must be set to connect to the licensing server when opened, either every time or when an Internet connection is available.
 Revoking a user account so they can no longer view any documents
Revoking a user account so they can no longer view any documents
Revoking a user account can be useful in a number of circumstances. For publishers, the most common use case is when a user purchases an ebook and then performs a chargeback on their credit card. You may also want to revoke a user’s access to all documents if they leave your company or you suspect them of misuse:
- In the ‘Customers’ tab, click ‘Manage’, then tick the user’s name
%22%20transform%3D%22translate(1.2%201.2)%20scale(2.41016)%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20fill%3D%22%23a7a7a7%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-16.48466%20-1.59008%206.39462%20-66.29413%206%2032.3)%22%2F%3E%3Cellipse%20fill%3D%22%23a7a7a7%22%20cx%3D%22248%22%20rx%3D%2214%22%20ry%3D%2214%22%2F%3E%3Cellipse%20fill%3D%22%23e3e3e3%22%20cx%3D%22124%22%20cy%3D%2288%22%20rx%3D%22112%22%20ry%3D%22112%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
- Change the ‘With all checked’ dropdown to ‘Suspend’ and press ‘OK’
%22%20transform%3D%22translate(1.2%201.2)%20scale(2.41016)%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20fill%3D%22%23fff%22%20cx%3D%2298%22%20cy%3D%2236%22%20rx%3D%22116%22%20ry%3D%2221%22%2F%3E%3Cellipse%20fill%3D%22%23d8d3d5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22rotate(-87.7%20101%20-13.5)%20scale(29.59822%20219.03996)%22%2F%3E%3Cellipse%20fill%3D%22%2388ffd7%22%20cx%3D%22158%22%20rx%3D%22169%22%20ry%3D%227%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
- Press ‘SUSPEND’ on the confirmation dialog.
%22%20transform%3D%22translate(1.3%201.3)%20scale(2.60547)%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20fill%3D%22%2355cda5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22rotate(-93.9%2058.8%20-41.4)%20scale(36.81387%20209.78727)%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20cx%3D%22177%22%20cy%3D%22185%22%20rx%3D%2275%22%20ry%3D%2298%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20cx%3D%22194%22%20cy%3D%22186%22%20rx%3D%2288%22%20ry%3D%2288%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
 Revoking a document so that it can no longer be viewed by anyone
Revoking a document so that it can no longer be viewed by anyone
If you want to stop a document from being accessible to all users, you can do so. This is handy if the document has a mistake in it and you need to re-issue it, if the document it out of copyright, if one was distributed accidentally, etc.
- Open the ‘Documents’ tab and press the ‘Details’ arrow next to the document you’d like to revoke.
%22%20transform%3D%22translate(1.2%201.2)%20scale(2.41016)%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20fill%3D%22%23fff%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(1.42813%2019.44742%20-177.76783%2013.05445%2030.6%2050)%22%2F%3E%3Cellipse%20fill%3D%22%238bffd8%22%20cx%3D%22129%22%20cy%3D%2285%22%20rx%3D%22255%22%20ry%3D%227%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(.2096%20-16.41433%2055.14944%20.7042%20145.2%2043.8)%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
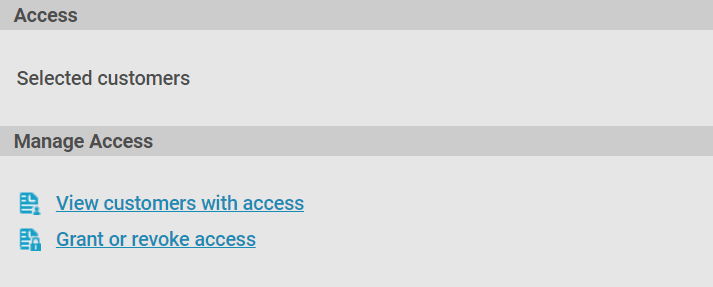
- In the details panel, find the ‘Manage Access’ section and press ‘Grant or revoke access’.
%22%20transform%3D%22translate(1.2%201.2)%20scale(2.41016)%22%20fill%3D%22%23e0e0e0%22%20fill-opacity%3D%22.5%22%3E%3Cpath%20d%3D%22M153%2015h12v17h-12z%22%2F%3E%3Cellipse%20cx%3D%22123%22%20rx%3D%2221%22%20ry%3D%2221%22%2F%3E%3Cpath%20d%3D%22M163.9%2027.5L175%2031l-22.2-16.1%2026%2012.1z%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
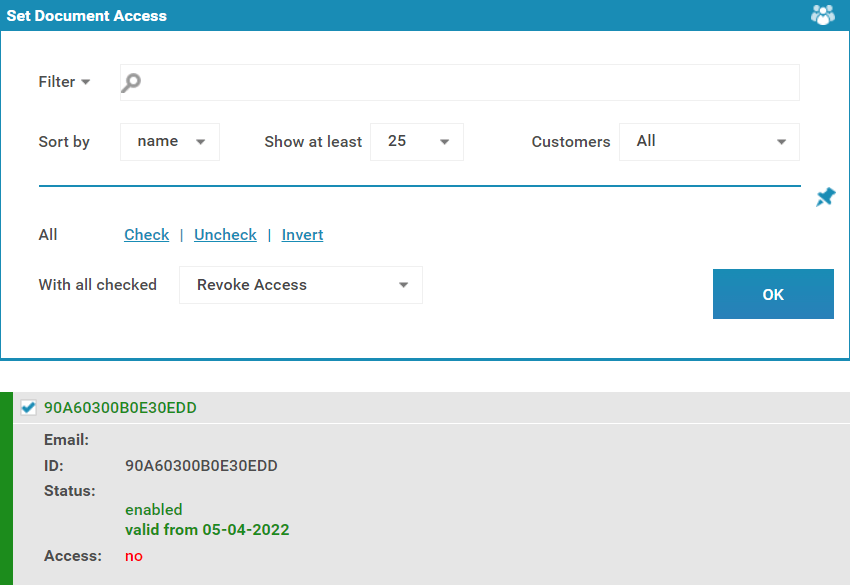
- Press ‘Check’ link to check all users and change ‘With all checked’ to ‘Revoke Access’.
%27%20fill-opacity%3D%27.5%27%3E%3Cpath%20fill%3D%22%23fff%22%20fill-opacity%3D%22.5%22%20d%3D%22M469%20415.6H-39v-271h508z%22%2F%3E%3Cellipse%20fill%3D%22%2392fcd7%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-1.13529%20-33.291%20337.71312%20-11.51668%20447.3%2010)%22%2F%3E%3Cellipse%20fill%3D%22%23d9d6d7%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-45.75711%20126.40263%20-563.47505%20-203.97512%20192.1%20543.6)%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
Press ‘OK’ to apply the changes. None of the customers in your database will be able to access the document.
 Revoking access on certain devices
Revoking access on certain devices
Safeguard restricts documents to devices, but what happens if that device is lost, stolen, or purposefully given away? Even if your device is encrypted without a password or physical security key, you should not assume your documents are safe. Instead, revoke the device’s access in the ‘Customer’ section of the admin portal:
- Click the ‘Details’ arrow next to the customer whose device you’d like to revoke.
%22%20transform%3D%22translate(1.2%201.2)%20scale(2.41016)%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20fill%3D%22%23a7a7a7%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-16.48466%20-1.59008%206.39462%20-66.29413%206%2032.3)%22%2F%3E%3Cellipse%20fill%3D%22%23a7a7a7%22%20cx%3D%22248%22%20rx%3D%2214%22%20ry%3D%2214%22%2F%3E%3Cellipse%20fill%3D%22%23e3e3e3%22%20cx%3D%22124%22%20cy%3D%2288%22%20rx%3D%22112%22%20ry%3D%22112%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
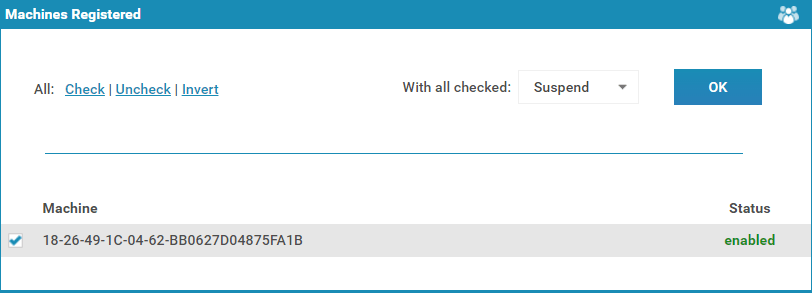
- Press ‘Suspend or Activate’ next to the ‘Device:’ section under the ‘License information’ heading.
%22%20transform%3D%22translate(1.2%201.2)%20scale(2.41016)%22%20fill%3D%22%23e0e0e0%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(.3321%203.64916%20-22.05186%202.00688%2048.7%2081.7)%22%2F%3E%3Cpath%20d%3D%22M79%2076L64%2088l13-36z%22%2F%3E%3Cellipse%20cx%3D%2265%22%20cy%3D%2269%22%20rx%3D%2229%22%20ry%3D%2229%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
- Tick the machine(s), change the ‘With all checked:’ dropdown to ‘Suspend’ and press ‘OK’.
%22%20transform%3D%22translate(1.3%201.3)%20scale(2.60547)%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20fill%3D%22%2376edc4%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(207.97762%208.77918%20-1.01443%2024.03171%20176.3%2015.9)%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(33.7641%20-66.87366%20100.62156%2050.8032%20104.5%20174)%22%2F%3E%3Cellipse%20fill%3D%22%2384d7bb%22%20cx%3D%22210%22%20cy%3D%2214%22%20rx%3D%2245%22%20ry%3D%2245%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
 Revoking individual user access to a document
Revoking individual user access to a document
It’s a good practice to revoke a user’s access to a document when they no longer have a reasonable reason to access the information. This can be achieved through the ‘Documents’ tab in the admin portal:
- Press the ‘Details’ arrow next to the document and click ‘Grant or revoke access’.
%22%20transform%3D%22translate(1.2%201.2)%20scale(2.41016)%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20fill%3D%22%23fff%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(1.42813%2019.44742%20-177.76783%2013.05445%2030.6%2050)%22%2F%3E%3Cellipse%20fill%3D%22%238bffd8%22%20cx%3D%22129%22%20cy%3D%2285%22%20rx%3D%22255%22%20ry%3D%227%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(.2096%20-16.41433%2055.14944%20.7042%20145.2%2043.8)%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
- Tick the users you’d like to revoke, change ‘With all checked’ to ‘Revoke Access’ and click ‘OK’.
%22%20transform%3D%22translate(1.2%201.2)%20scale(2.41016)%22%20fill-opacity%3D%22.5%22%3E%3Cpath%20fill%3D%22%23fff%22%20d%3D%22M180%2065L-2%2023l223-8z%22%2F%3E%3Cellipse%20fill%3D%22%2388ffd8%22%20cx%3D%22166%22%20rx%3D%22133%22%20ry%3D%227%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20cx%3D%2245%22%20cy%3D%2232%22%20rx%3D%22176%22%20ry%3D%2213%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
 The best PDF security solution
The best PDF security solution
To summarize, Safeguard represents a significant upgrade in security compared to other solutions on the market. Through the use of strong cryptography, secure licensing, and a bespoke file format/viewer application, it is able to prevent authorized viewing, copying, editing, screenshotting, and more. Crucially, there are also mitigations in place should the system fail (for example somebody loses their device).
Though DRM can be more expensive than other solutions, in the vast majority of cases it will outlive its value. Leaks and piracy can cost organizations millions, while a PDF DRM solution can be had for a few thousand dollars.
Take a free 10 day trial of our PDF DRM software to instantly revoke document access regardless of location.

 Planned disposal
Planned disposal Unplanned disposal
Unplanned disposal Choosing the right solution
Choosing the right solution Secure data rooms
Secure data rooms Adobe PDF security
Adobe PDF security Azure Information Protection
Azure Information Protection PDF DRM solutions
PDF DRM solutions How to revoke document access using Safeguard PDF DRM
How to revoke document access using Safeguard PDF DRM Revoking a user account so they can no longer view any documents
Revoking a user account so they can no longer view any documents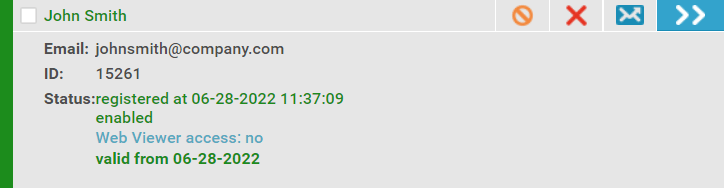
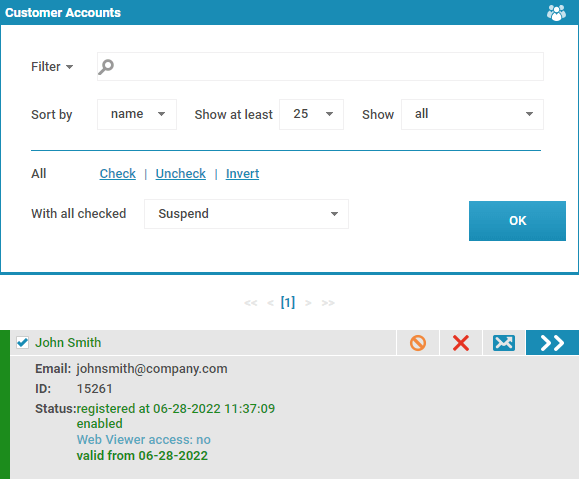
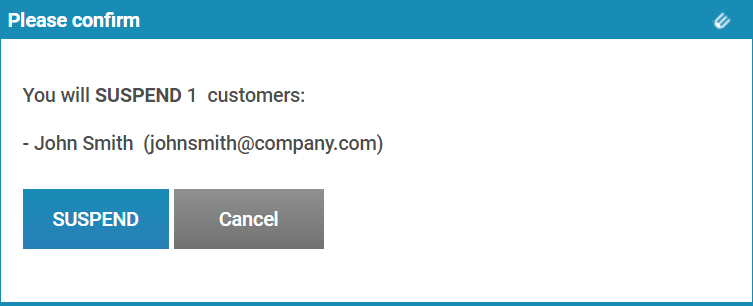
 Revoking a document so that it can no longer be viewed by anyone
Revoking a document so that it can no longer be viewed by anyone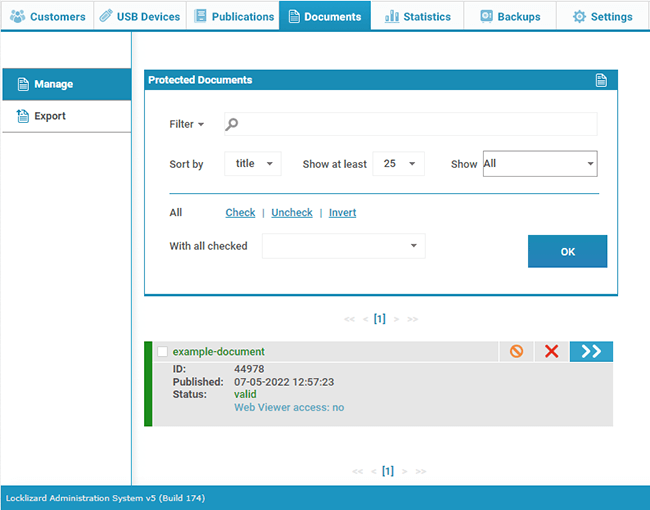
 Revoking access on certain devices
Revoking access on certain devices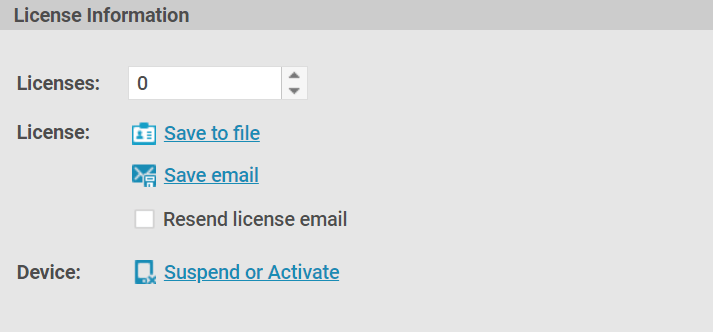
 Revoking individual user access to a document
Revoking individual user access to a document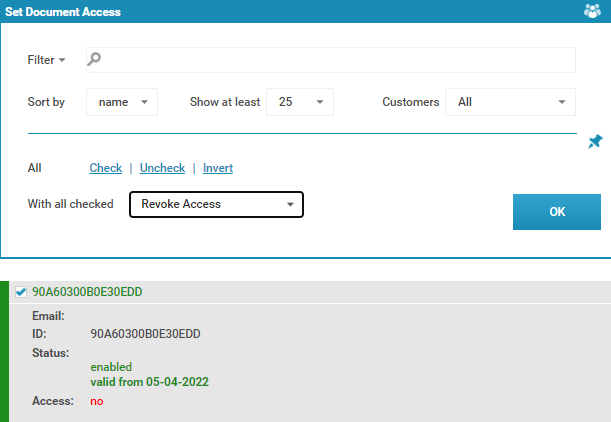
 The best PDF security solution
The best PDF security solution
