Stopping Screen Sharing & Recording of Documents
How to stop screen sharing and recording of sensitive documents
We explore various methods to block or stop the screen sharing and recording of documents in Zoom, Teams, and Webex, and why ‘secure’ web based document viewers cannot prevent it.
 Why preventing unauthorized screen sharing is important
Why preventing unauthorized screen sharing is important

The screen sharing and recording of documents represents a very accessible way to intentionally or accidentally share sensitive or valuable intellectual property with an unlimited number of users. It’s also difficult to trace – you can’t exactly spy on every Teams or Zoom call.
Failing to stop sharing screens and thus prevent leaks can lead to all sorts of trouble:
- Breach of regulations: Failing to meet data protection standards can lead to fines or legal action, particularly when customer data is involved.
- Loss of competitive advantage: Proprietary information ending up in the hands of a competitor would be disastrous. Such leaks can have a monumental effect on the success and profitability of a business.
- Operational disruption: Certain leaks could cause immediate disruption to a company’s operations and plans due to security concerns or the loss of secrecy. This can naturally be extremely costly.
- Damaged relationships: Leaks damage relationships with partners and stakeholders, who are often collateral damage. You will quickly find that other companies are less willing to do business with one that cannot secure its data.
- Long-term financial impact: A leak can mean other long-term costs such as legal action, lowered stock price, increased insurance premiums, the need to invest in new security, training, and containment measures, etc. If you are selling content and cannot control who pays to view it, then you are effectively giving it away.
 Can you stop screen sharing & prevent screen recording?
Can you stop screen sharing & prevent screen recording?

There are various methods companies use to try and stop screen sharing, but the only affective way you can achieve this is with an installed app that has control over the environment.
- Can you can prevent the recording of screens in the browser?
- Do invisible watermarks stop screen recording?
- How to stop screen sharing via group policy
- Anti-screen capture tools that prevent webcam recording
- Blocking sensitive information recording using DRM
- The only way to block screen recording and sharing
 Can a web browser prevent screen recording or sharing?
Can a web browser prevent screen recording or sharing?
Web based collaboration tools and secure data rooms are two of the most popular “secure” cloud document solutions. Enabling users to view documents in their web browser offers excellent convenience with a simple user experience, so it’s easy to understand why businesses love them. However, the results aren’t as nearly as positive when it comes to stoping screen sharing or preventing screen recording.
The vast majority of cloud collaboration services (Google Workspace, OneDrive, Box, etc.) do not even attempt to stop screen sharing or recording. The methods available in the browser are simply too limited for them to bother with. Users can therefore screenshot, record, and screen share at will and can easily share sensitive information in this way.
A handful of secure cloud document services try to block or limit screen-sharing without much success. There are two popular methods, which we’ll explain in more detail below.
1. Blocking screen recording with screen masks in the browser
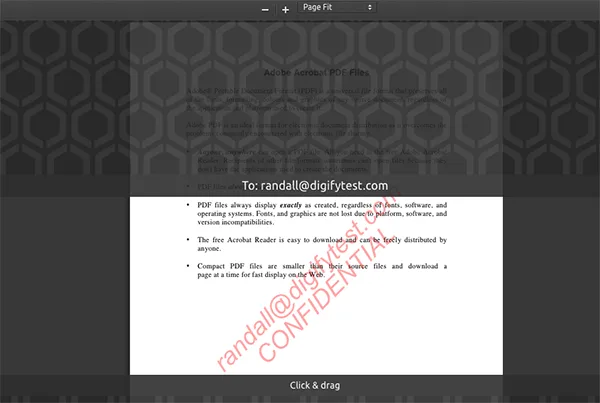
Some services look to prevent screen sharing and recording by limiting the amount of the document that is visible at any given time. Typically, this means that only a thin strip of the document (a few lines of text) is visible surrounding the cursor, with the rest blanked out.
It doesn’t take a genius to figure out that this doesn’t stop the sharing of sensitive information – it just makes it more annoying. The sharer can slowly move their mouse down the page to share the entire contents. Once they have the recording, they can pause it at will and read the whole document. It’s not worth the trade-off in usability for legitimate users.
2. Using JavaScript to block screen recording software
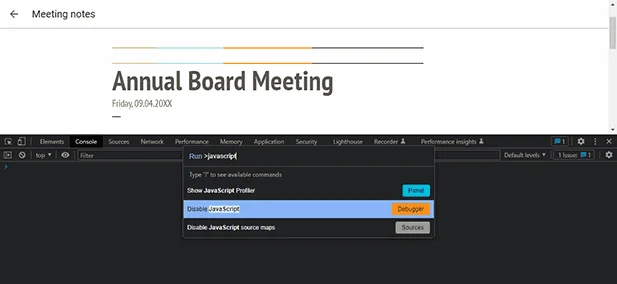
JavaScript is usually the first port of call for developers trying (often futilely) to restrict what users can do in the browser. In the case of stopping screen sharing and recording, JavaScript is totally useless.
Imagine, for a moment, that JavaScript executed in the browser could exercise enough control over a user’s system to disable core operating system functionality and screen recording applications. One visit to a dodgy website and a user’s system would be held hostage by attackers. This is why JavaScript cannot and will never be able to stop screen sharing and recording applications.
In addition, JavaScript only has control over the active browser window. Users can simply have the document open in a browser window (say Chrome) and use another browser (e.g. Edge) to share their screen in a Zoom, Webex, Teams or similar meeting. Screen capturing is then simple and the recorded video can be shared online for later viewing.
Note that JavaScript cannot effectively prevent screenshots either. Users can just use a screenshot tool such as the Windows Snipping Tool to effectively grab screenshots – in fact any screenshot app that is outside of the browser environment will work just fine.
3. Stopping screen recording with browser-based DRM
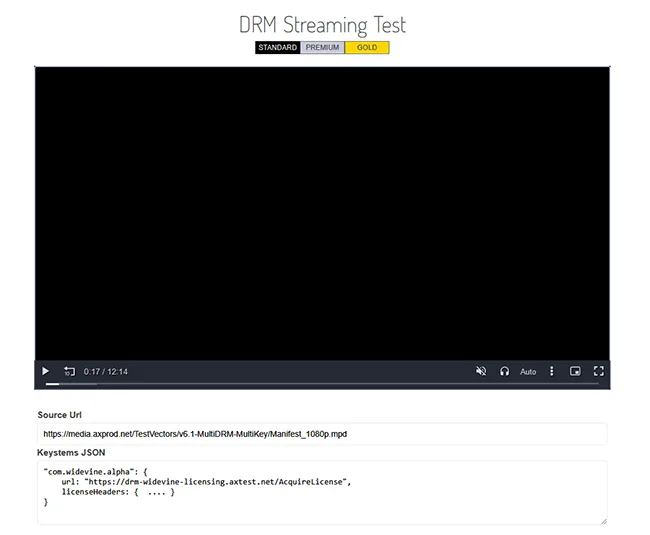
One or two cloud services employ DRM video systems which black out the video when a screen recording tool is used. Solutions that utilize them stream a video of the document from a remote server. This can lead to issues with latency that hamper the user experience without being particularly effective.
However, a simple workaround is to host a Zoom, Webex, Teams or similar meeting in a different browser and share the content that way. Remote users can screen record at their leisure.
This is true, regardless of the OS or browser. While Safari on Mac and iOS with Fairplay DRM supports anti-screen capture, that is just within the active browser window. Users can resize that and create an online meeting using another browser and share their screen for remote recording.
 How to screen record blocked content
How to screen record blocked content
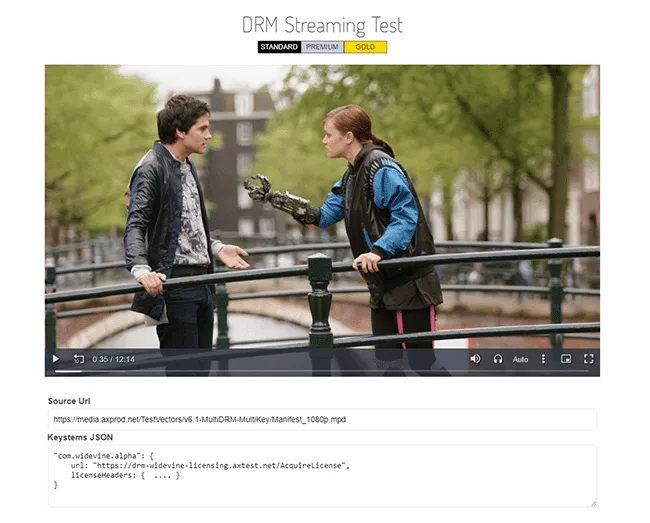
Historically, video DRM technologies have been ineffective at preventing screen recording. Most browser-based DRM systems can be circumvented by:
- Turning off hardware acceleration in their browser.
- Opening the document in a Zoom, Webex, Teams or similar meeting and recording that. Using a different browser than the one playing the video will bypass software security, and remote users can record DRM protected content without restrictions (even it the DRM video solution uses ).
Even Widevine L1 which requires a special hardware component to enforce, is not effective, which is why you will see Widevine protected content all over piracy sites.
There is also lots of incompatibility issues with browser-based video DRM software. Firefox for example only supports Google Widevine CDM and not Apple Fairplay DRM.
Ultimately, video-based document DRM is a novel idea but not a particularly practical one. While admins can disable users’ ability to turn off hardware acceleration, this requires control over the device in question. While such a setup may work for some businesses, many have a BYOD policy, a flexible workforce, or outside parties they need to share with.
 Do invisible watermarks stop screen recording?
Do invisible watermarks stop screen recording?
Invisible or forensic watermarking is often touted as a useful anti-piracy measure to enhance security and stop users from sharing screen recordings with unauthorized parties. However, as covered extensively in Invisible or visible watermarks, we do not recommend this.
While forensic watermarking may help you to track down a leaker after the fact (assuming the content is posted to the web), they are of little use as a preventative measure. Logic dictates that if a user doesn’t know an invisible watermark is there, they won’t be deterred from sharing your intellectual property. If you inform them of a visible watermark, they can look for it and remove it unless you have strong anti-copying and editing controls. If you have those, why does the watermark need to be invisible? It’s far better to display a visible watermark that identifies the user, as this reminds even non-malicious users to be careful who they share the document with.
 How to stop screen sharing via group policy
How to stop screen sharing via group policy
![]()
One option for the prevention of screen recording is to control screen capture via group policy. Microsoft provides a number of policies for Microsoft Edge Enterprise that allow admins to enable or disable screen capture in web browsers. This can be applied globally or with exceptions for specific sites.
These can help, but they’re very limited:
- In our testing, the feature only stopped screen capture originating from Edge. The policy did not prevent capture by the Zoom application, Discord, Google Meet, or even Microsoft’s own Teams app.
- The policies only work in Edge for Business, not Chrome or other browsers of choice.
- You can’t block screen capture specific documents in the browser, just websites. This makes the feature of limited use if you use Google Docs for both sensitive and non-sensitive content, for example. Users wouldn’t be able to screenshare their browser in authorized circumstances, which would hamper productivity.
- Group policy requires administrative control over a user’s PC. This might work if you are a traditional enterprise with on-premises users. If you have a BYOD policy, use freelancers, or work with third parties, it’s not much help.
Perhaps these policies can be helpful when combined with other per-application policies, an IRM solution, or by very strictly limiting what apps users can use. As far as we could test, however, they were practically useless in a real-world use case.
 Anti-Screen capture tools that prevent webcam capture
Anti-Screen capture tools that prevent webcam capture

There are various insalled apps that provide anti-piracy measures to prevent webcam capture, screenshot capture and block screen recording.
How effective are screen recording prevention tools in protecting sensitive information? Well not very because of the following issues:
- You cannot enforce users to install these applications. They might work in a locked-down corporate environment as long as the administrator has full control over every device and can prevent removal of the anti-screen capture software.
- They are a blunt tool. All screen capture and recording is prevented on the device, which is not very productive if you want users to be able to collaborate with others.
- Screen recording prevention and screen capture blocking can impact the user experience of legitimate users and content creators.
Ultimately you only want to prevent screen capture and recording of valuable IP, whether that is confidential, sensitive or revenue generation information.
 Blocking screen recording of sensitive information using DRM
Blocking screen recording of sensitive information using DRM

If they are developed with good security principles, digital rights management (DRM) applications can prevent screen sharing, screen recording, and screen capture of documents.
Locklizard Safeguard is one such application and works as follows:
- You protect your sensitive documents in the Safeguard Writer app locally on your device. This applies encryption and DRM controls (including screen sharing, recording and capture prevention).
- In your admin portal, you add users to the documents you want them to have access to. You can tick a box to automatically send them their license email and a link to download the Locklizard secure viewer application.
- To view the protected PDF, the user must activate their (by default) single-use license, which is locked to their device.
- When the user tries to open the PDF, the viewer application checks that the license is valid against the licensing server and reads the restrictions encoded in the PDF.
- The decryption keys for the PDF are transmitted to the authorized user’s device, and the document opens. The user cannot view or share the decryption keys as they are encrypted. The document itself is only ever decrypted in memory.
- When a user tries to screen share or record the PDF, they will see a grey box over the content.
Users cannot bypass or remove DRM controls (something that is simple to do in the browser).
 How do I stop screen share and recording with Locklizard?
How do I stop screen share and recording with Locklizard?
It is really simple to stop users sharing screens or block recording of your sensitive info or valuable IP using Locklizard. In Safeguard Writer just select ‘Disallow screen capture’.
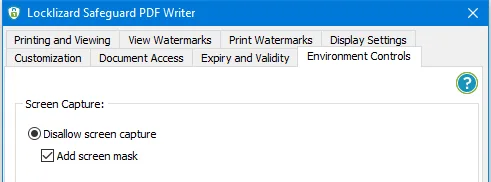
This will prevent users being able to remotely share your documents using online meetings, screen recording, and grabbing high quality screenshots using screen capture or recording apps.
Instead of the protected document, all they will see is a black screen or grey window.

 The best way to stop screen sharing and recording
The best way to stop screen sharing and recording

Locklizard provides comprehensive content protection that ensures security beyond the browser. As well as effectively preventing screen sharing, screenshot and screen recorder applications, it:
- Stops editing
- Prevents copy-paste
- Prevents sharing with unauthorized users
- Stops saving as unprotected files
- Allows you to disable printing or control printing (number of copies, black and white or color)
- Allows admins to log when a document is opened or printed, by whom, and from where
- Can apply dynamic, irremovable watermarks to documents that clearly state the reader’s name and other information. This helps to stop users from taking a video of the screen with a smartphone camera
- Lets you revoke documents instantly, regardless of where they are located or which devices they are stored on
- Locks documents to specific devices, locations, and IP addresses
- Can be used to expire documents after a number of opens, prints, days, or on a specific date
To see for yourself how Locklizard Safeguard can stop screen capture, unauthorized access, and misuse, take a 10-day free trial of our DRM software.
 FAQs
FAQs

How do I stop screen sharing on Zoom?
Admins can sign into the Zoom web portal to edit account settings and turn off the ability to share screens. However, banning screen sharing entirely will compromize productivity. It makes more sense to protect specific sensitive files with anti-screenshot controls using a DRM solution. This way, users can share their entire desktop if they wish, but the sensitive document will always be blanked out.
Note that if users want to share sensitive documents they have access to then they will just host their own Zoom meetings. Admins can only stop screen sharing of sensitive documents on Zoom if they have full control over the users environment (i.e. hosting the meeting).
How can I stop screen sharing on Webex?
Go to “Services > Calling > Client settings” and toggle off the screen sharing toggle from “In-call experience”.
How can I stop screen sharing on Teams?
In the Teams admin center, go to “Meetings > Meeting policies,” and under the content sharing section, switch screen sharing mode to “Not enabled”.
Is screen mirroring a security risk?
It can be. If you enable screen mirroring on enterprise devices, users may accidentally mirror to the wrong device when they are using public Wi-Fi, leaking sensitive information.
Can screen recording be detected in the browser?
No. Websites generally don’t have the necessary privileges to detect and prevent screen recording. The exception to this is if you are using a browser extension for the recording, which some sites may be able to detect.
Does video DRM stop screen sharing effectively to prevent piracy?
No. DRM systems like PlayReady, FairPlay Streaming, and Widevine are capable of preventing screen recording tools but they are not effective. Companies such as Netflix use Widevine DRM, which is seen as the gold standard for video DRM. However there are numerous ways users can bypass it, such as remotely recording from another device. Widevine DRM L2 and L3 protected content played on Firefox or Chrome can be easily duplicated with a screen recording app. This is also true of Microsoft Playready DRM (SL3000), , and DRM from other content providers. If content can be viewed in the browser then it can also be captured and shared. The browser only knows about its own environment and not another browser running a meeting online.
Does hardware DRM prevent screen recording?
Not effectively. Even if you prevent playback of content on specific browsers and devices that do not support hardware DRM, users can connect to the device using via a remote meeting and record content without restrictions.
While users can of course always record screenplay using a mobile phone, the playback quality will not be as good.
What methods can be used to prevent screen recording on devices?
Hardware or software DRM, visible and forensic watermarks can all help to prevent or deter screen recording, but nothing is foolproof.
Can Locklizard stop screen sharing of my browser/desktop?
No, Locklizard only stops screen sharing of digital content (research documents, training courses, etc.) in our secure viewer app.

 Why preventing unauthorized screen sharing is important
Why preventing unauthorized screen sharing is important Can you stop screen sharing & prevent screen recording?
Can you stop screen sharing & prevent screen recording? Can a web browser prevent screen recording or sharing?
Can a web browser prevent screen recording or sharing? How to screen record blocked content
How to screen record blocked content Do invisible watermarks stop screen recording?
Do invisible watermarks stop screen recording? How to stop screen sharing via group policy
How to stop screen sharing via group policy Anti-Screen capture tools that prevent webcam capture
Anti-Screen capture tools that prevent webcam capture Blocking screen recording of sensitive information using DRM
Blocking screen recording of sensitive information using DRM How do I stop screen share and recording with Locklizard?
How do I stop screen share and recording with Locklizard? The best way to stop screen sharing and recording
The best way to stop screen sharing and recording FAQs
FAQs
