Cloud Document Collaboration & Document Security

How Cloud Document Security Works & Why it is Not Secure
Learn how cloud-based collaboration tools implement their security measures, what’s best, and how you can keep your sensitive information safe.
 Cloud collaboration and document sharing
Cloud collaboration and document sharing

For many businesses, cloud collaboration tools have become the de facto way to write, edit, share, and protect documents. The market has grown rapidly over the past decade, with cloud email and collaboration revenue growing from 8.7 billion in 2015 to a projected 93 billion in 2025.
Changes in how we work have been a driving force behind this growth. Workforces have become increasingly more distributed, and traditional on-premises tools and rights management systems have proven less efficient and more expensive. However, though cloud document collaboration tools provide upgrades in some areas, they come with significant security trade-offs that are often glossed over in marketing materials.
We’ll be discussing them in detail today, covering:
- What is cloud collaboration
- The most popular cloud-based collaborative solutions
- Is secure cloud-based document storage a myth?
- How cloud-based collaborative solutions stop sharing and misuse
- Why cloud document sharing is not secure
- How to keep cloud documents secure
- Why use Locklizard Safeguard for cloud document security
 What is cloud collaboration?
What is cloud collaboration?

Cloud collaboration allows team members to work together on documents and projects stored online, providing real-time access and editing capabilities from any device with an internet connection. This method promotes smooth cooperation, enabling multiple users to simultaneously view, edit, comment on, and share files while ensuring everyone can access the most up-to-date version.
 What are the best online collaboration tools?
What are the best online collaboration tools?
![]()
There are several big names in the cloud document collaboration space. They have broadly similar offerings, with the difference primarily concerning how large their suite of applications is:
- Google Workspace: Google Workspace is likely the most popular cloud document collaborative solution. It includes collaborative Google Docs, Sheets, and Slides, while bundling in email, Google Meet, forms, and cloud storage. Workspace is simple to use, priced fairly, and now comes with some useful AI tools.
- Microsoft 365: Microsoft 365 is a powerful suite offering both online and desktop applications. It includes the Microsoft Office suite such as Word, Excel, and PowerPoint, along with email (Outlook), cloud storage (Microsoft OneDrive), team collaboration platform (Teams), and document management (SharePoint). 365 offers a wide range of features and deep integration with Windows, making it a tempting investment for those already in the Microsoft ecosystem.
- Adobe Document Cloud: Millions of Acrobat users utilize Adobe Document Cloud to easily view and share PDFs with others. Users can create a document hub that enables easy access to create, edit, sign, and track PDF documents.
- Zoho Workplace: Zoho Workplace is a comprehensive and affordable suite of online productivity and collaboration tools. It includes collaborative document editing (Writer, Sheet, Show), email (Mail), cloud storage (WorkDrive), team communication (Cliq), and online meetings (Meeting). Zoho Workplace is a strong contender for small to medium-sized businesses looking for a cost-effective alternative to Google Workspace or Microsoft 365, offering a similar range of features at a competitive price point.
- Proton: Proton is a newcomer to the cloud collaboration space, focusing on privacy and security. At the time of writing, it offers word processing collaboration only (Docs) via its Proton Drive cloud storage. However, it also features calendar, email, VPN, Wallet, and password manager functionality, making it a respectable choice for more privacy-conscious businesses.
- General cloud storage providers: There are various cloud storage providers that offer the ability to collaborate on text documents live and share them. These include Box, Dropbox, iCloud, ownCloud, etc.
Most of these services emphasize security in their marketing material – referencing secure services, encryption, and multi-factor authentication. For most businesses, however, it is also important that documents are protected during use and against unauthorized sharing.
 Is secure cloud document sharing a myth?
Is secure cloud document sharing a myth?

Secure, cloud-based collaboration is very difficult to achieve because online collaboration tools have contradictory goals. They want to enable frictionless editing, printing, and sharing, but only for certain people. Allow access from any device or location, yet stop access from untrusted users. And so on. It is much harder to implement functionality and then stop people from using it than it is to simply not include it in the first place. And it’s even more challenging when you’re trying to do so in the browser.
 How do cloud collaboration tools stop unauthorized use?
How do cloud collaboration tools stop unauthorized use?
Cloud-based collaborative solutions are overwhelmingly delivered to users via the browser. This limits the methods available to enforce document and sharing controls because allowing a webpage to disable system functions would be a disaster for security. Developers, therefore, have four primary methods to enforce controls in the browser:
1. JavaScript
Developers use JavaScript to limit the browser features users can access. For example, they can disable the ability to right-click to prevent copying and pasting, control whether a document is editable, grey out certain buttons, and more.
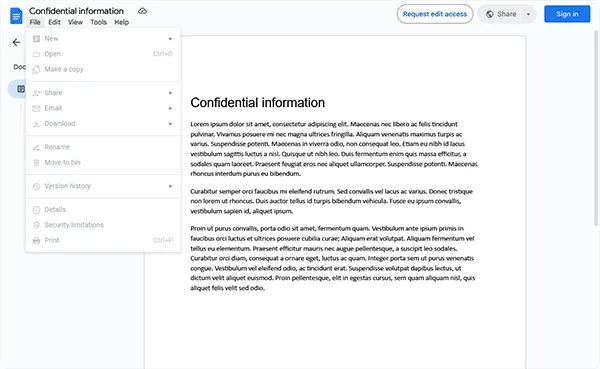
2. HTML obfuscation
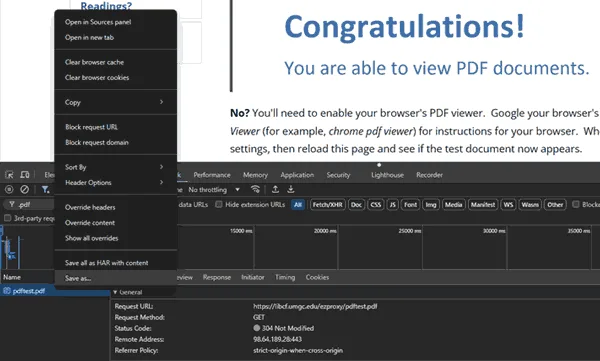
As most browsers have a developer mode where users can adjust code, obfuscation is often used to try to prevent them from finding which code disables certain functions, as well as prevent, for example, entire document files from being downloaded via the browser’s sources panel.
3. Login security
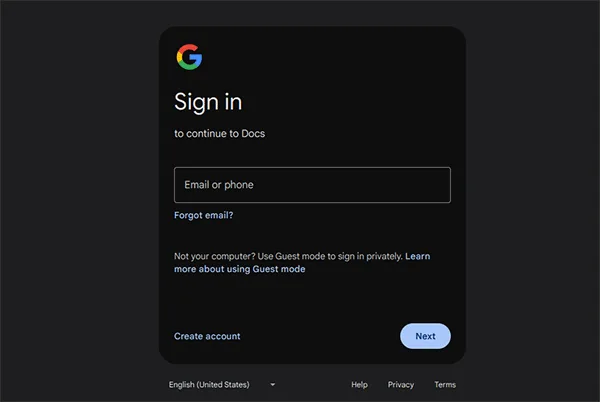
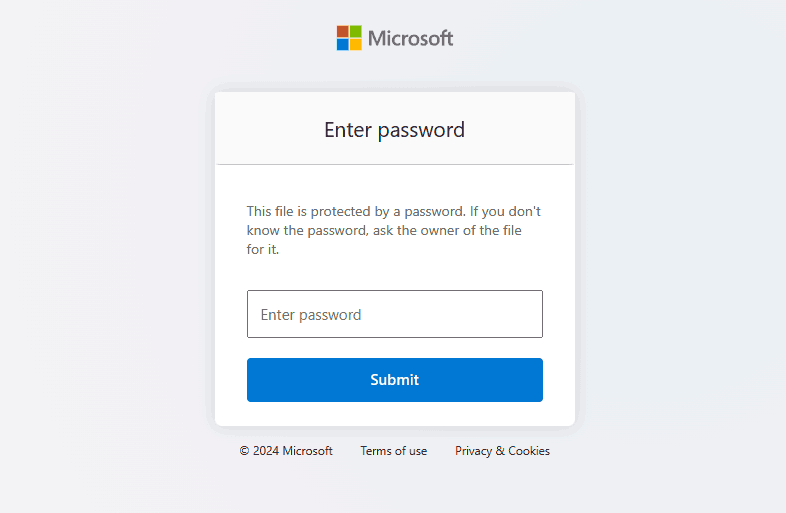
Cloud collaboration services seek to tightly control user accounts as access to an account grants access to all of its documents. Typically, this involves securing them with a password and two-factor authentication or, in more advanced scenarios, conditional access policies.
4. Password security

Some cloud providers allow you to set a password on shared documents and create expiring download links. Users have to enter a password to open the document, which adds an additional layer of security should the link to the document be leaked or an account the document is shared with be compromised.
 Why cloud document sharing is not secure
Why cloud document sharing is not secure
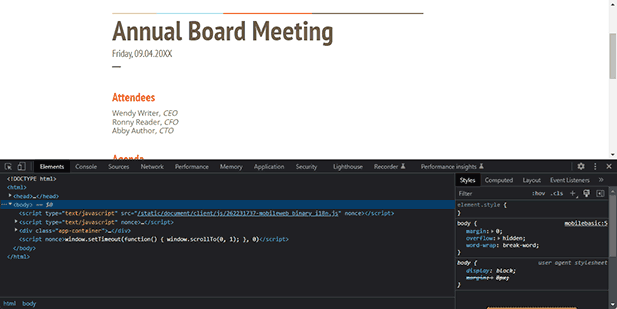
While cloud developers have many options to prevent sharing and misuse, browser-based techniques are rarely enough to prevent determined users from doing so. There are several threats to cloud based document management systems that the techniques above do not fully mitigate:
- Screenshotting the document
Browsers cannot reliably prevent screenshots or stop sharing of screens because they do not have enough control over system functions. As a result, all users need to do to share documents is screenshot them. They can manually screenshot each page or use an automated screenshot tool such as Fireshot to automatically screenshot the pages and then convert them into an editable PDF using OCR. - Sharing account credentials
Almost as simple as taking a screenshot is just sharing logins with somebody else. Most cloud services only use two-factor authentication for additional login security. While 2FA provides some protection against outside attackers, it does nothing to stop an internal user from leaking their information. They can provide a 2FA code just as easily as they can offer their username and password. - Bypassing JavaScript controls
JavaScript executes partially on the user’s PC. As a result, it is possible to interfere and rewrite it to enable disabled functions such as printing, editing, and copy-pasting. For some cloud services, users can even download extensions that do all of this for them. - Printing to file drivers
Sometimes, you need to allow users to print, but still don’t want them to edit or make digital copies. A few cloud collaboration platforms let you enable only printing, but it is rarely secure. Web platforms cannot stop users from printing to file drivers rather than a physical printer, and this allows printing to a PDF file, which can then be shared and edited at will. - Keeping expired or revoked documents
The cloud is often seen as a good way to expire or revoke documents – you disable downloads for the document’s lifecycle and then turn off sharing on the original file to remove it from users’ libraries. However, because users have many options to make a local copy of the document beyond a ‘download’ button, this is a misconception. Unless you are tracking down every screenshot, or file driver print, copies of your document are likely to remain in circulation. - Account compromise
Though implementing 2FA makes account compromise less likely, it’s still a very real possibility. Attacks such as session hijacking bypass 2FA. While adding passwords to documents helps with this, they can only be applied to documents that have been shared with the user, not ones they have created. Additionally, setting a unique password for each document and communicating them securely to intended users isn’t feasible for many organizations, leading to poor password hygiene. This is compounded by the fact that trying different document passwords is often not rate-limited, enabling automated attacks to guess insecure passwords. - Server compromise
Though cloud providers put a lot of resources into their cloud security, they are not infallible. There is always the risk that attackers will compromise the servers of a cloud provider and gain access to documents. This is why it’s important to choose a service that encrypts your files in transit and at rest. Even then, however, you will have to trust the provider’s word that they do so securely with no temporary files left over or other vulnerabilities.
Ultimately, then, while cloud collaboration services provide some degree of security, you’ll have to take things into your own hands if you want to be confident that sensitive and confidential documents stay safe.
 How to keep cloud documents secure
How to keep cloud documents secure

The best way to ensure their security when a user account or server is compromised is by applying your own encryption. Encrypting documents locally before uploading them means that attackers cannot access them even if they hack your account or the provider’s servers. Your encryption keys are stored separately from the cloud provider and documents can never be accessed by them.
Encryption alone won’t stop unauthorized sharing and misuse. T o prevent this, a digital rights management (DRM) system is needed. Secure DRM viewer applications can leverage local printing, editing, and screenshot controls that cannot be easily bypassed.
The downside of using encryption or DRM, of course, is that previews and collaboration features will not work when you upload the document to the cloud. Providers never have access to unencrypted files – a necessary limitation for the best security. However, this does not mean that collaboration is completely out of the question. A document DRM solution such as Locklizard still allows users to comment on and highlight documents locally and share these annotations with others.
 Why use Locklizard for secure document sharing?
Why use Locklizard for secure document sharing?

Locklizard Safeguard ensures your documents are protected in the cloud and after downloading. The following features enable complete protection regardless of your cloud storage provider or workplace model:
- AES encryption: Encryption ensures you don’t have to rely on a cloud provider or account security to keep your sensitive documents safe. Attackers will see only a jumble of numbers and letters as they need a valid license file installed on their device to decrypt the file. Licenses are sent to users at the point of distribution and are single-use by default, so they cannot be shared. Decryption keys are encrypted, not exposed to the user, and not uploaded with the document, leaving attackers with no route to extract the information.
- Strong document controls: Locklizard uses a local viewer application that enforces printing, editing, saving, copy-paste, and screenshot controls. It enforces controls that cannot be easily bypassed or removed and does not use JavaScript or passwords.
- Effective expiry and revocation: Apply additional expiry options (date, number of days since first open, after n prints, after n views) or revoke protected documents instantly, regardless of their location. Rather than trying to remove all copies of a file, Locklizard makes it so users can no longer decrypt the document, rendering it useless. Due to strong copying controls, you can also be sure that users have not made additional unprotected copies without your consent.
- Dynamic watermarks: Dynamic watermarks can display a user’s name, company, and other information when they open or print it. This strongly dissuades the sharing of printed copies or taking pictures of the screen with an external camera.
- Lock access to authorized devices and locations: As well as locking documents to devices, you can set specific IP addresses and locations where sensitive documents will be accessible.
- Logging: Track who viewed or printed a document, when, and from where, remaining compliant.
 Collaborating on documents with Locklizard
Collaborating on documents with Locklizard
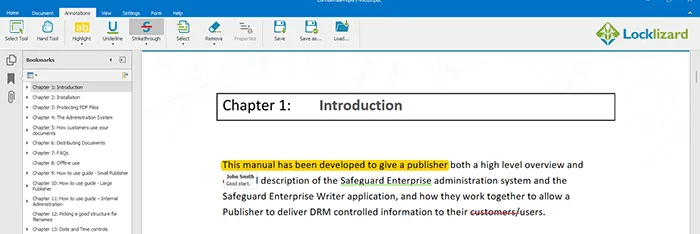
Locklizard Safeguard does not support live document collaboration, as live collaboration makes it impossible to prevent misuse without significantly degrading usability. Users are encouraged to create first drafts of sensitive documents with parties they 100% trust in a secure environment. After protecting them with Locklizard, they can distribute to a broader subset of users and get feedback using Locklizard’s highlighting, commenting, underlining, and strikethrough.
Users save their annotations to a separate file and provide this for others to load into their viewer application and expand. This is an excellent way to get suggestions from multiple parties while preventing unauthorized sharing and misuse.
To try this for yourself, take a 10-day free trial of our DRM software.
 FAQs
FAQs

What can cloud collaboration be used for?
Cloud collaboration tools can be used for various tasks, including project management, slideshows, text, graphics, 3D modeling, spreadsheets, meetings, or even just standard file storage. The vast majority of cloud collaboration, however, happens on traditional text documents.
How vulnerable is the cloud?
The vulnerability of the cloud is entirely dependent on how secure your provider and account is. You could have the best password in the world but a bad provider and your data would be unsafe and vice versa. As a general rule, however, providers that offer end-to-end encryption are more secure. For the best security, encrypt documents yourself before you upload them – then you know an attacker will not be able to access your files without first gaining access to the device that holds your decryption keys.
Where is the safest place to store files?
On your local machine, which is kept at home, behind a locked door, encrypted. Failing that, storing them anywhere with strong encryption should be okay as long as your decryption keys are sufficiently protected.
Can anybody see my Google Docs?
Only if you set the sharing mode to “Anyone with the link can view”. However, you should be aware that even if you share a link with a specific user, they can download your Google Doc to share it with whomever they like. See how to share Google Docs securely for more information.
How safe are my documents on Google Drive?
Not especially. It only takes your user account being hacked, Google being hacked, or somebody you shared a document being hacked for your documents to leak. Users you share with can also easily download documents you share with them to share with unauthorized parties.
What is the most secure cloud storage for financial/legal documents?
None of them are particularly secure, as mentioned above, but if you must go the cloud route, choose a provider that uses end-to-end encryption and has regular public security audits.

 Cloud collaboration and document sharing
Cloud collaboration and document sharing What is cloud collaboration?
What is cloud collaboration? What are the best online collaboration tools?
What are the best online collaboration tools? Is secure cloud document sharing a myth?
Is secure cloud document sharing a myth? How do cloud collaboration tools stop unauthorized use?
How do cloud collaboration tools stop unauthorized use? Why cloud document sharing is not secure
Why cloud document sharing is not secure How to keep cloud documents secure
How to keep cloud documents secure Why use Locklizard for secure document sharing?
Why use Locklizard for secure document sharing? Collaborating on documents with Locklizard
Collaborating on documents with Locklizard FAQs
FAQs
