Enterprise Digital Rights Management or Enterprise DRM (EDRM)
Enterprise Rights Management (ERM) or Enterprise DRM

 What is ERM or enterprise DRM?
What is ERM or enterprise DRM?
Enterprise Rights Management solutions persistently control access to and use of information, ensuring your organization’s intellectual property is used appropriately by employees throughout its lifecycle.
You may think this sounds similar to information rights management (IRM) and it is. The information security industry uses similar terms for the protection of information or data both inside and outside the enterprise.
ERM or enterprise DRM, is rights management applied inside of the enterprise, rather than outside. While ERM can also be used to control document use or digital assets with external users or third parties such as customers and business partners, it is better suited for the protection of digital data within the enterprise. This is because EDRM systems are usually complex, requiring users to operate the same software (or use weak browser alternatives where security cannot be fully enforced), and policy rules can easily be wrongly configured so they are not effective.
Of course, some of the ERM controls will appear very similar to those you would use in digital rights management – stopping printing, stopping editing, or saving. But other controls – preventing copying or forwarding – are more closely related to traditional internal control mechanisms, such as access control systems:
- Digital rights management controls, whilst in other respects being identical to enterprise rights management (ERM) controls, have been built to operate outside the reach of an IT administrator rather than as part of internal access management controls.
- Enterprise rights management (ERM) builds on the traditional access rights of read, write, append, delete, and execute. They can additionally prevent copying by forbidding the writing of files to unsanctioned destinations and blocking sending as an email attachment.
Enterprise DRM solutions use a data-centric security approach, protecting documents at the data level rather than protecting networks, servers or applications and relying on those applications to enforce security or policy rules (e.g. a DLP or Data Loss Prevention system). They ensure documents containing sensitive business data are encrypted in storage and transit, and that they can only be accessed with the correct authorization and used in an authorized manner.
 How is ERM, EDRM or Enterprise DRM implemented?
How is ERM, EDRM or Enterprise DRM implemented?
While EDRM systems differ slightly in how they work, they all follow a similar process:
- Documents are protected with encryption and DRM restrictions are added to prevent copying, editing, printing, etc. Protection is applied using an application and may be automated using policies and/or APIs.
- Protected documents are made available on a network share, SharePoint, etc.
- User accounts are added to a license server and admins determine what documents they can access.
- The license server emails users their access information.
Users install a rendering application on their device and activate their license file. Once activated they can then view documents they are allowed to access.
 Why use Enterprise Rights Management (ERM)?
Why use Enterprise Rights Management (ERM)?
Most data security compromises happen within the enterprise. Employees may take data with them on USB sticks, on a laptop, or upload it to the cloud even with a DLP system actively monitoring critical data or the network perimeter. Sensitive documents or data could be exposed on systems unintentionally due to poor security measures, or maliciously by ex-employees or those with a grudge.
They say that data is an organization’s most precious asset, and with good reason – exposure or theft of certain sensitive or confidential documents may affect both a company’s share value and its bottom line. Preventing the above situations should be a top priority, and for this to happen, the protection must remain with the document no matter where it is stored. ERM aims to do exactly this – making sure either information does not leave the enterprise, or if it does, that it can only be used by certain individuals with tight controls governing use.
A good enterprise digital rights management system will enable organizations to control which users have access to documents, how they can be used, how long they can be used, and the locations users can access them from. It should enable administrators to instantly revoke documents and users, have documents that automatically expire (so retention periods can be enforced), and not rely on insecure and unmanageable technology such as password protection – see why you should not password protect documents.
Enterprise DRM (EDRM) solutions

There are a few companies that operate in the EDRM or enterprise DRM space, but here we cover the two most well-known ones and their security flaws.
 Microsoft Enterprise Rights Management
Microsoft Enterprise Rights Management
Microsoft’s cloud-based Azure Rights Management Services (not to be confused with its on-premises Azure Directory Rights Management Services) is an ERM for Microsoft Office documents. It is a policy-based system that requires a moderate workload to set up and maintain, though it does support a wide variety of file formats. Still, the big question is: does it actually work?
Well, the title of the paper How to Break Microsoft Rights Management Services may give you a hint. As we have outlined in more detail in our blog on Azure Rights Management, those with view-only access to an Azure Rights management document can gain full document control without much difficulty. Shortly after publishing the paper above, the researchers released the tools to remove ARM controls through a simple .exe file. These attacks reportedly still work today despite being published seven years ago, which demonstrates that there is no easy fix. Microsoft points out that this is a limitation of its policy-based models, as the controls to prevent printing of modification are not backed by cryptography.
There are other problems with Azure Rights Management. The management of security policies and classification will likely require full-time employees. Additionally, external sharing is a hassle that will increase the load on your IT department. All of this makes its $5 per user/month cost (for those without a Microsoft 365 Enterprise subscription) difficult to justify.
 Adobe Rights Management
Adobe Rights Management
Adobe’s primary rights management offering is now Adobe Experience Manager. Conveniently, it allows organizations to protect both PDF and Microsoft Office files, with the ability to restrict who can access digital content as well as whether they can edit, print, or copy from a file.
Unfortunately, it’s hard to call Adobe’s Microsoft Office support anything other than a gimmick, as outlined in detail in our blog on Adobe Experience Manager. The Office 365 protection is delivered via a plugin, which makes it unreliable and insecure. Additionally, it relies on the security built into Word, which is deeply flawed. Using it with sensitive information or confidential data is not a good idea.
The PDF protection it offers is better, but still far from perfect. Though it takes the right approach by using a combination of a license server and encryption keys, authentication is still based on Adobe account credentials. All an authorized user needs to do to grant access to Adobe-protected PDF files is to share their login details with others. Add to that poor support for offline functionality, no screenshot prevention, and complex policy rules to setup and maintain, and it also becomes a hard sell. And that is even before you consider the per user costs.
 Locklizard Enterprise Digital Rights Management
Locklizard Enterprise Digital Rights Management
Locklizard Safeguard offers comprehensive rights management controls for PDF files that work regardless of whether the document is inside or outside the enterprise.

Safeguard’s default enterprise digital rights management protection:
- Stops document sharing – locks documents to authorized devices so they cannot be shared with others.
- Stops users editing, copying and pasting, and screenshotting content.
- There are no passwords for users to enter, manage, or remove.
- Persistent protection of documents regardless of location with US Gov strength AES encryption and DRM controls.
Unlike competing solutions, Locklizard Safeguard controls are simple to manage and cannot be removed. Document content is only ever decrypted in memory and dynamic watermarks identify any user who tries to take a picture of the screen with a mobile device.
 | Protecting PDF documents with Enterprise Digital Rights Management software |

How to add rights management to a PDF document with Locklizard
Adding rights management controls in Safeguard Enterprise Secure PDF Writer is simple:
- Right-click the PDF file and press “Make Secure PDF”
%22%20transform%3D%22translate(1%201)%20scale(2.11719)%22%20fill%3D%22%23fff%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20cx%3D%22224%22%20cy%3D%221%22%20rx%3D%22133%22%20ry%3D%2229%22%2F%3E%3Cellipse%20cx%3D%22244%22%20rx%3D%22138%22%20ry%3D%2230%22%2F%3E%3Cellipse%20cx%3D%2224%22%20cy%3D%223%22%20rx%3D%2229%22%20ry%3D%2216%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
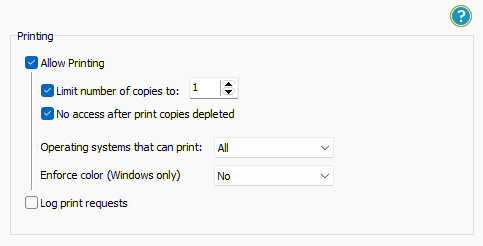
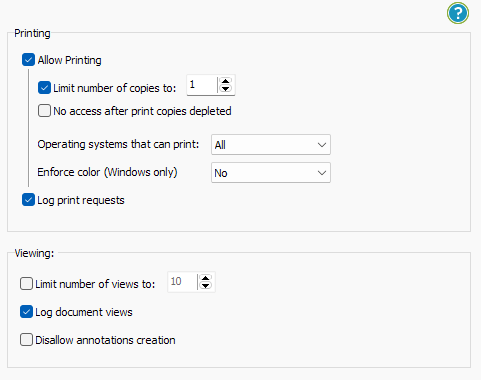
- Stop printing, allow printing, or limit the number of prints.
%27%20fill-opacity%3D%27.5%27%3E%3Cellipse%20fill%3D%22%23cecece%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(23.22648%20-85.21986%20126.36312%2034.43999%2066.5%20118)%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22rotate(162.5%20164.1%20101.5)%20scale(148.75926%20255.51164)%22%2F%3E%3Cpath%20fill%3D%22%23cdcdcd%22%20fill-opacity%3D%22.5%22%20d%3D%22M50%20206.6h79.2v39.6H50z%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
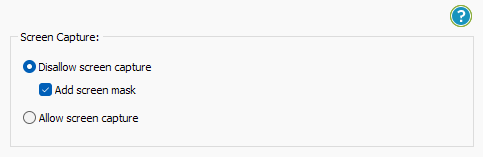
- Stop screen grabbing (even from remote connections).
%22%20transform%3D%22translate(1%201)%20scale(1.88672)%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20fill%3D%22%23cacaca%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22rotate(76.5%20-20%2045)%20scale(59.50181%2038.8711)%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20cx%3D%22161%22%20cy%3D%2259%22%20rx%3D%2295%22%20ry%3D%2295%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20cx%3D%22157%22%20cy%3D%2246%22%20rx%3D%2290%22%20ry%3D%2290%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
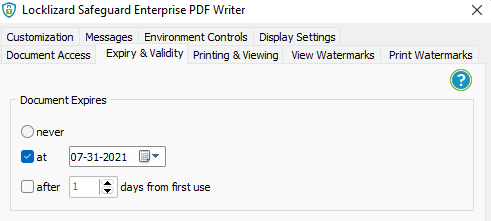
- Enable document expiry. Automatically expire documents on a specific date, after a number of views, after a number of prints, or after a number of days from opening.
%22%20transform%3D%22translate(1%201)%20scale(1.91797)%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20fill%3D%22%23fff%22%20cx%3D%22176%22%20cy%3D%2285%22%20rx%3D%2295%22%20ry%3D%2252%22%2F%3E%3Cpath%20fill%3D%22%23d5d5d5%22%20d%3D%22M180-16l-192%205-4%20141z%22%2F%3E%3Cpath%20fill%3D%22%23fff%22%20d%3D%22M37%2045l234%204-139%2081z%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
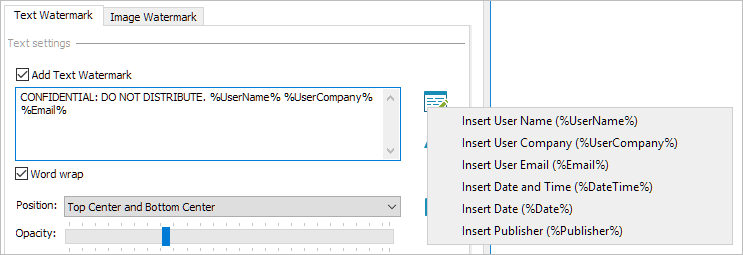
- Add dynamic watermarks to viewed and or printed pages. Dynamic variables replace actual user and system data when the document is viewed/printed so you only have to protect the document once for all users.
%22%20transform%3D%22translate(1.5%201.5)%20scale(2.90234)%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20fill%3D%22%23d2d2d2%22%20cx%3D%22186%22%20cy%3D%2275%22%20rx%3D%2253%22%20ry%3D%2253%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(67.88003%207.85399%20-5.26178%2045.47626%2088%2014.2)%22%2F%3E%3Cellipse%20fill%3D%22%23d1d1d1%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-4.4371%2032.17735%20-55.1362%20-7.60302%2035.2%2077.4)%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
- Track document views and prints.
%22%20transform%3D%22translate(1%201)%20scale(1.8789)%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20fill%3D%22%23cfcfcf%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-57.2312%20-2.47171%204.9529%20-114.68172%2013.8%20113.5)%22%2F%3E%3Cellipse%20fill%3D%22%23d5d5d5%22%20cx%3D%2269%22%20cy%3D%2267%22%20rx%3D%2237%22%20ry%3D%2237%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(87.81558%2032.48397%20-69.10335%20186.81063%20181.8%20124.3)%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
- Once you have chosen your DRM restrictions, press the “Publish” button at the bottom of the window.
%27%20fill-opacity%3D%27.5%27%3E%3Cellipse%20fill%3D%22%23d1d1d1%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22rotate(168.9%20164.5%20104.6)%20scale(494.0625%2062.51262)%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(393.1765%20-23.13948%204.63058%2078.68087%20199.7%2040)%22%2F%3E%3Cellipse%20fill%3D%22%23d5d5d5%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-82.79938%20-45.81606%2023.04825%20-41.6531%2025.1%20159.3)%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
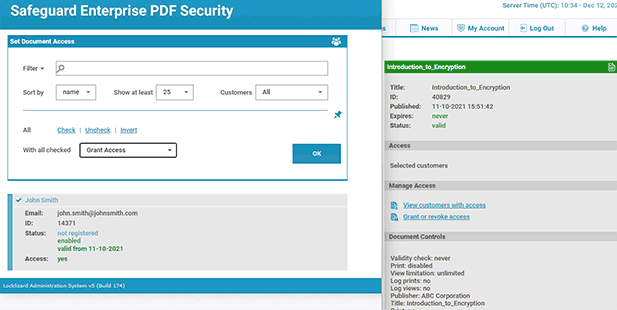
Your protected PDF file will output to its source folder in the .pdc format and you can safely share it knowing that nobody can access it without a valid license. - Add a user account and send them their license via the Safeguard admin portal.
%22%20transform%3D%22translate(1.2%201.2)%20scale(2.41016)%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20fill%3D%22%2357cae7%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(90.48772%20.46606%20-.09282%2018.0206%2065.8%207.7)%22%2F%3E%3Cellipse%20fill%3D%22%23eae2e1%22%20cx%3D%22125%22%20cy%3D%2281%22%20rx%3D%22255%22%20ry%3D%2253%22%2F%3E%3Cellipse%20fill%3D%22%239df1bc%22%20cx%3D%2252%22%20cy%3D%2221%22%20rx%3D%2292%22%20ry%3D%226%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
With the PDF published, you’ll need to send your recipients the encrypted .pdc file, alongside a download link for the secure PDF reader application and a valid license. The simplest way of doing so is by ticking “Email license” when you add a new user. See how to add a new user and grant them document access.
Safeguard Secure PDF viewer prevents editing, copy and paste, Save As, and screenshots. If printing is allowed it prevents printing to file drivers, and you can add watermarks to printed copies to make re-scanning or using OCR tools difficult.
Remotely manage user and document access
In the Safeguard Enterprise Admin System, you can:
- Assign document access.
- Change document expiry dates for individual users, groups, or documents. The same document can be set to expire at different times for different users.
- Lock use to specific locations (e.g. the office only or a country) to prevent users opening documents outside of authorized areas.
- Revoke documents and users at any time regardless of where they reside.
- See tracking analytics – when documents have been viewed and printed, by who, from where, and when.

 Download Enterprise Rights Management Software
Download Enterprise Rights Management Software

The best enterprise rights management for PDF files
Download enterprise rights management software for PDF documents – DRM Download.
Safeguard Enterprise PDF Security is an enterprise level PDF DRM software with document copy protection, tracking, location, and print controls. Use our PDF enterprise rights management security to protect sensitive PDF documents from unauthorized use and misuse regardless of where they are located.
See our customer testimonials or read our case studies to see why thousands of organizations use Locklizard PDF Enterprise Rights Management software to protect their documents from unauthorized access and misuse.









 Free Trial & Demo
Free Trial & Demo What is ERM or enterprise DRM?
What is ERM or enterprise DRM? How is ERM, EDRM or Enterprise DRM implemented?
How is ERM, EDRM or Enterprise DRM implemented? Why use Enterprise Rights Management (ERM)?
Why use Enterprise Rights Management (ERM)? Microsoft Enterprise Rights Management
Microsoft Enterprise Rights Management Adobe Rights Management
Adobe Rights Management Locklizard Enterprise Digital Rights Management
Locklizard Enterprise Digital Rights Management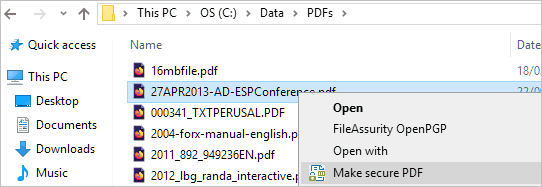
 Download Enterprise Rights Management Software
Download Enterprise Rights Management Software FAQs
FAQs















