Invisible or visible watermarks for copyright protection?

Watermarking: Are invisible or hidden watermarks or visible ones best?
Invisible watermarks are great for protecting images from copyright infringement but don’t work so well with documents. This blog explains why visible watermarks are more effective as a document copy deterrent.
 What are we trying to achieve with watermarking?
What are we trying to achieve with watermarking?
Watermarking is a complex subject that requires some thought. You need to understand what you’re trying to solve and how effective different techniques are at protecting digital information. This is never more true than with PDF document watermarking.
Watermarks can serve many purposes, including:
- Hiding information from the public view
- Proving that the information is authentic
- Proving the owner of the information
- Identifying the authorized user of the information
- Preventing editing photographic copies or transforming the original without being detected
There are two basic types of watermarking as far as the human eye or a camera are concerned – and they are invisible watermarks (hidden watermarks) and visible watermarks. So, we shall look at each, covering:
- What are invisible or hidden watermarks?
- Invisible watermarks and text files
- Invisible watermarks and images
- How to make a PDF watermark not visible (hide watermark)
- Invisible watermarks in Social DRM for ebooks
- Removing invisible watermarks
- Visible watermarks
- Invisible vs visible watermarks as a copyright deterrent
 Invisible or hidden watermarks
Invisible or hidden watermarks
Invisible watermarks, also known as steganography (from the greek “stenagos” – covered), or hidden watermarks, are so-called because they’re not obvious to anybody who doesn’t know they’re there. They contain hidden patterns or symbols that convey information to those “in the know”.
In some forms of steganography, a secret meaning may be ‘hidden’ in a picture. For example, a picture with one apple on a table has one meaning, but one with two apples means something entirely different. There is no direct attack against these forms of steganography, short of finding the codebook(s) for interpreting the meanings.
Even small patterns are easily visible on small images
An invisible watermark has to contain enough information to either identify the Copyright Owner and/or the licensed user. That means that an invisible watermark needs a background in which to hide or be hidden. Commonly, this means having a picture (or video still) into which, according to a set of rules (they vary with the various schemes that are in existence), pixels with a particular coding or definition replace existing pixels. These form one or more patterns, usually encoded, which can be extracted by re-processing the picture following the rules for the scheme.
As you can imagine, with video or sound there is a huge amount of information flowing. There’s plenty of ‘room’ to hide invisible watermark information that is imperceptible to the human eye. All well and good.
As usual, the devil is in the detail. There has to be enough picture information to ‘hide’ the watermark information so that it is not visible and able to be removed. A drop cap or simple illustration in a book isn’t going to be enough.
 Adding invisible watermarks and text files
Adding invisible watermarks and text files
A file of ASCII text has no spare space in it to hide anything, so the technique is not going to work with txt files.
It might work if you considered the page of text to be a graphic (rather like PDF can) but there is still the problem of where to hide the information so that you can find it later and prove it is reliable and not some mere accident.
 Hidden watermarks and images
Hidden watermarks and images
Invisible watermarks have been commonly used in images to prove the owner of the information and establish copyright.
If you are going to add an invisible watermark to an image, then the image file must have plenty of pixels to hide it in. Otherwise, the watermark will become visible and degrade the picture. Invisible watermarks generally use high-resolution image files because they use a lot of pixel data, so changing a pixel here and there does not degrade the picture. The reason for this is that the stored file has to be reproduced exactly, not a bit more or a bit less, or it doesn’t work. So, to make it work you need one or more large pictures in which to hide the invisible watermarks you want to add.
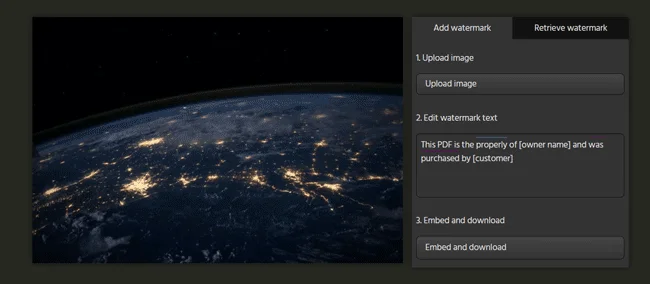
The protector has to manually replace the owner and customer fields for each image
There are also problems with this approach in that if the form or format of the picture is changed, it may not be possible to maintain the state of your modified pixels. A change from a png to a jpg for instance, or to grayscale from colour, may be enough to prevent recovery of the hidden message. This problem was well-researched in the 1990s, and there are lots of patents relating to the preservation and recovery of hidden information across various modifications.
Adding invisible watermarks in Photoshop
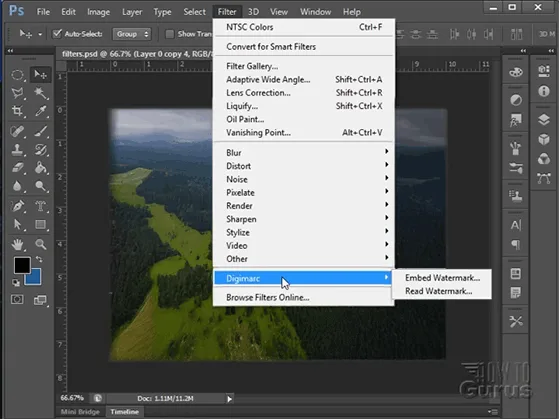
Another popular way to add invisible watermarks to images is through add-ons such as Digimarc for Photoshop or other editing software. Digimark is a more advanced version of the concept presented above. The process goes something like this:
- You load the image into Photoshop and press “Filter > Digimark > Embed Watermark”.
- After you save and share the image, anybody can open it in Photoshop and press “Filter > Digimark > Read watermark” to find a link to the original owner.
However, adding invisible watermarks in Photoshop with Digimark has the same issues as any other invisible watermark. It works inconsistently, especially once images are shared on the internet and become subject to compression, noise reduction, and anything else that may modify colours and contrast. Additionally, you must keep an active Digimark subscription to properly read the link. This subscription costs many thousands of dollars per year.
Ultimately, such watermarks are better used for things such as adding tracking information to product packaging and other printed products that will not materially change after distribution.
 How to make a PDF watermark not visible (hide watermark)
How to make a PDF watermark not visible (hide watermark)
To create a PDF with an invisible watermark or make a PDF watermark not visible, the original file would have to have the invisible watermark added to it by an application before distribution. Alternatively, the protection software would have to determine when there was the opportunity to add an invisible watermark and insert dynamic information (such as a username) when it is viewed and/or printed. At the moment, this is not possible.
Basic text-based invisible watermarks can be difficult to distinguish if you have a busy image
As the facility to add invisible watermarks dynamically does not exist, you’d need to manually reprocess the same PDF file for each user, adding a unique identifier. This clearly involves a lot of work and document management, which could be made futile if the invisible watermarks can be easily removed.
 Invisible watermarks in Social DRM for ebooks
Invisible watermarks in Social DRM for ebooks
A more recent spin on the invisible watermark idea is so-called social watermarking for ebooks. In this scenario, there are both visible and invisible dynamic watermarks, with the invisible watermarks hidden in the document’s code, image file names, etc. Unfortunately, while they are not immediately obvious, this kind of watermark is quite easy to remove. As the ebook has no other protection against editing, the user can view and change the document’s code and filenames. Once you know what the text identifiers look like, it doesn’t take long to perform a find and replace and remove them all.
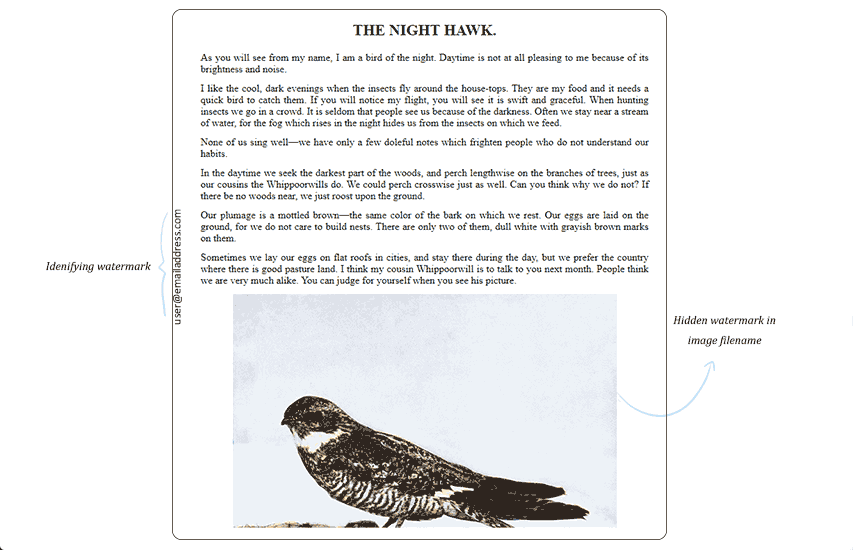
Visible and invisible watermark text in an ebook
Of course, if the user doesn’t know there are hidden watermarks, they won’t remove them. However, this also means they won’t have a reason not to share it. Either way, your document ends up out there in the wild.
 Removing invisible watermarks
Removing invisible watermarks
When using invisible watermarks, you need to make sure that the watermark survives screen grabbing, printing, or format changes. PDF documents that are not protected in any other way can be saved into a different format or printed as physical documents and then run through a scanner. The invisible watermark is then lost.
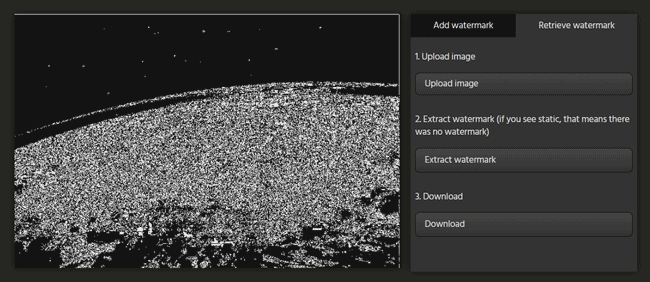
Screen grabbing the image can remove the image watermark due to different colors and encoding
There have been proposals to create invisible watermarks where pictures can survive transformation from (say) png to jpg but they are less clear about what happens if pictures have their size and shape changed, or if they are printed and then scanned. Images that are screen grabbed are in a different format from the original and may also avoid the invisible watermark too.
These approaches to defeating invisible watermarking mean that a recipient who can obtain a document that is not fully controlled can effectively bypass the controls and continue to do what they want – even if they have to invest more effort than they might like.
So, you can only make invisible watermarks for documents effective if combined with a document control system such as DRM to prevent conversion to other file formats and screen grabbing. Otherwise, they could be easily removed.
 Visible watermarks
Visible watermarks
These turn out to be very useful indeed when used with secured documents. The fact that these watermarks are visible makes them much more secure to implement because everyone can ‘see’ the watermarks and test if they look right. No amount of changing the view on the screen or the printed page can completely lose these watermarks. See PDF watermarking and insert watermark in Excel.

Visible watermarks also have a history. They are well established in the protection of banknotes, cheques, international agreements, and so on. They also provide a strong way of preventing forgery – though trying to forge encrypted documents is more difficult already (you need to completely break the encryption/decryption scheme in use).
Watermarks on cash are passive. Once set up, they can tell you about the organization that created the note and whether it’s legitimate, but nothing about who is authorized to spend it. Credit cards, however, have an additional tangible link to the purchaser – the name on the front. The same can be said about protected PDF documents. Like a card, a secure PDF is licensed to a specific person – authorized for whoever is holding it. Because of this, secured PDF documents let you identify the recipient and the supplier, which is a great deal more powerful than previous watermarking methods.
Protected PDF watermarks can be powerful in other ways, too. Most importantly, you can use dynamic watermarks (user info automatically inserted at view/print time) so that you only have to protect a document once for all users. Once configured, you can place watermarks on top or underneath the content, but have them work independently from it. They’re separate layers of content that you can hand-place to minimize harm to the digital reading experience. You can even have a toned-down watermark for the screen, but automatically insert a more visible alternative once the user prints the document.
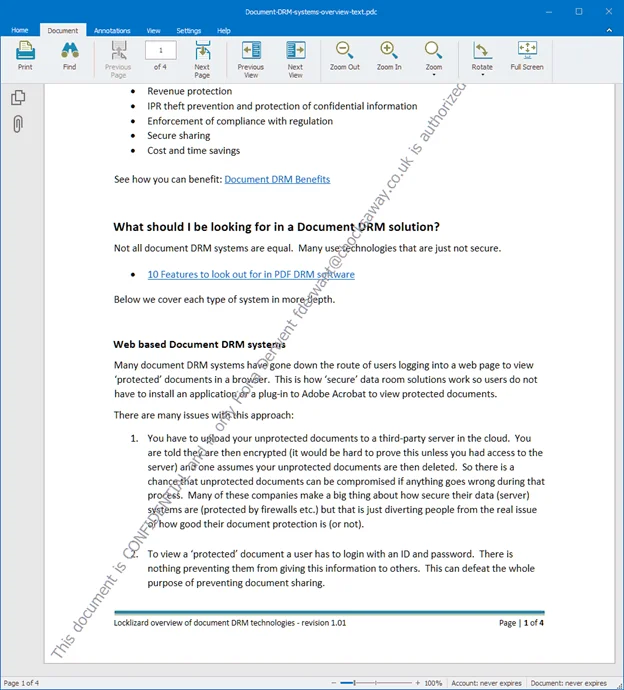
Dynamic watermark displayed in Safeguard Secure PDF Viewer
PDF secure watermarks also have the power to reveal who the licensed user of the document is. If they allow their access and authority to be misused, they can be held to account. In this way, you can use a watermark as a deterrent. Of course, while doing so, secure PDF watermarks continue to provide traditional capabilities: identifying the copyright owner and making it more difficult to falsify documents.
Like any security problem, somebody with enough money, time, and expertise can bypass the watermarks. They can use a high-resolution camera to photograph every page and remove watermarks pixel by pixel. However, very few would find it worth the tremendous investment when it would be cheaper to just buy a copy.
 Invisible vs visible watermarks as a copyright deterrent
Invisible vs visible watermarks as a copyright deterrent
The point of making a secure document is usually to prevent ‘secret’ information from being made publicly accessible. Invisible watermarking only serves to hide another secret inside of that restricted information. It does nothing to physically (or digitally) prevent sharing with others and does not even work as a deterrent because the watermarks are invisible. It is only helpful for tracking down the source of a leak after it has happened – when it is already too late.
Invisible watermarks are therefore most useful for establishing copyright on content that you want to be publicly available. For example, as a photographer that posts images online. In this situation, they can help you prove that you’re the original owner (though they are still prone to breaking after being screen grabbed or compressed for social media). What they are not good at is identifying users you have distributed a document to.
Locklizard believes that document watermarks that are clearly visible are more effective. We do not grant recipients control of protected documents so they cannot edit the content to remove our watermarks. Safeguard PDF disables the ability to screengrab with software, and taking a picture with a camera will identify the authorized user due to irremovable dynamic watermarks. Printing is also covered. Publishers can disable printing entirely to avoid scanning, or let users print a specified number of times with an obvious identifying watermark.
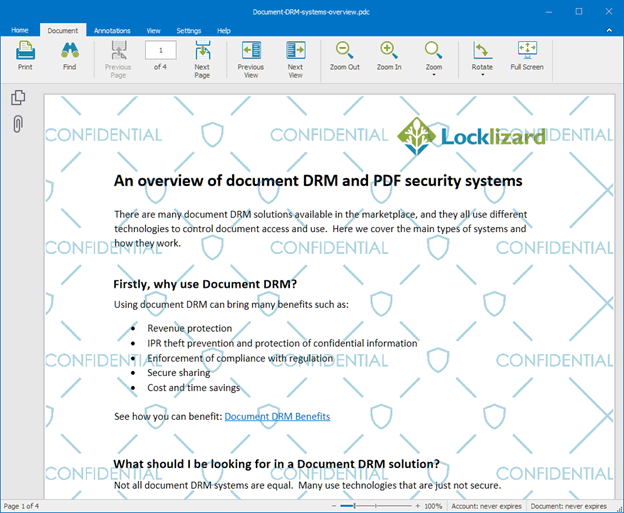
Confidential image watermark displayed in Safeguard Secure PDF Viewer
The range of visible watermarking options supported by Locklizard is significant. You can have both text and graphics watermarks running both on top of and underneath the content layer, and these may be as subtle as the publisher wishes to go – there are no limitations on the selection of graphics or fonts. All the watermarking information is itself protected to prevent it from being tampered with or overridden. Using visible watermarks in this way avoids the inherent problems with steganography while being more effective, simpler to implement, and reliable.
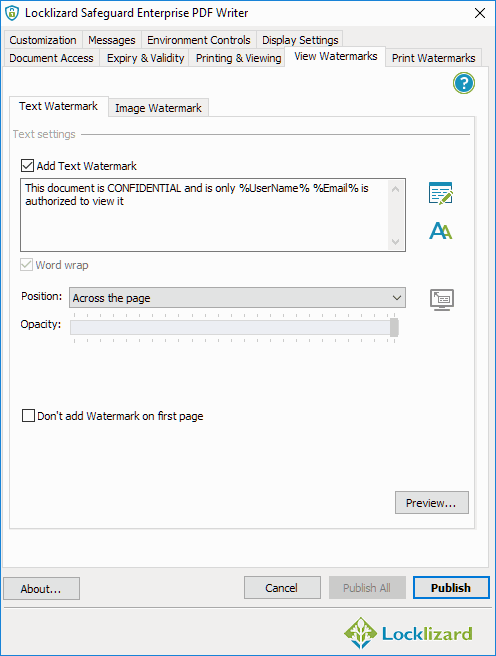
Adding a dynamic watermark to a document
We do understand the attraction of the invisible watermark as a concept. A watermark that in no way detracts from the viewing or reading experience would be ideal. However, the watermark still has to perform its intended purpose to be worthwhile.
Some watemarks such as PDF stamps, must be visible to convey a message, for example ‘Confidential’, ‘Do Not Distribute’, etc. – see How to insert a stamp in a PDF – so clearly invisible watermarks would be useless in this case.
We remain unconvinced that invisible watermarks are effective for protecting documents. This is especially true when compared with the use of a fully controlled secure PDF DRM solution, where visible watermarks can even deter cell phone camera copying.
Take a 15-day free trial and see for yourself how you can protect your PDF documents with non removable watermarks and security.

 What are we trying to achieve with watermarking?
What are we trying to achieve with watermarking? Invisible or hidden watermarks
Invisible or hidden watermarks Adding invisible watermarks and text files
Adding invisible watermarks and text files Hidden watermarks and images
Hidden watermarks and images How to make a PDF watermark not visible (hide watermark)
How to make a PDF watermark not visible (hide watermark) Invisible watermarks in Social DRM for ebooks
Invisible watermarks in Social DRM for ebooks Removing invisible watermarks
Removing invisible watermarks Visible watermarks
Visible watermarks Invisible vs visible watermarks as a copyright deterrent
Invisible vs visible watermarks as a copyright deterrent
