Azure Rights Management: How good is its protection?

How secure is Azure Rights Management for information protection?
In this blog, we aim to help you make an informed decision by explaining how Azure Rights Management works, the protection it provides, and what secure alternatives are available.
 What is Azure Rights Management?
What is Azure Rights Management?
Azure Rights Management is the component of the wider Azure Information Protection suite that protects files and emails when they are shared on or offsite. It specifically focuses on ensuring ongoing access for authorized users while disallowing unauthorized ones.
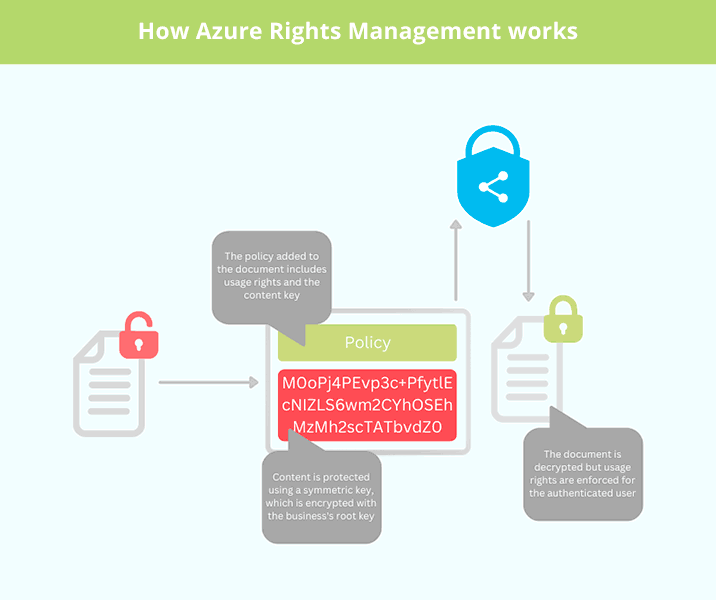
Though Azure Rights Management used to protect only Office files its functionality has since been extended to include images, raw files, Adobe creative cloud files, and Autodesk Design Review. Once a file has been protected with Azure Rights Management, the authorization policies stay with it regardless of whether it has been copied away from the corporate network.
Azure Rights Management supports collaboration on shared Microsoft 365 files, even if they are not part of the organization. However, the collaborator must have a Microsoft 365 or Azure AD account for automatic functioning.
 | Azure Rights Management vs Microsoft Rights Management vs Azure Information Protection |

Microsoft is no stranger to rebrands, but the names behind its rights management protection offerings are especially confusing. You will have heard names like Microsoft Azure Rights Management, Azure Directory Rights Management (AD RMS), Windows Rights Management, Microsoft Rights Management (services), and Information Rights Management (IRM), bandied about with little elaboration.
So, are all of these the same thing? Not exactly. To try to put it as succinctly as possible:
Microsoft Purview Information Protection (formerly Microsoft Information Protection)
A wide-reaching tool designed to help organizations discover, classify, protect, and govern sensitive information regardless of where it travels.
Azure Information Protection (AIP)
A component of Purview Information Protection that extends the labeling and classification system with a unified labeling client, on-premises scanner, and SDK.
Information Rights Management
The Office 365 implementation of Azure Information Protection.
Azure Rights Management Service (formerly Windows Azure Active Directory Rights Management, RMS Online)
Also known as Azure Cloud Security. The cloud-based protection used by Azure Information Protection to encrypt and add policies to labeled files.
Active Directory Rights Management Services (AD RMS)
The current on-premises version of Azure RMS. It is not well-suited to sharing with third-parties and comes with no default rights policy templates.
Microsoft Rights Management Services
The collective name for Azure Rights Management Service and Active Directory Rights Management Service.
If you need more clarification, Microsoft’s terminology page may be of use.
 | Azure Rights Management: Is it effective? |
Now we’ve discussed what Azure Rights Management is, you should be in a better place to understand its security. Or, rather, the lack of it. For a deeper explanation, we can defer to the paper How to Break Microsoft Rights Management Services by researchers at the University of Bochum. It concludes:
“Our attacks can remove the whole protection of a file or modify the content without breaking its integrity, thus creating arbitrary files in the name of a different user… Microsoft RMS is widely used in enterprises’ systems such as banks and HSMs. Since Microsoft also includes it in its Azure platform, our attacks are even more severe. We only applied the attacks on Office documents, but the concept works on arbitrary files.”
In other words, you can’t lock a Word document from editing or other Office documents from editing by those who can view it. Users can bypass Microsoft information rights management and gain full control, including the ability to copy, modify, print, and share. This attack can even be automated and its code was freely available on GitHub.
Microsoft’s comment on this attack? That this is simply a limitation of policy-driven document enforcement, and there’s not much they can do about it.
“Policy enforcement capabilities, such as the ability to prevent printing or modifying content to which the user has legitimate access, are not guaranteed by cryptography or other hard technical means”, Microsoft stated.
What Microsoft seems to be hinting at here is that no policy system is infallible. At the very least, users can always take a picture of their screen or copy out the document by hand. It is more about how difficult and time-consuming the removal of protection is to achieve.
So, how easy is it to bypass Microsoft’s information rights management? Well, it’s certainly not as popular or developed as, say, removing e-book DRM, or cracking a password protected PDF, but a simple search for “Microsoft RMS attack” or “break Microsoft RMS” will return plenty of useful results. The tools used in the research study are still available to all and results can be achieved relatively easily with the provided .exe file. Users can even modify the document and re-protect the file as if it was created by the original author.
Documents protected using Azure Rights Management or Microsoft Rights Management services can still be leaked, then, and could play a dangerous role in spearphishing attacks. Should a hacker compromise one person with view access, they would be able to modify the document (replacing payment details with their own, for example), and potentially forward it on with nobody the wiser.
 Other Azure RMS considerations
Other Azure RMS considerations

When evaluating a document or information protection solution, it’s of course about more than just what it can do. You must consider how it fits into your existing infrastructure, whether it meets compliance standards, and cost/ROI. If you are deeply invested in the Office ecosystem, then perhaps these are already covered. A Microsoft 365 Enterprise bundle will provide you with Azure Information Protection for relative convenience and good value provided you can stomach the (seemingly very serious) gaps in document security.
If, however, your company does not create and distribute many of its documents in Microsoft formats, it starts to make less sense. Pricing for those outside Microsoft’s enterprise plan (as an add-on to Office 365) is $2/user per month for the premium Plan 1 and $5 for Plan 2. For reference, without P2, you will have to manually label and classify all of your documents.
In fact, you will have to do some manual policy creation and classification/labeling regardless, as automatic classification only works under some circumstances. This will represent a significant workload that could be expensive to set up and maintain.
Then there is the question of external sharing. As mentioned earlier, collaborative sharing requires a Microsoft 365 account or Azure AD account, as well as the relevant clients for them, which need admin privileges to install. The signup process can be confusing for external users and lead to errors that increase the load on the IT department. Overall, this may not be feasible for some partners or for your business.
 | Simplify rights management with Locklizard |

Though Azure Rights Management may be the right choice for some companies, for many it’s just too unwieldy, ineffective, and expensive. If it is just document protection you need, then you should be looking at digital rights management (DRM) tools instead.
Locklizard Safeguard allows you to protect documents in the universal PDF format so that nobody can edit them and they cannot be shared, printed, or screen grabbed without your permission. Through a combination of AES 256-bit encryption, licensing controls, and a secure viewer application, Locklizard avoids the security pitfalls of Azure information protection and provides true protection for documents that are shared both internally and externally.

The best part? It’s simple to use. Here’s what the document protection process looks like, from start to finish:
- You encrypt a PDF on your local PC and add any DRM controls you desire. These can include anti-screenshotting and copying techniques, printing controls, watermarks, device/location locking, and more.
- The protected file is saved to your disk and a record of the document is recorded on the Admin System.
- You create a user account for each person who you want to be able to view the document.
- Users receive an email with a license file and a link to download the Safeguard secure viewer app.
- After installing the viewer, the user clicks the license file to activate it on their PC. Once activated, the license file cannot be registered elsewhere (unless otherwise specified).
- You choose which documents users can access via the Admin System.
- You send the encrypted PDF file to users just like any other file (via email, file sharing, messaging, etc.).
- The user opens the PDF with their secure viewer application.
Using the Locklizard e-commerce API and command line, the admin work can be automated, further streamlining the process.
When protecting a PDF with Locklizard, you additionally gain access to the following functionality:
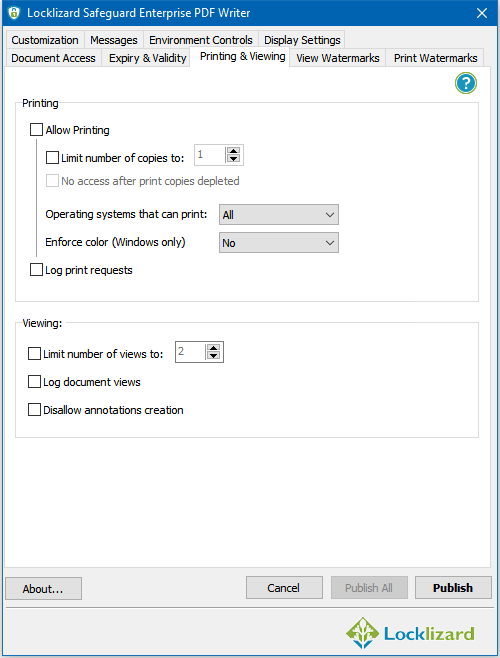
- Apply dynamic watermarks to your documents that automatically insert the users’ information, the date/time, etc. when the document is opened or printed.
- Document expiry based on date, days since first open, the number of prints, the number of opens, etc.
- Revoke documents manually and instantly even if they are stored outside of an organization’s boundaries
- Document open and print logging for security, regulatory requirements and compliance
- Lock PDF files to devices, countries, and IP addresses (e.g. office use only, no use in non-licensed countries)
- Limit printing to black & white or low-resolution copies
For more information on preventing unauthorized access and use of your documents see Enterprise Rights Management or take a 10-day free trial of our PDF DRM software.
 FAQs
FAQs

What is Azure Information Protection?
Azure Information Protection (AIP) is a cloud-based solution which classifies and protects documents and emails in SharePoint and Outlook.
Do I have to create policies to protect documents using RMS?
Yes. You have to do some manual policy creation and classification/labelling since automatic classification only works under some circumstances.
Do I have to create policies in Locklizard?
No. There are no policies to create or other complex configuration. You select usage rights when protecting a document and use the admin portal to assign access.
What is IRM or Information Rights Management?
IRM is a term used to apply digital rights to information. It is mainly used as a term for the protection of Enterprise documents. See What is IRM?
Do I need to purchase a subscription to protect company data using Locklizard?
You can purchase a subscription or a perpetual license either hosted by us (cloud service) or using on-premises servers. There are no yearly fees for on-premise systems.
Does Locklizard protect Microsoft Office file types?
No, Locklizard provides corporate data protection only for PDF files.
Does Locklizard use passwords for document protection?
No, we use a licensing system with transparent and secure key management. There are no passwords for users to enter, share or remove.
How does Adobe compare to Microsoft Azure security & information protection for Office 365?
Both provide protection of Microsoft Office 365 files but Adobe Experience Manager Document Security has many more security issues.
Is Microsoft Digital Rights Management the same as Azure Rights Management or DRM?
Essentially they use the same technology. Azure Rights Management or Azure DRM is the term used for the online protection of Office files, wheras Microsoft Digital Rights Management refers to the protection of offline versions.

 What is Azure Rights Management?
What is Azure Rights Management? Other Azure RMS considerations
Other Azure RMS considerations FAQs
FAQs
