How to prevent users removing security from PDF files
Why removing PDF security is so easy & how to permanently protect PDFs
Why password protection & certificates fail to protect PDFs, plus the best practices & tools to permanently prevent PDF sharing, copying, editing, and printing.
Ensuring the security of your PDF documents is essential in protecting sensitive and classified information, but preventing unauthorized access and modification can be a challenge. If you Google “PDF security”, you’ll see hundreds of websites describing ways to bypass and remove PDF passwords and providing the tools to do so. It’s as easy as uploading the document to a webpage and pressing one button.
For organizations, this represents an existential threat. With GDPR and CPRA, consumer data privacy protections are the strongest they’ve ever been. Meanwhile, the risk to your stock price should sensitive board minutes, financial reports, trade secrets, or contracts leak is immense. To prevent this from happening, you need to understand the following:
- How traditional PDF security works
- Best practices to prevent PDF security removal
- Tools to protect PDF files
- How to prevent users from removing PDF security using Locklizard
- Closing words
 Understanding PDF security
Understanding PDF security
There are several types of PDF security, but password security is the most common. Software such as Adobe Acrobat, Foxit PDF, SmallPDF, and various other online services and tools all offer this type of protection.
There are two types of PDF password. They have some key differences:
- The PDF open password: This is used to determine who can open the file, as well as encrypt it.
- The permissions password: Used to control how a user can interact with a document – whether they can edit, print, copy/paste, etc.
If you can take anything away from this article, it should be that these passwords are not an effective way to protect document content from unauthorized access and modification. Users can bypass or break PDF security in several straightforward ways.
 How to remove security from a PDF
How to remove security from a PDF
There are various simple methods to remove PDF passwords or restrictions, with some targeted at removing the open password, and others the permissions password:
- Free online PDF unlockers
Hundreds of free websites allow you to upload a PDF and download a copy without the permissions password or any editing and printing restrictions. In our testing, this entire process took less than thirty seconds. - Microsoft Word’s “Save As” trick
Users can remove permissions passwords intentionally or inadvertently by opening the PDF in Word. The conversion process usually ignores the permissions password to create an editable document that the user can export back into an unprotected PDF format. - Third-party PDF open password removers: Tools such as Elcomsoft’s password recovery software and several other projects attempt to guess or remove the open password using dictionary and brute‑force attacks. Short passwords can be cracked in minutes, and only very long, complex passwords are entirely immune to cracking.
- Removing it in Acrobat
The easiest method to bypass PDF security requires no tools or special knowledge. Someone who knows the password can open it in Acrobat and select “Tools > Protect > Encrypt > Remove Security.” After entering the valid password and saving the file, all protection will be stripped. Anybody they share it with can open it without authentication.
The ease with which users can remove or bypass Adobe-style password protection demonstrates that it isn’t a serious security mechanism.
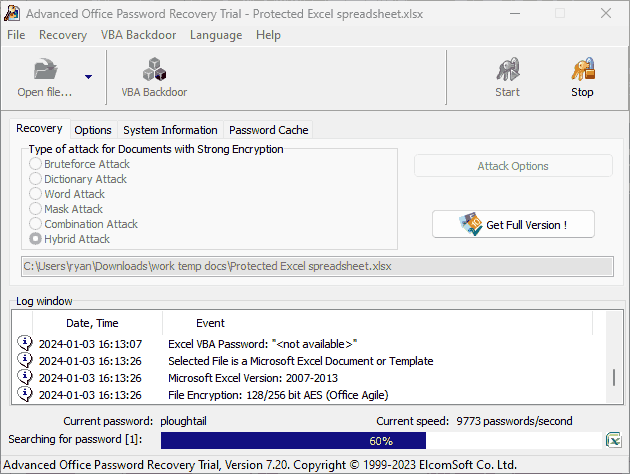
 Removing an owner password with Elcomsoft
Removing an owner password with Elcomsoft
While the Owner password uses encryption, passwords are still generally short and usually relatively easy for a computer to crack because humans choose them. Usually, they pick words you’ll find in the dictionary or something related to the purpose of the document or company, which can be gleaned from metadata. Even if you think you’re typing random letters, chances are you’ll end up with some variation of the letters on the home row of your keyboard.
Password removal tools such as Elcomsoft can remove password protection with various types of attacks. These include using dictionary phrases, guessing based on parts of the password you do know, or systematically trying every combination of numbers and letters. Methods for older versions of Acrobat often don’t require you to know the password at all, as they can brute-force the weak encryption key in several hours.
But there are other, bigger issues with using an open password to prevent unauthorized access:
- Any user who has the password can share it (along with the document) with somebody else.
- You have to find a way to inform users of the password in a secure manner.
- Long, complex passwords are better, but impossible for users to remember.
- You should use different passwords for each PDF, but this could take hundreds of hours at scale to log and maintain them.
In practice, this makes it quite useless.
The security of the permissions password, meanwhile, is completely useless. Users can upload your protected PDF to any number of online tools to strip the permission password and trivially gain the ability to edit, copy, and print at will. They can then share the decrypted, unprotected document with anybody.
 Are PDF certificates a better alternative?
Are PDF certificates a better alternative?

PDF certificates are the second most common PDF security mechanism. They are often seen as a more secure alternative to password-protected PDF files, and they are. You don’t have to worry about how to transmit passwords securely because it uses public key infrastructure (PKI). Users are also much less likely to share their private key vs a password, and files encrypted with a certificate are incredibly hard to crack.
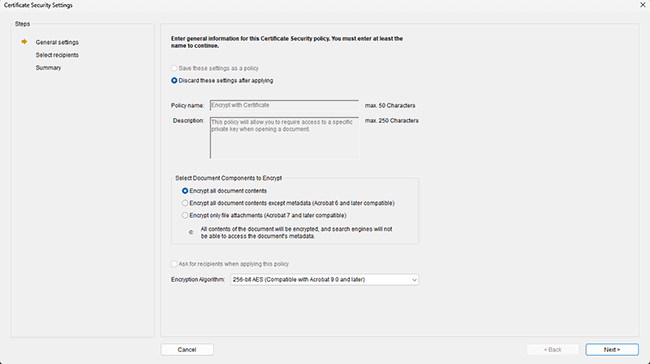
The main issue is that PDF certificates are not designed to stop editing. They are simply a mechanism to exchange private and public keys. Once the user has decrypted the file, they can still do what they want with it. Certificates can also be finicky to use and manage, with the sender needing to have the user’s certificate in advance so that they can protect it with their public key.
We discuss the pros and cons of PDF passwords vs certificates in another blog.
 Best practices to prevent PDF security removal
Best practices to prevent PDF security removal

So, how do you prevent the removal of restrictions in PDFs? If you insist on using PDF passwords and certificates, follow these best practices:
- use a unique, long, and complex password for every copy of every document
- do not share the documents with users that you do not want to edit them
- ensure certificates are regularly revoked and securely maintained
- use strong encryption algorithms such as AES-256 bit
- train your employees on PDF security and the dangers of removing protection
- store PDFs in a secure environment, protected by multi-factor/biometric authentication
- use a reliable PDF viewer that implements security features effectively
- use digital signatures so that recipients can be sure the PDF came from you. Just be aware that they do not prove a document has not been tampered with due to exploits in signature validation.
- add watermarks to your PDFs that contain the recipient’s information (to discourage sharing). Generic please do not copy text is unlikely to be effective.
If you follow these best practices, there’s a lower chance that somebody will intercept and gain access to your documents. Unfortunately, there’s little you can do to stop users who are authorized to view your documents from editing them or sharing them with unauthorized ones. Even user-identifying watermarks won’t go that far, as they can be removed using PDF editing software.
To truly stop users from removing PDF security, you’ll have to start looking at third-party software and services that don’t use passwords for protection.
 | Tools to prevent PDF security removal |
Various products on the market are designed to enhance the security of PDF files to prevent the easy removal of passwords and restrictions. Not only are they more secure, but they have additional features such as the ability to expire documents on a fixed date or after a period of time.
We’ll quickly assess the four most popular options – PDF certificates, PDF plugins, data rooms, and PDF DRM.
 The problem with PDF security plugins
The problem with PDF security plugins

PDF security plugins are tempting because they promise to fix inherent issues with an application. Unfortunately, in this case, they introduce more problems than they solve. While some PDF security plugins can patch a few holes, they create much larger ones:
- Plugins often stop working due to application updates or other conflicting plugins/scripts.
- Attackers can study a plugin to determine why and where it acts, and then create a new plugin specifically designed to overrule it.
- Some DRM document plugins won’t work unless you turn off security in Adobe Acrobat. That makes users more likely to fall victim to malicious scripts or documents.
- Plugins require the same admin rights to install as any software, yet cause admins more headaches. They can be complex and time-consuming to install at scale since IT admins may need to check for and uninstall any existing plugins.
- Plugin controls aren’t usually adequate, either. They typically either batch encrypt PDFs or encrypt content with AES-256 using a key instead of a password, which is still vulnerable to sharing. Others, such as Microsoft Information Protection, are more sophisticated but still struggle with the problems above.
Ultimately, third-party PDF security plugins can only do so much to fix the major document security weaknesses present in Adobe Acrobat. With the constant headache of compatibility on top and easy methods to attack plugins, they just aren’t worth it.
 Why ‘Secure’ data rooms are anything but
Why ‘Secure’ data rooms are anything but

Secure data rooms have a more interesting proposition: what if you allowed users to open PDF files, but only on a secure server that you control? Theoretically, this would mean that anybody outside of the organization who wishes to view your documents would be subject to the same level of oversight and access control as your employees, with tools to prevent the copying of files to external devices. Usually, this is offered as a service by a data room provider, who will allow you to rent a secure server in the cloud that already has access controls applied and a shiny interface to boot.
Unfortunately, while data rooms may be helpful in certain circumstances, they alone do not prevent unauthorized users from gaining access to files or copying them. Usually, access to the secure server space is authenticated via a username and password combination. This can be shared with unauthorized users just as a PDF password can. While yes, measures like IP address restrictions can be implemented, these can also be spoofed through the use of a VPN.
There are other issues with data rooms, too:
- By their very nature, they do not install any security software on the recipient’s PC. This means that they cannot prevent or detect screenshots when the window is not in focus and cannot prevent printing to file drivers.
- Multiple users can often log in at the same time with the same credentials.
- You’ll be uploading your sensitive content to the servers of a third-party, where it is decrypted. You cannot personally assess whether those servers are secure, won’t experience data loss, or won’t retain temporary files after deletion.
- Documents are accessed using a browser, which is not a secure environment. Browser plugins and development tools can be used to bypass security controls in some cases, and often temporary files containing unencrypted information are stored on the user’s local PC where they can be extracted.
 PDF DRM
PDF DRM

Like PDF security plugins, PDF DRM applications try to provide a more secure set of controls for PDF files. PDF DRM software is typically entirely separate from the Adobe Acrobat security handler and does not rely on the application in any way. This allows them to implement a system that is secure from the ground up, rather than trying to patch holes in a sinking ship.
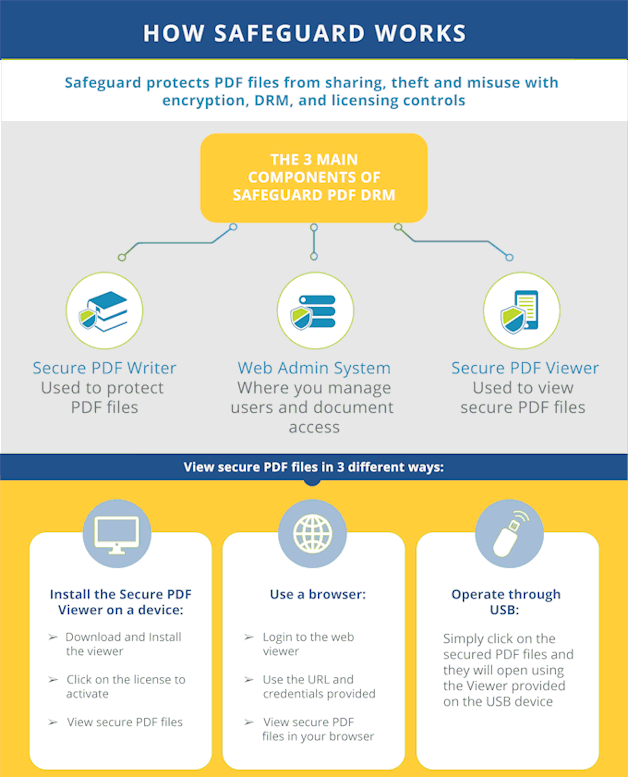
PDF DRM systems generally have three components: a licensing server, a secure PDF viewer application, and a “Writer” application that encrypts the PDF files. When the document issuer encrypts the file, they choose which controls they’d like to apply (stopping printing, copy-pasting, etc.). The document becomes inaccessible to anybody who does not have the correct decryption key, which is transmitted securely and transparently from the licensing server once an authorized user installs a license file.
The user can then open the file in their viewer application and only interact with it within the boundaries of the chosen controls. When it comes to PDF viewers, standalone applications are the most reliable and secure when compared to plugins to existing viewers or browser viewers, as they are much harder to manipulate and have greater control over the operating system.
A well-designed PDF DRM system with a standalone viewer makes it very difficult for users to send high-quality copies of a document to others or edit it. They also typically contain additional measures not seen in plugins or data rooms, such as the ability to lock specific documents to devices to prevent sharing, prevent screenshotting, and printing to unprotected PDFs.
 | How to prevent users from removing PDF security using Locklizard |
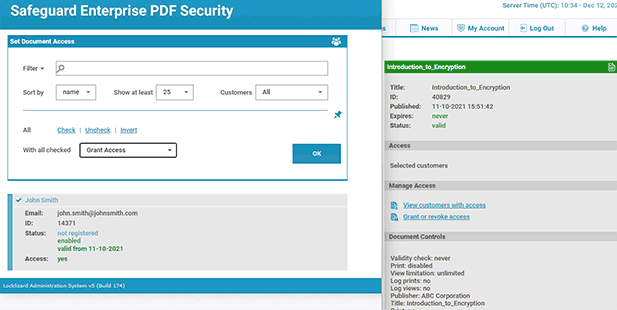
Locklizard does not use passwords and uses its own reader software to enforce restrictions. As a result, users cannot easily bypass or remove the PDF security.
Locklizard Safeguard DRM uses a combination of encryption, secure licensing and key management, and DRM controls to ensure that documents cannot be edited, copied, printed, or shared, regardless of who is using them and where they are stored. These controls are simple to apply, and access and license distribution are managed via a central portal.
Here’s how to protect a PDF and prevent users from removing the protection:
- Right-click on a PDF in File Explorer and select “Make secure PDF”.
%22%20transform%3D%22translate(1.2%201.2)%20scale(2.41016)%22%20fill%3D%22%23fff%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-.5809%2027.73216%20-106.81608%20-2.23748%20197.3%200)%22%2F%3E%3Cellipse%20rx%3D%2246%22%20ry%3D%2230%22%2F%3E%3Cellipse%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(84.31433%2010.80091%20-3.55798%2027.77434%20176%200)%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
- Protect the PDF from unauthorized use by ticking the relevant controls. We recommend that you add a watermark to identify users. Safeguard creates permanent dynamic watermarks that cannot be removed using PDF editing software.
%22%20transform%3D%22translate(1.3%201.3)%20scale(2.57031)%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20fill%3D%22%234b8fc5%22%20cx%3D%2284%22%20cy%3D%227%22%20rx%3D%22194%22%20ry%3D%2215%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-132.31977%2038.04086%20-24.81465%20-86.31426%20103.4%20134.4)%22%2F%3E%3Cellipse%20fill%3D%22%23d4d1cf%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22rotate(82.1%20-70.5%20201.8)%20scale(28.42074%20194)%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
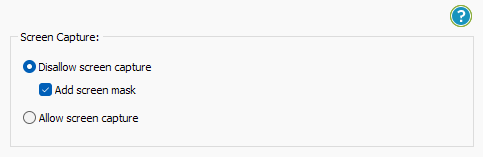
- Locklizard will automatically protect a PDF from copying text and images, but you may want to take additional steps to protect your PDF from screen capture. Without screen capture protection, a user can screengrab your PDF and import it into an optical character recognition tool to make the text editable. To prevent this, open the “Environment Controls” tab and tick “Disallow screen capture” and optionally “Add screen mask” which covers the viewer window with an image if focus is moved away from it.
%22%20transform%3D%22translate(1%201)%20scale(1.88672)%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20fill%3D%22%23cacaca%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22rotate(76.5%20-20%2045)%20scale(59.50181%2038.8711)%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20cx%3D%22161%22%20cy%3D%2259%22%20rx%3D%2295%22%20ry%3D%2295%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20cx%3D%22157%22%20cy%3D%2246%22%20rx%3D%2290%22%20ry%3D%2290%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
- Press the “Publish” button at the bottom of the window.
%27%20fill-opacity%3D%27.5%27%3E%3Cellipse%20fill%3D%22%23d1d1d1%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22rotate(168.9%20164.5%20104.6)%20scale(494.0625%2062.51262)%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(393.1765%20-23.13948%204.63058%2078.68087%20199.7%2040)%22%2F%3E%3Cellipse%20fill%3D%22%23d5d5d5%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-82.79938%20-45.81606%2023.04825%20-41.6531%2025.1%20159.3)%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
Your protected PDF file will output to its source folder in the .pdc format and you can safely share it knowing that nobody can access it without a valid license. - Add a user account and send them their license via the Safeguard admin portal.
%22%20transform%3D%22translate(1.2%201.2)%20scale(2.41016)%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20fill%3D%22%2357cae7%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(90.48772%20.46606%20-.09282%2018.0206%2065.8%207.7)%22%2F%3E%3Cellipse%20fill%3D%22%23eae2e1%22%20cx%3D%22125%22%20cy%3D%2281%22%20rx%3D%22255%22%20ry%3D%2253%22%2F%3E%3Cellipse%20fill%3D%22%239df1bc%22%20cx%3D%2252%22%20cy%3D%2221%22%20rx%3D%2292%22%20ry%3D%226%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
With the PDF published, you’ll need to send your recipients the encrypted .pdc file, alongside a download link for the secure PDF reader application and a valid license. The simplest way to do this is by ticking “Email license” when adding a new user. See how to add a new user and grant them document access.
Safeguard Secure PDF viewer cannot have its anti-editing controls bypassed because it cannot edit in the first place – only highlight and add annotations. It also does not have copy and paste or save as functionality, and does not allow printing to file drivers. You can additionally choose whether to disable screenshots or printing to stop unprotected copies from being created. When you do allow printing or screenshots, you can enable dynamic or static watermarks that identify the original user or place a moiré pattern to throw off OCR and scanning tools.
 Closing words
Closing words

In summary, the following PDF security solutions are clearly not adequate for the protection of sensitive and confidential information.
- Adobe password protection is useless – open passwords can be shared and permissions instantly removed.
- Data rooms don’t offer much additional security and require you to upload documents to a server that is not under your control.
- PDF plugins suffer from compatibility issues, are easily bypassed, and can introduce security vulnerabilities.
There is simply no denying, then, that PDF DRM is the best way to prevent users from removing PDF security. A well-designed PDF DRM system will leave users with no route to bypass controls and edit, print, share, screenshot, or copy and paste a document. It will also introduce new and more granular controls that allow you to apply only the restrictions that are necessary for your use case.
Find out more about how DRM works, or take a 10-day free trial of our DRM software.
 FAQs
FAQs
Is PDF password removal safe?
Removing security from a PDF increases the chances it will be accessed or modified by malicious parties. However, PDF password removal tools are usually safe to use, provided they are local tools (not requiring an upload to a website) and well-respected. Uploading a document for PDF password removal online risks your document being exposed to attackers should they compromise that site.
How do I remove a password from a PDF without Adobe Acrobat?
You can use an alternate PDF editor such as Foxit or SmallPDF if you know the password, and PDF password removers such as Elcomsoft if you do not.
Why use a PDF password remover?
Though it is tempting to think that everyone who uses a PDF password user plans to misuse your document, that is not always the case. Many users remove passwords from PDFs because they find them annoying to enter on open or because they have forgotten them. This is understandable, but still exposes businesses to additional risk.
Is it possible to remove a password from a secured PDF without losing quality?
Quality loss when removing passwords sometimes occurs when you upload your PDF to an online tool, which compresses the PDF before allowing you to download it to save on bandwidth costs. To avoid this, use a local tool such as Adobe Acrobat or a local PDF password remover.
How does encryption affect the process of PDF password removal?
Full encryption (such as that which is used in PDF open passwords) makes security much harder to remove if the password is not known. Rather than exploiting flaws to remove the password, PDF password removal tools must

 Understanding PDF security
Understanding PDF security How to remove security from a PDF
How to remove security from a PDF Removing an owner password with Elcomsoft
Removing an owner password with Elcomsoft Are PDF certificates a better alternative?
Are PDF certificates a better alternative? Best practices to prevent PDF security removal
Best practices to prevent PDF security removal The problem with PDF security plugins
The problem with PDF security plugins Why ‘Secure’ data rooms are anything but
Why ‘Secure’ data rooms are anything but PDF DRM
PDF DRM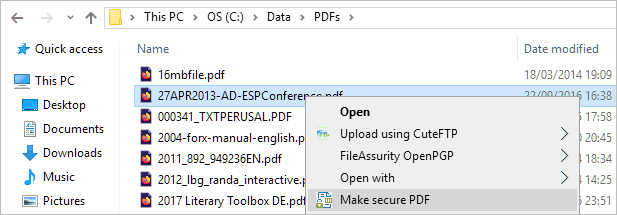

 Closing words
Closing words FAQs
FAQs
