PDF Password or Certificate Encryption?
Certificates or Passwords for PDF encryption – which is more secure?
Should you use passwords or certificates to protect confidential and sensitive business documents from leakage and misuse? What’s the best way to encrypt sensitive content?
- Choosing the right PDF protection for your business
- How does PDF encryption work?
- PDF encryption using passwords
- PDF certificate encryption
- What about PDF restrictions to stop editing, copying, printing?
- Protecting PDF files without passwords or certificates
- Are passwords, certificates, or neither best for PDF encryption?
 Choosing the right PDF protection for your business
Choosing the right PDF protection for your business
Whether you choose one protection method over the other is determined by your reason for protecting PDF files in the first place. The content may be commercially sensitive or confidential, such as trade secrets or intellectual property, or it may be personal data that must comply with regulations like HIPAA or GDPR. Alternatively, you may have a requirement to share documents within your organization securely or want to enable secure external document sharing with third parties. Perhaps you have revenue-generating content (ebooks, training courses, reports) and want to ensure it’s not readily pirated.
Regardless, it makes sense to ensure that the method you use to encrypt PDF files cannot be readily bypassed or removed – otherwise, there’s not much point in applying it to begin with.
 How does PDF Encryption work?
How does PDF Encryption work?

When you use PDF encryption software, a certificate or password is usually used to protect the random key that’s generated. The key is the component that’s actually used to encrypt and decrypt the PDF. If you choose AES 256-bit encryption, for example, a 32-character random key is used to encrypt the PDF, scrambling its contents. The password or certificate stops that key from being made readily available. After this point, only the entry of the correct password or the correct private key (in the case of certificate encryption) will decrypt the contents and enable access.
 PDF Encryption using Passwords
PDF Encryption using Passwords
The ability to encrypt a PDF with a password is included with all PDF editing software. This is easily the most popular way to protect PDF files: it’s part of the PDF standard, is readily available to implement in PDF applications, and many online PDF protection sites let you do it for free. But how strong is this protection, really?
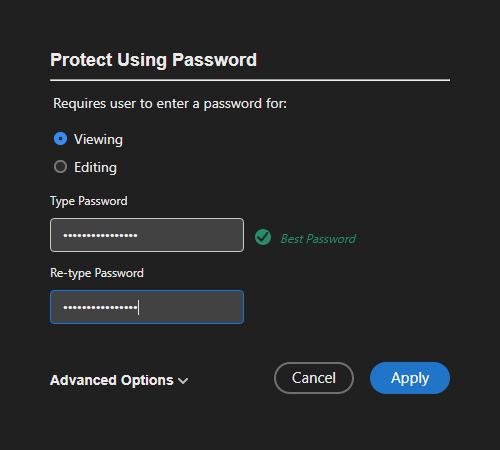
Encrypting a PDF with a password using Adobe Acrobat
 Is PDF password encryption secure?
Is PDF password encryption secure?
To answer that question, you need to keep the following in mind:
- Anyone you give the password to can decrypt the PDF and remove all protection.
You must provide users with the password if you want them to open the PDF document, so you have to trust them not to share the password or unprotected PDF file with others. - Users can share the PDF and the password with others.
You cannot prevent users from sharing PDF files and passwords with others because there is no security that locks keys to machines or devices. - You have no idea how many times your ‘protected’ PDF file has been shared with others.
The password is unique to the PDF file and not to the user, so you cannot track who is using it. - A password protected PDF can be broken with password crackers.
Even if a user does not know the password to the PDF file, they can use a freely available password recovery program or cracker to carry out a ‘brute force’ attack on the password. The simpler the password (shorter and less complex) the easier and quicker it is to crack. - You have to manage a list of PDF documents and their passwords.
Password management is a pain in the butt. For obvious reasons it is not a good idea to use the same password for every PDF file, so you need to keep a list of documents and their corresponding passwords and make sure that is securely stored. This is also true for users that receive password protected PDF files. - You need to make passwords strong, yet easy for users to remember.
This is in itself a usability challenge – how many people can accurately type in a 16-character password or more consisting of upper and lower, numbers and special characters? - You have to find a way to securely distribute the passwords to others.
Passwords need to be sent separately from the protected PDF documents and using a secure form of distribution. This maybe using a file or email encryption program to securely send them to others. - You need to avoid backwards compatibility with weak implementations.
For example, if you are using Adobe Acrobat to encrypt PDF files then you should choose the compatibility option “Acrobat X or later”. This is because in Acrobat 9, Adobe made it much easier to crack passwords with brute-force attacks, making just one call to verify the password for AES 256-bit encryption instead of the 71 calls used in Adobe 8 using AES 128 bit.
So password protection might be a readily available way to encrypt PDF files, and there is no complex registration process that you need to support such as with certificates, but in reality it is pretty useless.
If you still want to use a password to encrypt a PDF, then follow the guidelines for choosing a strong password to protect PDF files so you can create one that can’t be brute-forced easily..
 PDF Certificate Encryption
PDF Certificate Encryption
An alternative to PDF password encryption is to use certificate-based encryption. This is generally a bit more secure than passwords.
 What is PDF certificate encryption?
What is PDF certificate encryption?
Certificates are part of PKI (Public Key Infrastructure). PKI is a system used to identify the creator of the encrypted file and the public identity of the recipient without allowing that information to be used to break into the system readily.
A certificate holds a user’s public key and information about when it was generated, when it expires, and what it can be used for. Certificates can be signed by a Certificate Authority (CA) who validate the user, or they can be self-signed and it is up to you to trust that the certificate belongs to the right person. Most organizations generate their own certificates unless they want to use them for secure communications with third parties.
When you use an application to generate a key pair, you will get a certificate containing your public key (this is given to others to encrypt information for you), and a private key that you do not disclose. The private key is used to decrypt information and digitally sign files.
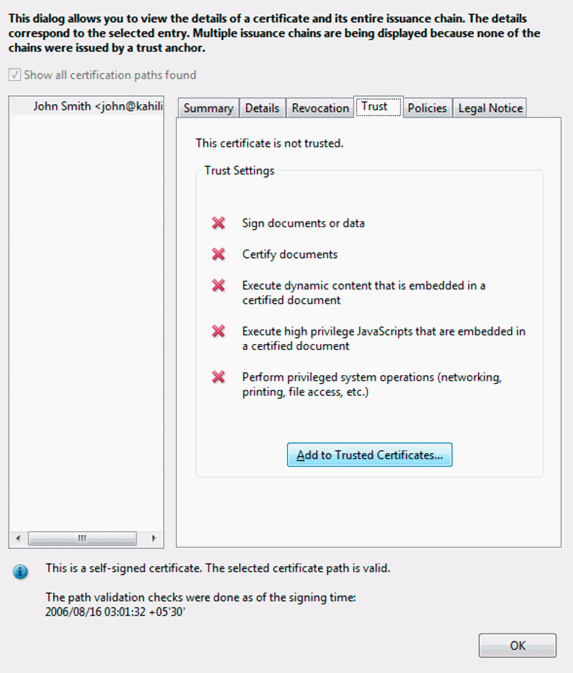
Cerficate Import: Encrypting a PDF with a certificate using Adobe Acrobat
When using certificate encryption, the PDF file is still protected using a password (for example, if AES 256-bit encryption is used, then a random 32-character password is used to protect the PDF document), but that password is encrypted using the recipient’s public key. Only the corresponding private key can decrypt it.
So, certificates are just a secure key exchange mechanism – there are no passwords to distribute or for users to share with others.
 Digitally Signing PDF files
Digitally Signing PDF files
Another advantage of certificate encryption is that users can digitally sign a PDF. There are two reasons for doing this:
- to assure recipients that the document came from you.
- to verify that it has not been tampered with.
However, due to a weakness in signature validation implementations, PDF documents can be altered and PDF Readers don’t realise that it has been tampered with.
Users use their private key to digitally sign PDF files, and recipients verify the signature using that users’ public key.
 PDF encryption with certificates vs passwords
PDF encryption with certificates vs passwords
The use of certificates is more secure for distributing PDF files than passwords since:
- you don’t have to worry about how to transmit the password securely to other users.
- users are unlikely to share their private key with others and so only the authorized recipient can decrypt it.
- there are currently no password cracking applications that can crack PDF files that have been encrypted with certificates.
- certificate encryption systems are highly resistant to attack by anyone who does not have an appropriate key to decrypt the file.
- PDF files can be digitally signed so you know who they originated from. This may be important for example if users are downloading documents from a cloud server.
However, just as with password encryption, once a user has decrypted the PDF file, they can do what they want with it, including saving it to an unprotected file.
They also have other disadvantages:
- If you are protecting PDF files for internal use, users must have key pairs already generated, and ideally, certificates should be stored in a directory server so they are easily accessible for use.
- You need to put into place a system for revoking certificates and generating new ones when they expire. So there is a management overhead to consider.
- If you are selling revenue generating content then certificate encryption is unlikely to be a good solution for your business. This is because you need the user’s certificate before you can encrypt PDF files for them.
 What about PDF restrictions to stop editing, copying, printing?
What about PDF restrictions to stop editing, copying, printing?
 Whether you encrypt a PDF with a password or a certificate, you can apply PDF restrictions (to stop users editing, copying, and printing content) and enter an additional password (a permissions password) to prevent users removing those restrictions – well, in theory anyway.
Whether you encrypt a PDF with a password or a certificate, you can apply PDF restrictions (to stop users editing, copying, and printing content) and enter an additional password (a permissions password) to prevent users removing those restrictions – well, in theory anyway.
There is only one thing you need to know about applying PDF restrictions – they are completely useless:
- Once a user can open the PDF, they can easily remove the restrictions by using freely available password cracking or recovery tools.
- PDF restrictions are not enforced by all PDF Readers.
Some PDF Viewers and other applications completely ignore them, so users can just use Mac Preview, Google Docs, or the appropriate PDF Reader to view ‘protected’ PDF documents, and no restrictions will be applied.
Even worse, users could end up compromising your PDF documents by uploading them to cloud servers in order to remove the restrictions. You have no idea then who has your documents. So you have added ‘protection’ that has actually made it more likely that your PDF files will be compromised.
So, unless you don’t have anything better to do, don’t bother adding PDF restrictions. If you want to read more about how the Adobe Acrobat Security Handler works and why PDF restrictions are totally useless, see PDF Security Issues.
 Protecting PDF files without passwords or certificates
Protecting PDF files without passwords or certificates
So, if PDF passwords and certificates don’t provide much protection, what can you do to protect PDF files from being opened by unauthorized users and misused by authorized ones?
A different approach to protecting PDF files is using a PDF DRM system that uses encryption and licensing controls. Locklizard, for example, uses this approach to securely transfer document decryption keys to authorized users’ devices and then store them in an encrypted keystore that is locked to the device. This removes the need for both passwords and certificates – PDF files are transparently decrypted if the user has the correct key made available to them.

Encrypting a PDF without passwords or certificates using Locklizard Safeguard PDF DRM
PDF DRM systems also have the advantage over PDF restrictions in that controls cannot be easily removed as they are persistently enforced by the application. Some systems use plugins to Adobe to achieve this, some use browser-based systems where users must log in to view protected PDF files, and others use dedicated secure PDF Readers. A dedicated PDF reader is a more secure approach since it has control over the environment – plugins only work within the application so you cannot prevent screen grabbing and other functionality that may be used to bypass the PDF protection, and users can easily share login credentials with others in browser-based systems and manipulate and bypass the JavaScript protection.
Commonly, PDF DRM systems will enable you to:
- Disable PDF printing
- Stop screenshots
- Expire PDF files
- Lock PDF files to devices and locations
- Restrict PDF use – copying, editing, saving to unprotected formats
- Add dynamic watermarks that cannot be removed
- Track PDF opens and prints
One of the most important features of a PDF DRM system is locking PDF files to devices so they cannot be easily shared with others. Combined with transparent key delivery, this can provide the ultimate in PDF protection.
A WORD OR WARNING: make sure any PDF DRM system you purchase does not force users to remove or lower their security for it to work. Some DRM plugins do this. Other PDF DRM solutions force users to enable JavaScript in their PDF Reader. This is a really bad idea since hackers send out malicious PDF files that use JavaScript to gain control of user’s computer systems. The result of a user clicking on a malicious PDF file and it causing them harm could therefore result in you being sued.
 Are passwords, certificates, or neither best for PDF encryption?
Are passwords, certificates, or neither best for PDF encryption?
In summary, there are many ways you can protect PDF files, from using password and certificate encryption, digital signatures, licensing, and DRM controls. The method you choose for your business will depend on how confidential, sensitive or valuable your PDF documents are and whether you just want to securely send PDF files, protect them while they are being stored, share PDF files securely, sell them, or just control how they are used.
Clearly passwords or certificates are of no use if you want to enforce PDF restrictions such as stopping editing, copying, and printing, since they can be easily removed.
What you need to bear in mind is if the protection can be easily bypassed or removed then there is no point in applying it to begin with.
If you want to protect PDF files without passwords or certificates, stop sharing, and enforce edit, print and copy restrictions then take a free 10 day trial of our PDF DRM software.
 FAQs
FAQs
What are the benefits of using a certificate to secure a PDF file?
Using a certificate to secure a PDF offers stronger protection than passwords. It leverages public-key encryption to prevent password sharing, while allowing for individualized permissions for each recipient. However, as outlined above, Adobe’s implementation of PDF certificates has several key flaws.
Is it possible to add multiple passwords or certificates to a PDF file?
Yes. You can add multiple certificates to a PDF file for different recipients. It’s also possible to add both an open and permissions password to a PDF.
Can you password protect a certified PDF?
Yes, but it will replace the certificate protection.
How do you digitally sign a PDF with a certificate?
Press “Protect > Use a certificate” in the tools pane, then press “Certify (visible signature)”. Choose where you want your signature, select your certificate, and choose “Continue”, followed by “Sign”.
Can I sign a PDF without a certificate?
Yes, you can do this by selecting “Fill & Sign” in the sidebar, selecting the pen icon, and clicking anywhere on your document. However, it does not provide any inherent security.

 Choosing the right PDF protection for your business
Choosing the right PDF protection for your business How does PDF Encryption work?
How does PDF Encryption work? PDF Encryption using Passwords
PDF Encryption using Passwords
 PDF Certificate Encryption
PDF Certificate Encryption What is PDF certificate encryption?
What is PDF certificate encryption? Digitally Signing PDF files
Digitally Signing PDF files PDF encryption with certificates vs passwords
PDF encryption with certificates vs passwords What about PDF restrictions to stop editing, copying, printing?
What about PDF restrictions to stop editing, copying, printing? Protecting PDF files without passwords or certificates
Protecting PDF files without passwords or certificates Are passwords, certificates, or neither best for PDF encryption?
Are passwords, certificates, or neither best for PDF encryption? FAQs
FAQs
