Google Workspace security – is it secure?

How good is Google Workspace security & privacy
The key security features of Google Workspace, plus the problems with data protection measures such as encryption, document restrictions, DLP and access rules, and how you can address them.
Google Workspace has grown from a management tool tested at a small community college to a full suite of cloud-based collaboration and productivity apps with over three billion users. Its success in the enterprise and education spaces has been propelled partly by the reputation Alphabet Inc has built for safety and data protection – but how secure is Google Workspace really? We’ll examine it from a document security perspective in this blog.
 Google Workspace security
Google Workspace security

Google Workspace provides a good range of security features to protect data such as 2-step verification for login, enforced SSL connections, client side encryption (CSE), security alerts and reports, password monitoring, data loss prevention (DLP) and context aware restrictions to name a few.
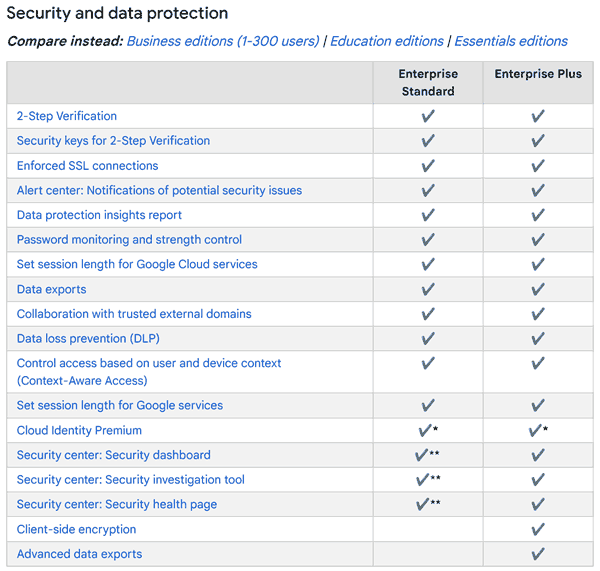
So, at first glance, it looks like a secure system for document collaboration. In practice, however, how do all these components protect your organization’s data?
 Google Workspace & encryption of data
Google Workspace & encryption of data
The first thing to discuss regarding Google Workspace is its encryption since there is some confusion here. Some users aren’t sure if their emails and documents are encrypted, which type of encryption Google uses, and how secure it is.
Is Google Workspace email encrypted?

There are two options for Google Workspace encrypted email, which are the same as Gmail encryption: the default TLS encryption and S/MIME. TLS encrypts the communication channel, protecting data in transit and preventing spoofing attacks. The email is decrypted once it is delivered to email addresses via the mail server.
S/MIME is much better because it provides end-to-end encryption. It encrypts emails individually when they are in transit and at rest on the mail server. If there is an attack on the mail server, the emails and their attachments are usually still safe, with decryption occurring only at the client’s inbox when a valid private key is present.
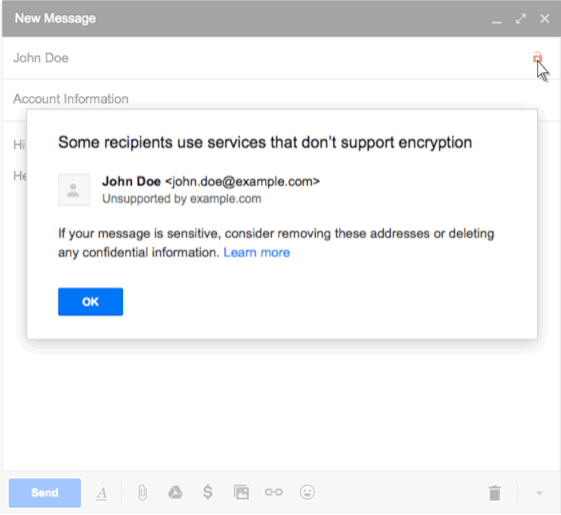
Both types of encryption only work if all parties’ email service/mail server supports them. With S/MIME it gets more complex, with all parties required to exchange keys in advance for encryption to work and set up in the admin console. There is also an additional cost if certificates are purchased via a certificate authority.
Regarding document security specifically, both of these options are of limited use. While they will protect attachments in transit and S/MIME at rest, most users will immediately download attachments to their PCs. At this point, they’ll be unencrypted and can be intentionally or unintentionally shared at will. We explain this in more detail in our blog on gmail attachment encryption and how to send attachments securely.
What about Gmail confidential mode?

Gmail confidential mode attempts to address what happens after an email attachment lands in a recipient’s inbox.
However, as covered in our Gmail confidential mode blog, it is a half-hearted effort. In our testing, it was simple to bypass controls and create unprotected versions of PDF files, copy & paste from documents, and print. Users can easily make copies of the email body, making confidential mode a waste of time overall.

Is Google Workspace encrypted?

Unlike its emails, Google Workspace documents are encrypted in transit and at rest. However, there are a few key points to consider regarding Workspace’s encryption.
- Google uses a good encryption algorithm to secure its documents, AES-256. However, encryption is still per account rather than per document; ergo, if an account’s encryption key is compromised, all its documents are.
- Google’s cloud key management service allows you to use your own encryption keys at rest (both hardware and software keys are supported) rather than Google managing them for you. Google calls this client-side encryption or CSE, and it enables you to gain greater control over how encryption is managed. However, it costs extra (only Enterprise Plus plans provide client-side encryption) and requires additional configuration and management overheads since you have to store and manage keys securely.
- Encryption is not a substitute for the flaws we mentioned earlier with document controls. Google Workspace encryption does not protect documents in use, and therefore does not stop authorized users from sharing, printing, screenshotting, etc.
 Does DLP and Context-Aware Access prevent data loss?
Does DLP and Context-Aware Access prevent data loss?
![]()
Google’s DLP or Data Loss Prevention enables you to create and apply rules which control the files and content that users can share outside the organization.
Context-Aware Access enables you to create granular access control security policies for apps based on attributes such as user identity, location, device security status, and IP address.
Both of these security features are available in the Enterprise editions and help to prevent leakage of sensitive data and confidential information.
However, apart from being a large management overhead to configure and manage, restrictions or rules can often be easily bypassed by exploiting weaknesses in document controls such as those enforced by Google Docs Security. Users can then share data with unauthorized users outsides the confines of both systems.
DLP and context-aware access can therefore only be made effective if all systems that make up the overall protection solution adequately enforce security measures to prevent copying and sharing of information.
 How secure is Google document cloud?
How secure is Google document cloud?

Another major component of Google Workspace is its cloud-based document collaboration tools. Google Docs, Sheets, and Slides conveniently allow users to work together from any device, anywhere. Google’s browser-based approach is key to this convenience but is also the Achilles’ heel in its security. Though Google’s marketing material claims that it’s designed to meet stringent security standards, we did not find much evidence of that in our testing. In fact, several key flaws in its apps would make us hesitant to recommend it:
- It is too easy to bypass Google Workspace security controls
The controls to prevent editing, printing, copy-pasting, and sharing are enforced by JavaScript, which is executed partly in the user’s browser. Bypassing them to create unprotected copies only takes a few seconds in the browser’s developer panel. We cover this in our blog on Is Google Docs secure? - Your documents are only as secure as your user accounts
Users are bombarded with social engineering, phishing, and session hijacking attacks that may compromise their accounts. Additionally, malicious internal users may intentionally give away their login details and share 2-step verification codes. - DLP and Context Aware Access restrictions only go so far
If there are weaknesses in other parts of the system that enable users to bypass rules then DLP and context aware access restrictions won’t be able to address that. - Link-based sharing is a terrible idea
It is commonly used in malware attacks and is why we don’t recommend link sharing in Google Drive or sharing a PDF as a link. In addition, some admins fail to disable the “anyone with the link can view” option in documents. This frequently leads to links accidentally or intentionally being shared with unauthorized users.
%22%20transform%3D%22translate(1%201)%20scale(2.1836)%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20fill%3D%22%23b3abdc%22%20cx%3D%22237%22%20cy%3D%22170%22%20rx%3D%2257%22%20ry%3D%2247%22%2F%3E%3Cpath%20fill%3D%22%23ab99ff%22%20d%3D%22M208%20157h48v22h-48z%22%2F%3E%3Cpath%20fill%3D%22%23cccdcb%22%20d%3D%22M33.7%2020.5l30%202-2.9%2015.7L32%2048.5z%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
- Your document security is tied to Google’s server security
Your documents are stored on a server that you do not have control over and cannot audit. Though Google generally has a good track record, it has still had several major incidents.
%22%20transform%3D%22translate(1.3%201.3)%20scale(2.53906)%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20fill%3D%22%23525252%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-32.6316%204.919%20-18.71495%20-124.15097%20241.7%2076.3)%22%2F%3E%3Cellipse%20fill%3D%22%23d9d9d9%22%20cx%3D%2247%22%20cy%3D%22114%22%20rx%3D%22126%22%20ry%3D%22145%22%2F%3E%3Cellipse%20fill%3D%22%23f7f7f7%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-44.89729%20-45.55144%2035.11039%20-34.60618%208.7%20123)%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
- Google Workspace has an active vulnerability
There is a design flaw in Workspace’s Domain-Wide Delegation that could expose customers to unauthorized access and privilege escalation. According to Hunters’ Team Axon, this could result in the unauthorized access of emails, extraction of data from Google Drive (i.e., all your workspace files), and other illicit activities across an entire targeted Workspace domain. Google has yet to fix this vulnerability (as of January 2024), and claims that it “does not identify an underlying security issue”. There are proof-of-concept tools available on the open web to exploit it.
%27%20fill-opacity%3D%27.5%27%3E%3Cellipse%20fill%3D%22%23cfcfcf%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(64.06908%20135.89144%20-236.5092%20111.50759%2093.7%2037)%22%2F%3E%3Cellipse%20fill%3D%22%23d0d0d0%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-145.01083%2030.54914%20-17.27286%20-81.9909%20340.6%20317)%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(33.80983%2067.22336%20-489.435%20246.16016%20404.2%20115.3)%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
- Security reports and investigation tools
While these are a great asset to have, and enable organizations to quickly find and spot security weaknesses, they cannot warn admins of issues that are part of the makeup of the system. For example, they won’t be able to report that users have turned off JavaScript to bypass editing restrictions or made use of a vulnerability to get around DLP rules.
 Google Workspace privacy: is it all it’s cracked up to be?
Google Workspace privacy: is it all it’s cracked up to be?

Google makes a lot of noise about protecting privacy in Google Workspace – probably because it’s the biggest ad provider in the world and everybody knows user data is its lifeblood.
However, Google’s actions speak louder than its marketing material. In 2022, it changed some of its Web & App Activity controls for Workspace users and took advantage of the change to enable tracking features that users had previously opted out of. This also made it so that admins cannot control search privacy settings – only individual users. A clear downgrade in privacy.
Some organizations complain that Google’s privacy controls are intentionally misleading and unintuitive for confidentiality purposes. Indeed, it has been the subject of several lawsuits for precisely this accusation. Privacy settings are obfuscated by several categories that don’t always make logical sense, and Google often bundles settings together rather than allowing individual control.
Ultimately, you have to decide whether to trust a company that makes almost 80% of its revenue from data-driven ads with your privacy. This might be a risk worth taking for personal accounts, but businesses sharing sensitive and confidential documents might want to think twice.
 What are the alternatives to Google Workspace security?
What are the alternatives to Google Workspace security?

Google Workspace security is barely worth the (digital) paper that it’s written on. Though its self-managed encryption keys are a good addition, poorly enforced document controls fail to prevent sharing regardless of encryption in both email attachments and regular documents. Organizations that regularly process confidential and sensitive information will want to look elsewhere if they are serious about preventing leaks and need to share documents securely.
 Microsoft 365 vs Google Workspace security
Microsoft 365 vs Google Workspace security

The natural inclination is to go with Workspace’s main competitor, Microsoft 365. Business Premium subscriptions include Azure Information Protection (a component of Azure Rights Management). Admittedly, AIP controls aren’t quite as easy to bypass as Google Docs’, but there are still major flaws. As covered in how secure is Azure Rights Management, users with the right to view a document can strip its copying, editing, printing, and sharing controls using a freely available program. Seemingly, you are introducing a lot more complexity for a minor upgrade in protection.
A DRM solution may be the best choice if you’re just looking for simple but effective document security. These can offer strong per-document encryption in specific file formats and enforce controls in dedicated viewer apps so they cannot be easily bypassed or removed.
 Locklizard PDF DRM vs Google Workspace security
Locklizard PDF DRM vs Google Workspace security

Locklizard Safeguard is DRM software that protects PDFs through a combination of AES 256-bit encryption, a secure viewer application, and document controls.
Here’s how it works:
- You export or save as a PDF from the application of your choice and encrypt it with printing, editing, screenshot, saving, and copy-paste controls using the Safeguard Writer application.
- Optionally, you can add dynamic watermarks to identify whichever user opens/prints the document.
- You then choose which users want to have access via your admin portal. These users are sent an email with a license file, which can be registered to one device by default. Once they install the license, decryption keys are securely transmitted to an encrypted keystore which users cannot access or share.
- You provide the encrypted PDF to users via any method (Google Drive, Workspace email, message, etc.). The security of the sharing method is not as important since the individual documents are encrypted, and only authorized users can open them.
- Your documents receive strong protection against unauthorized sharing and modification. Sharing the PDF file with others is useless (as they will be unable to open it), keys are locked to devices, and document controls ensure users can’t make unprotected copies or edit them.
For additional security, admins can lock documents to specific locations and IP addresses (for example, the office). They can also expire documents based on several criteria and manually revoke both documents and users at any point. Finally, optional document tracking lets you see who viewed and printed what documents.
Follow this step-by-step process – protect a PDF from being copied – to apply security to your files.
 Final verdict – is Google Workspace secure?
Final verdict – is Google Workspace secure?

Google Workspace security might be okay for day-to-day use and Google Meet calls, but we certainly wouldn’t trust it for sensitive data and confidential information. A combination of poor document controls, cloud hosting security issues, and open unauthorized access and privilege escalation vulnerabilities leaves too many ways for information to leak.
If you need protection of confidential and sensitive documents, it’s best to use DRM software such as Locklizard Safeguard. This offers a simple way to prevent unauthorized sharing and misuse from internal and external users.
Take a 10-day free trial of our DRM software to see how it compares to Google Workspace security for the protection and sharing of confidential documents.
 FAQs
FAQs

What is Google Workspace?
Google Workspace is a suite of cloud-based productivity and collaboration tools such as Gmail, Docs, Drive, Meet, Sheets, Slides, Forms, Calendar, Sites, etc. that enable businesses and private users to create, store, manage and share files, emails and data.
How do I make my Google Workspace secure?
You can better secure Google Workspace by securing sensitive and confidential documents with a DRM solution before you upload them. This will prevent unauthorized sharing and modification both in Google Drive and for email attachments.
How much does Google Workspace cost?
Workspace has four plans: business starter at $6/user/month, standard at $12, and business plus at $18. The business plus plan is required for enhanced security, while the enterprise plan, which has an undisclosed price, offers the best security.
What are Google Workspace’s security features?
Workspace offers context-aware account access, DLP and IRM tools, email spam, phishing and malware defenses, AI classification for Drive files, and encryption of data in transit and at rest.
What are the Google Workspace security best practices?
Google has a long list of best practices that you can read here. Some key points include: strong protection on admin accounts, MFA for additional login security, good password hygiene, client-side encryption, turning off sharing options, data loss protection, email encryption, etc.
What’s the difference between Google Workspace and Google Cloud?
Google Cloud is the name for the large suite of cloud products Google offers, including Google servers, cloud storage, AI tuning, load balancing, Workspace, and more. So, Workspace falls under the Cloud offering, but Cloud is much more than just Workspace.
Is Google Login or sign in secure?
Google login or sign in is as secure as the password you use to protect the account, so a strong password is essential. Organizations can apply password rules, add two factor authentication (2FA) and Single Sign On (SSO) to boost security and help prevent social engineering and phishing attacks.
Does Lockizard protect sheets, docs, and slides?
Locklizard can protect documents from any application that can export as PDF, including Google Slides, Docs, and Sheets. We do not support protection in native Workspace formats however, only as PDF.

 Google Workspace security
Google Workspace security Google Workspace & encryption of data
Google Workspace & encryption of data Does DLP and Context-Aware Access prevent data loss?
Does DLP and Context-Aware Access prevent data loss? How secure is Google document cloud?
How secure is Google document cloud?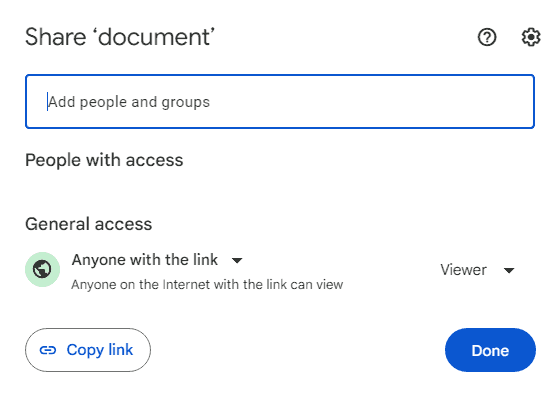

 Google Workspace privacy: is it all it’s cracked up to be?
Google Workspace privacy: is it all it’s cracked up to be? What are the alternatives to Google Workspace security?
What are the alternatives to Google Workspace security? Microsoft 365 vs Google Workspace security
Microsoft 365 vs Google Workspace security Locklizard PDF DRM vs Google Workspace security
Locklizard PDF DRM vs Google Workspace security Final verdict – is Google Workspace secure?
Final verdict – is Google Workspace secure? FAQs
FAQs
